In a field where every contractor releases an annual infosec report, BakerHostetler's is unique. BakerHostetler, a law firm with a massive data and privacy presence, compiles data from their client's experiences to offer a rare lawyer's perspective on cyber statistics. No amount of vendor telemetry can provide some of the information they have, including outcome statistics from ransomware negotiations or the frequency of litigation.
While the firm's stats are somewhat self-selecting — they refer to outcomes for companies savvy enough to pursue proper legal guidance — they are the closest look we have to results typically hidden behind boardroom doors.
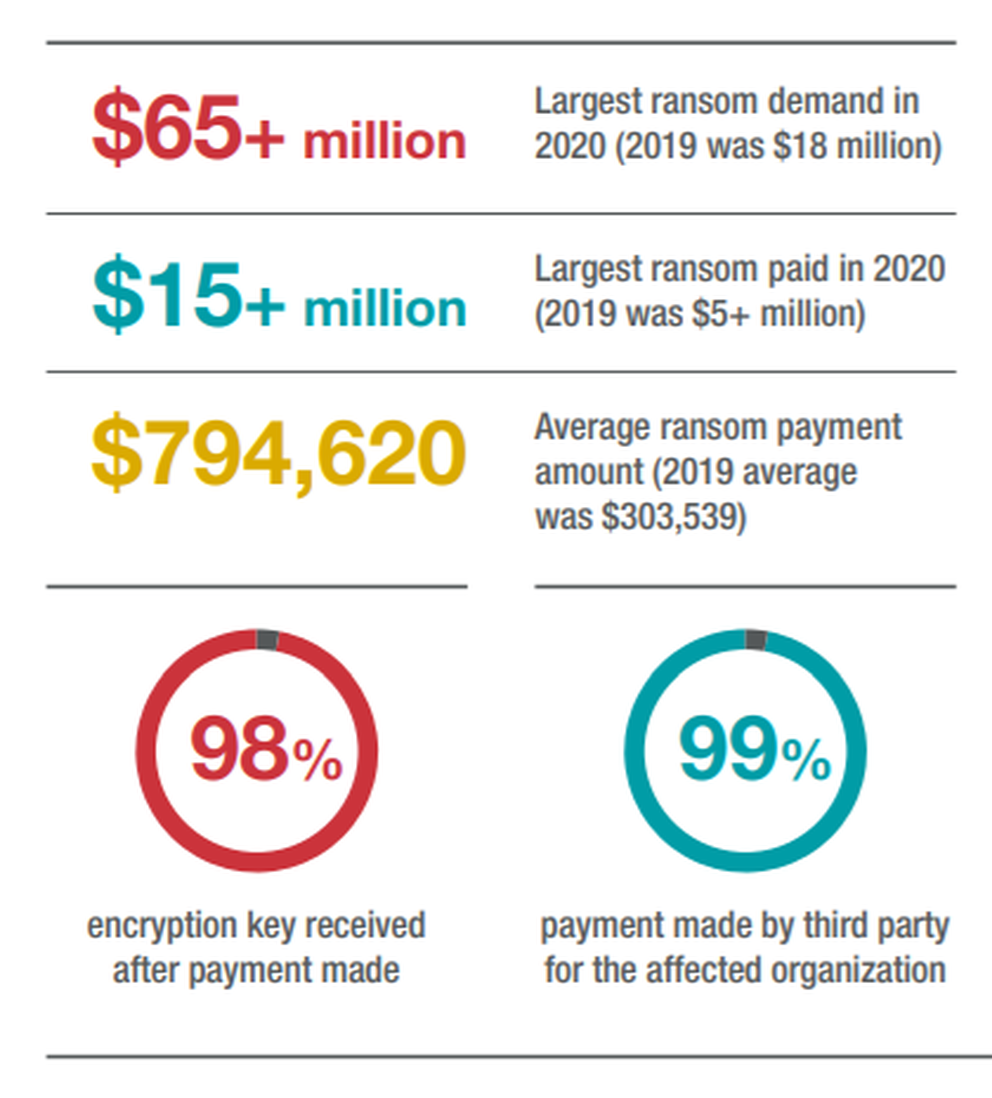
For example, contrary to common rhetoric, which often portrays paying ransom as a risky proposition inviting criminals to take the money and run, firm clients who paid ransoms received an encryption key 98 percent of the time.
SC spoke to Craig Hoffman, partner at BakerHostetler and the main editor of the report, about the real outcomes from breaches.
A good place to start would be why a law firm would release cybersecurity statistics. What do people get here that they can't get from security vendors?
Hoffman: If you look at forensic firms, they have good annual reports. The Mandiant M-Trends report is one I've followed for a long time. It has great details, such as Mitre attack chains and dwell time until investigation. But it won't have the other parts of a breach: How long did it take the company they investigated to send a notice to individuals? Or, did they get sued after they provided that notice? Since we are advising a company and bringing in different types of experts to help us give advice, we see data from the whole picture and try to use that here.
Mandiant has reported on the forensics, CoveWare has great data releases quarterly on ransom payments. Those are based on a single source. Ours is based on seeing incidents across multiple forensic firms, multiple payment facilitation, and negotiators. If you look at the breakdown of companies, it's across all industries and revenue size.
How different is the data, which you have a window on, than other researchers get to see?
One of the biggest disparities lies in the overall impact. If you look at others who find a statistic for the average cost of a data breach per record, that number, whether it's $200 or $300 per record, has no good, practical use. You would say, "Okay, we have a database of 100,000 customers. So that means if we have an incident we're going to have billions of dollars in liability." That's just not what actually happens.
If you take the components of our report, you get a more realistic projection of what your first-party and third-party costs and liabilities are. You can say, "Alright, I have an incident. What is the likelihood that I actually get sued? Should I factor in litigation costs into my expectation of what my likely costs are?" Last year, our clients provided notice 543 times. Out of those, our clients were only sued 20 times. So if you're saying, I need to figure out how much and how likely it is I will have litigation, unless it's a scenario that meets a couple of criteria, it's unlikely you'll be sued. You don't need to factor the same liabilities into your cost.
One of the statistics that jumps out right away is that nearly all of your clients — 98 percent — who paid a ransom got their data back. That goes against a common narrative in the industry and the government that people who pay ransom run a significant risk of being cheated by a criminal.
I saw the recent task force and their long list of recommendations. All of that is great. I hope they're tremendously successful in shutting down these ransomware threat groups. Until that happens, we still have organizations who are affected by this and need help.
With the Treasury alert that came out in October of 2020, I suspect the government would prefer that companies not pay the ransom. But you just don't have a lot of tools to make that happen when companies are in a position of either incurring a lot of lost income and impacting their relationships with clients and stakeholders or making a payment to tremendously lessen that impact.
And it's not illegal to make that payment. They make a business decision. There are only a few groups on [the sanctioned list], or affiliated with organizations that are on there, or operate out of countries on the sanctions list. For most of the ransomware actors that are active right now, there is no indication that they are in a country or affiliated with a group that are. There should be an ability to have confidence that you can make a payment without violating laws.
As you note in your statistics, almost all of your clients use a third-party negotiator in payments. Does that affect the success rate?
They go hand-in-hand. Yes, you're dealing with a criminal. If you don't know who they are, how can you have any confidence that if you send money to them they will live up to their end of the bargain? In reality, because you are almost always using a third party to do the negotiations, they can identify who that group is and identify their track record.
You can see how many times they've negotiated with the group before, and what their track record is. When you reached an agreement to pay, did they give you an encryption tool or try to re-extort you? For groups that do re-extortion, or who don't provide an encryption tool that works, ransomware only works a few times for them. It becomes known who they are, and people don't negotiate with them.
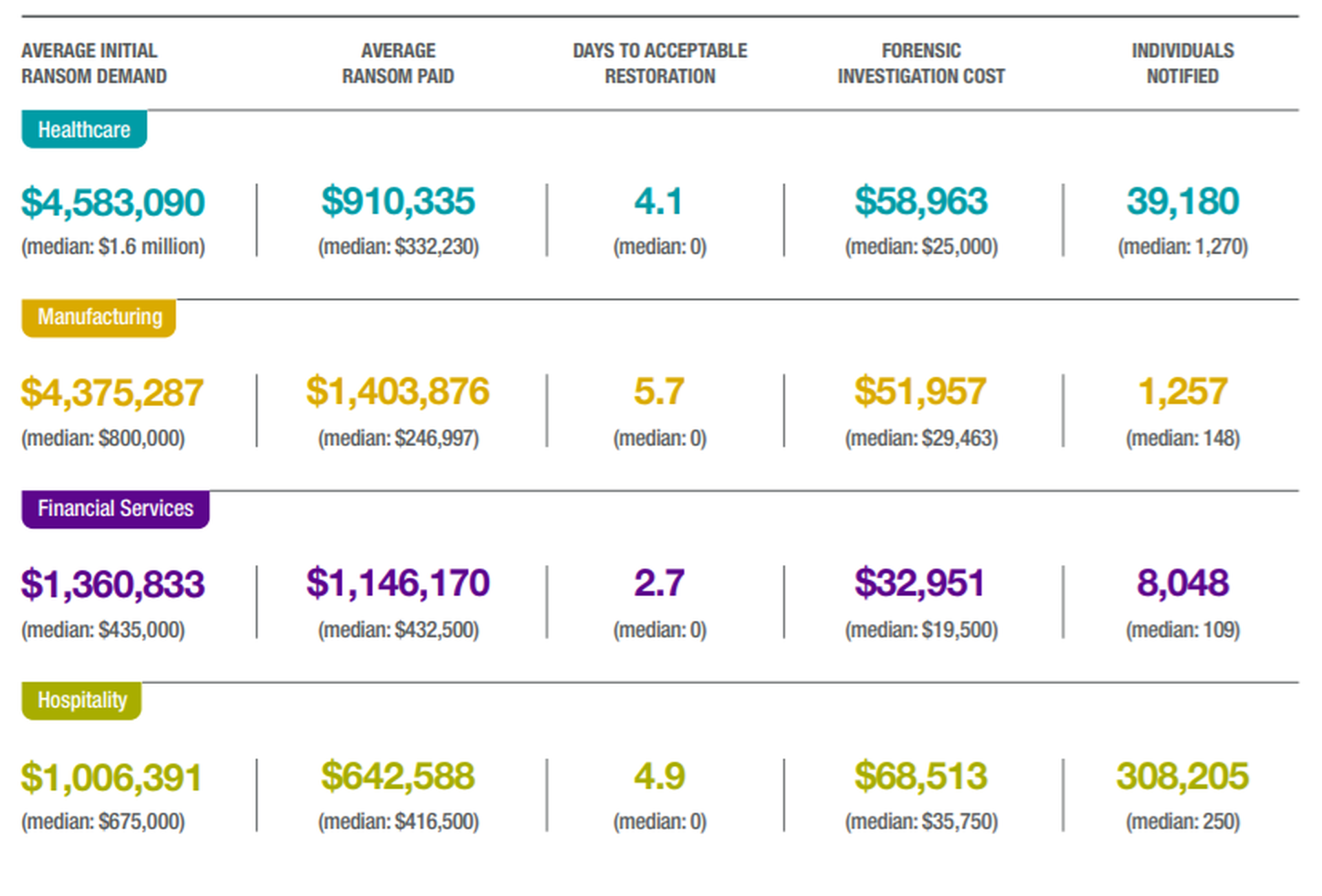
When clients come to you, do they already have a sense of the role negotiation plays? Your stats on negotiated ransoms are substantially lower than the demands. In healthcare, the median final cost was around 20% of the asking cost. How are people prepared and how should they be prepared?
People have a lot of questions at the outset. What does this mean, we're dealing with a criminal? You mean, we can actually negotiate with them? What are the strategies for negotiating with them? The biggest factor in getting a reduction from the initial demand is time. How fast do you need to obtain the decryption tool to restore operations? The longer you can hold out, the more you can drive down the cost.
You mentioned that only a small number of organizations that meet certain criteria tend to get sued after a breach. What are those criteria?
If you're an organization preparing to do notice, you want to know if it's likely that you're going to be sued. Are you doing notice to 10,000 or more people, and does it involve their social security number? If it does, there's a decent chance, especially with larger organizations. If it's an incident that comes fairly reported on, there's a pretty good chance to get sued. If the incident was a breach of an employee's email account where someone could view data, and you're going to notify 1000 people, after the notice is sent, there is a pretty good chance of not being sued.
Finally, the report deals with a broad range of companies that are either large or prepared enough to come ask for help. How will things be different for smaller firms or ones that are less prepared?
At companies that are small and up to medium, and even at ones who are large, there is often no designated person whose job it is to address the overall impact of a security incident. Often, it's not someone's job to go find names and addresses to build a notification. When companies are already lean, it's hard to have an employee detect and investigate, determine notice obligations, and send them out.
Organizations have to pull together and it's really taxing. It takes a big toll on the core people who pull together to do it.




