An ongoing ransomware campaign hides its payload in an uncommon way by targeting popular open-source packages that typically receive nearly 15 million installations per week, according to new findings by Checkmarx and Phylum.
In a blog post, Checkmarx researchers said the campaign uses a form of typosquatting to target the popular “requests” package on Pypi and the “discord.js” package on NPM, and includes embedded ransomware. When executed, the ransomware encrypts files on the victim’s computer and demands payment of $100 in cryptocurrency to unlock them.
Unlike most open-source attacks where malicious packages are being executed upon installation, Alik Koldobsky, security researcher at Checkmarx, told SC Media that the payload is hidden in multiple strategic locations and only executes when the victims use the actual functions of the packages, which makes the campaign hard to detect by many security scanners.
The malware payload supports multiple operating systems, allowing the campaign to target a wider audience. In addition, attackers named the ransomware messages and infrastructure after the U.S. Central Intelligence Agency.
A detailed attribution has yet to be done, but researchers discovered clues through further investigation that imply the attacker is Russian — the Telegram user account associated with the attack has a Russian phone number, and the attacker interacts with researchers directly in Russian.
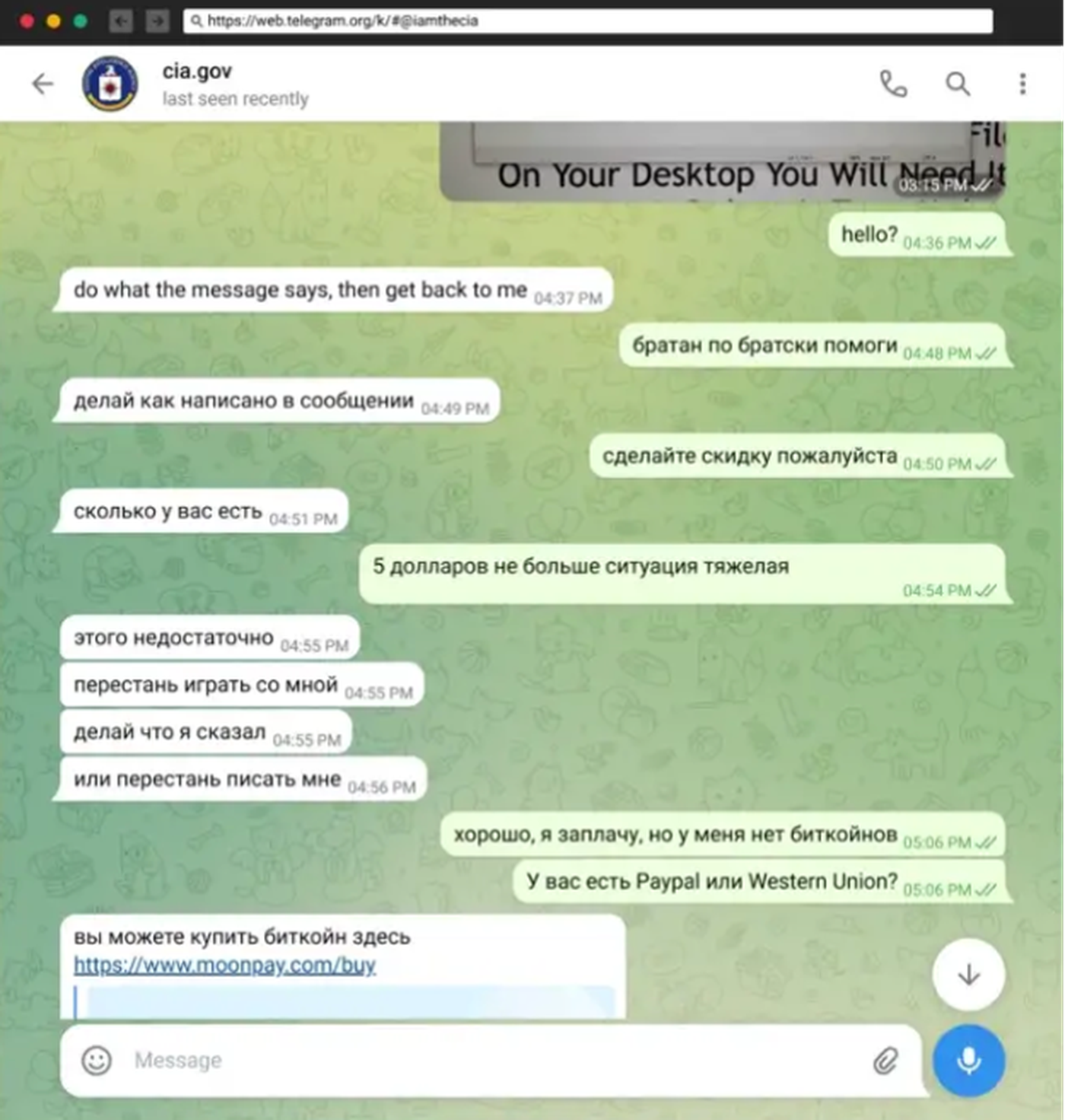
Even after Checkmarx reported the attacks, the offender's account is still able to publish potentially malicious packages on NPM and PyPi, where software supply chain attacks are rampant. Researchers say they will continue to monitor for any new activity.
Koldobsky warned that there would be more attacks from the same actors as well as copycats, simply because the method is easy and impactful.
Besides the campaign’s uncommon way of hiding its payload, it is rare yet not unknown for ransomware attackers to use open source as a delivery system, said Mike Parkin, senior technical engineer at Vulcan Cyber. In August, Sonatype discovered multiple malicious Python packages that embedded ransomware.
Kristen Bell, director of application security at GuidePoint Security, said she expects a rise in ransomware within the open source in the upcoming months.
“Both ransomware and open-source attacks are on the rise, so it is not surprising to see them being combined,” Bell told SC Media in an email.