Researchers at CrowdStrike have discovered a new hacking campaign that targets cloud infrastructure around the world in service of a cryptojacking scheme.
The campaign – dubbed "Kiss-A-Dog" – dates back to at least September, when a CrowdStrike honeypot first began picking up signs of attacks targeting vulnerable Docker and Kubernetes instances. The name given to the campaign derives from the domain name used by attackers to fetch the Python-coded malware payload: kiss[.]a-dog[.]top.
It leverages multiple command and control servers to escape containerized environments and gain root privileges, while using kernel and user rootkits for obfuscation, creating backdoors, lateral movement and persistence. The attackers also demonstrated the ability to detect and uninstall third-party cloud monitoring services.
Once they gained a foothold within a compromised container, the threat actors sought to compile network scanning tools to look for additional cloud servers running Docker and Kubernetes.
And there are plenty to find. According to Shodan, there are more than 68,000 vulnerable Kubernetes instances (16,915 in the U.S.) and 13,000 Docker instances (2,320 in the U.S.) exposed to the internet globally.
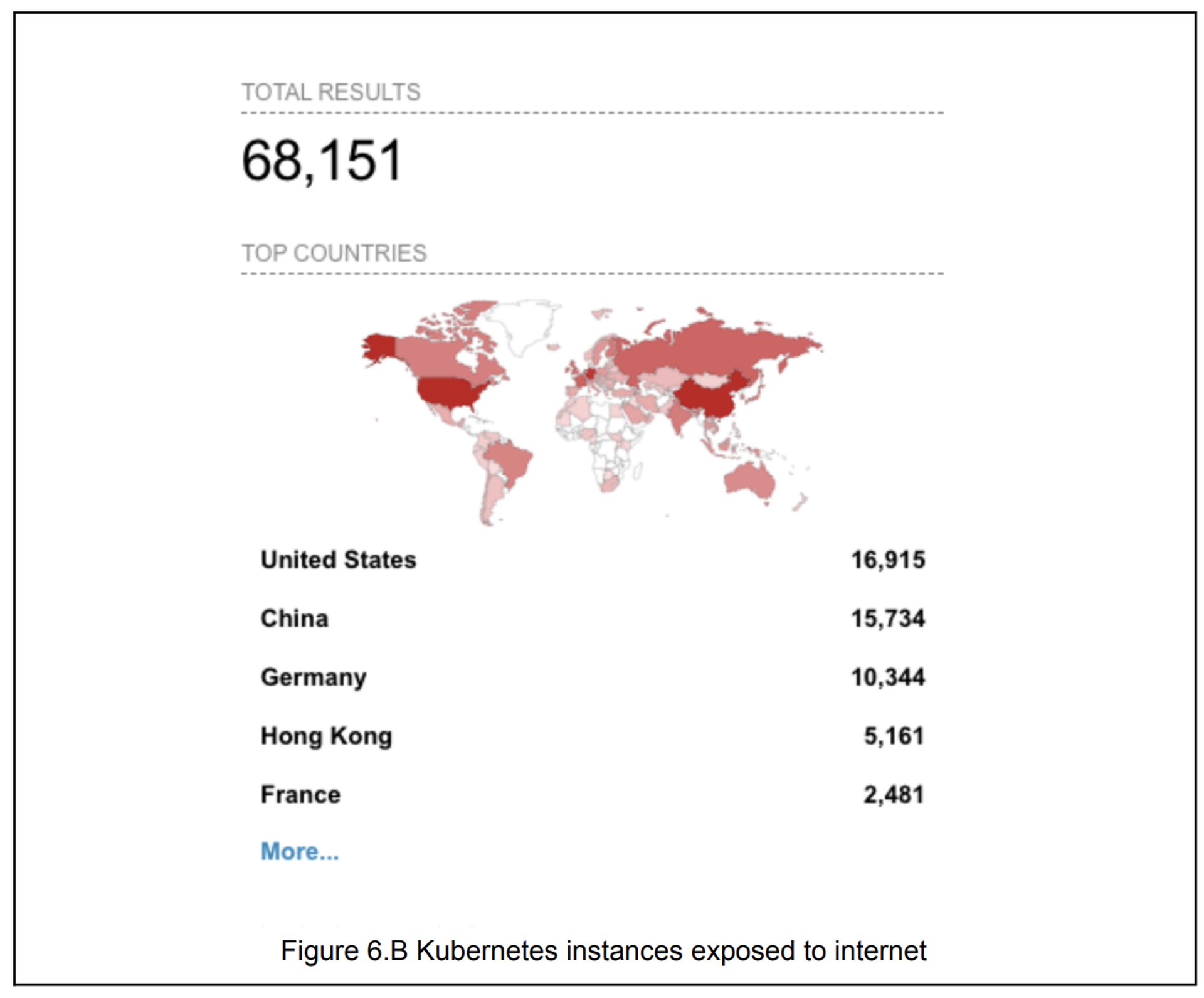
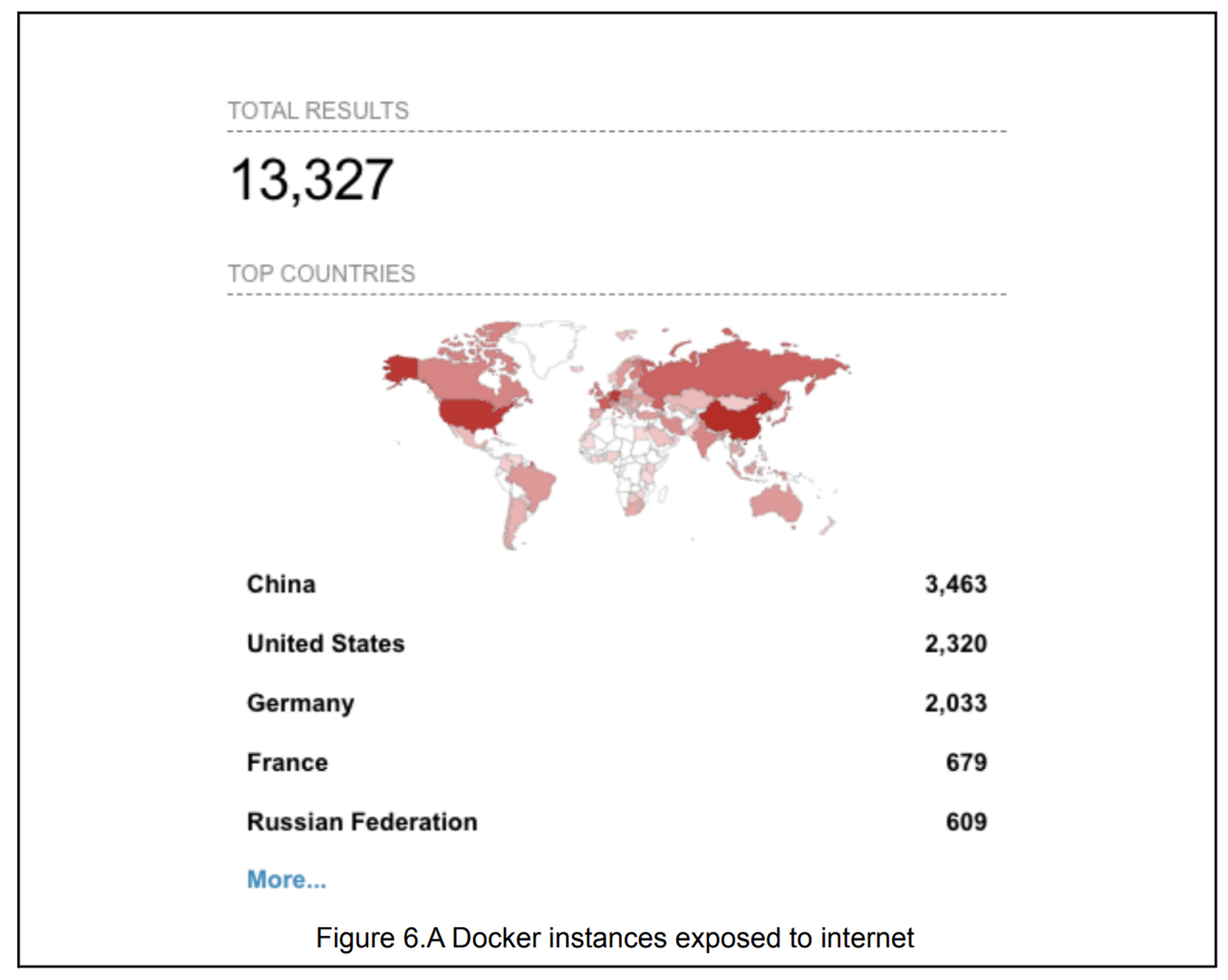
According to researchers, the ultimate goal was to harness victims’ computing power to install XMRig and mine cryptocurrency. While these attacks have been happening for some time before they were first observed by CrowdStrike, a parallel crash of the cryptocurrency market over the summer likely “muffled” their visibility and impact at first.
“The campaigns by cryptojacking groups last from days to months depending on the success rate,” wrote Manoj Ahuje, senior threat researcher for cloud security. “As cryptocurrency prices have dropped, these campaigns have been muffled in the past couple of months until multiple campaigns were launched in October to take advantage of a low competitive environment.”
CrowdStrike doesn’t make a firm attribution around the campaign, but does note that multiple attacks emanated from command and control servers that were previously used by TeamTNT, a hacking group known to target cloud and container environments.
Research from Trend Micro released Oct. 19 tracks a very similar-sounding cryptomining campaign from actors that also target cloud containers, use TeamTNT routines and install XMRig on victim servers. However, Trend Micro senior threat researcher Sunil Bharti wrote that “analysis of the attack patterns and other technical details of the code has also led us to believe that the routines are mimicking TeamTNT’s arsenal, but are likely deployed by another cryptocurrency mining group named WatchDog.”




