At the beginning of 2021, SC Media noted that the next few years were likely to see ransomware actors increasingly target entities in critical infrastructure and cause disruption in the flow of goods and services that are vital to keeping modern society running.
In the following months, high-profile ransomware attacks against oil and gas provider Colonial Pipeline and meat provider JBS offered powerful examples of this possibility, but a new joint advisory from the U.S., U.K. and Australia show that the targeting of critical infrastructure runs much deeper.
The advisory notes that in the United States alone, the FBI, NSA and Cybersecurity and Infrastructure Security Agency (CISA) have observed ransomware attacks affecting 14 of the 16 federally designated critical infrastructure sectors in 2021, as well as an increase in “sophisticated, high-impact ransomware incidents” against these sectors. These attacks have touched defense contractors, emergency services, the food supply, IT infrastructure, and government facilities, among others.
Similar reporting from Australian authorities has found continued targeting of healthcare and medical entities, energy companies, higher education institutions and financial entities, while the U.K. has seen its education sector pummeled by ransomware in the past 12 months. The National Cyber Security Centre repeatedly noted throughout 2021 that attacks against schools and other education entities were skyrocketing.
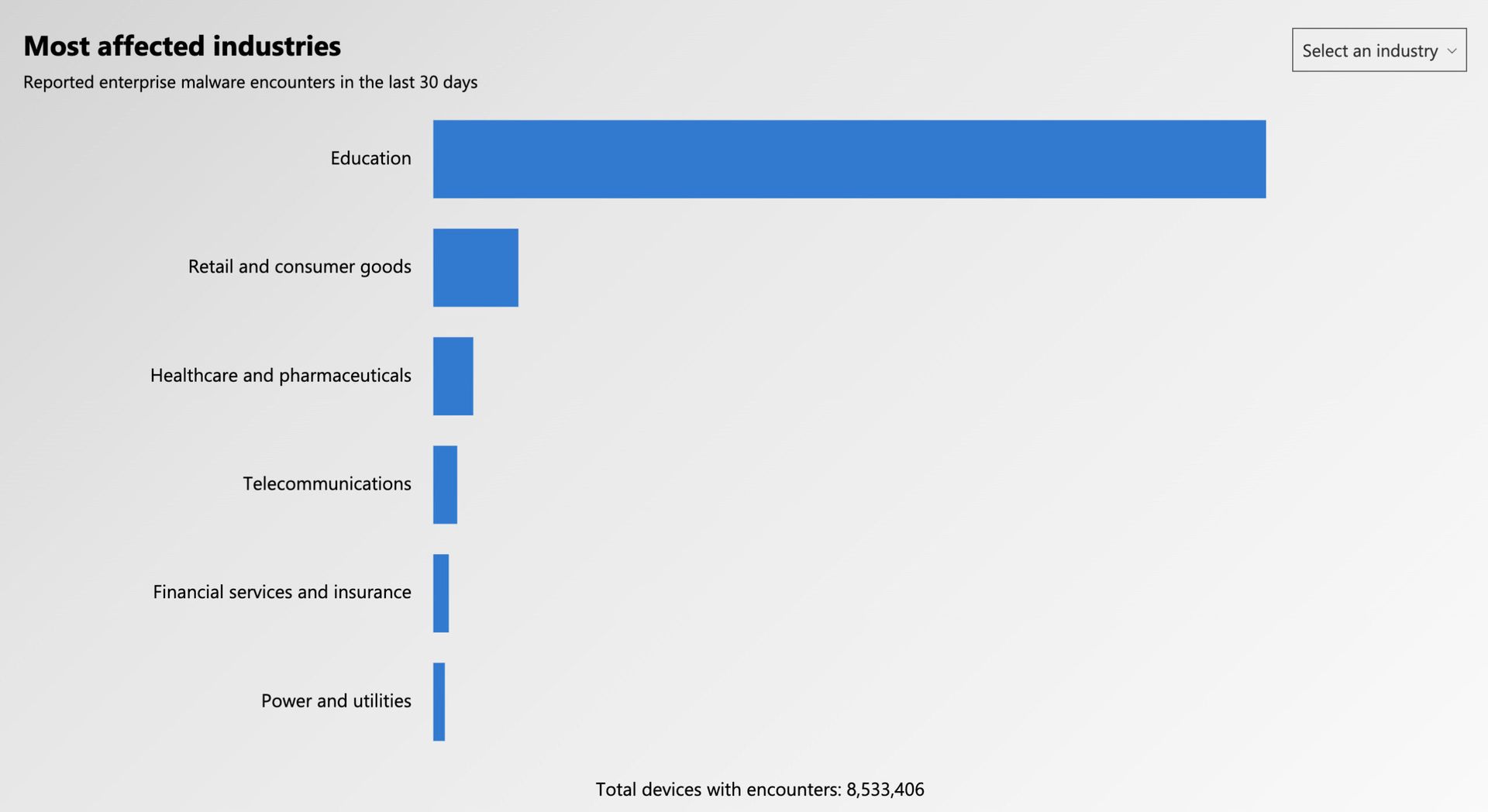
Increased attacks against the education sector is not just isolated to the U.K.: U.S. K-12 school systems have become a favorite target for ransomware criminals because these districts often have little funding and resources around IT or security. Nor is it just about ransomware. Microsoft’s global threat activity map consistently shows education entities as far and away the No. 1 victim of observed malware events on Microsoft devices:
In the unsettled world of international cyber norms, there are few if any hard rules that garner consensus, but avoiding attacks on critical infrastructure — which can lead to widespread disruption of vital services, and even death — has long been discussed as a red line, not only by the U.S. and Western governments but also adversarial nations like Russia and China.
Ransomware 'red lines' difficult to measure
It should be noted that while these agencies say they are observing an increase in such attacks levied against critical infrastructure, that level of visibility and measurement over the impact of ransomware has traditionally been difficult to report on. SC Media asked Emsisoft's Brett Callow (who specializes in ransomware) if he had or knew of any independent data that could demonstrate this global increase.
Callow said he collects numbers of both disclosed and undisclosed attacks on state and local governments, healthcare entities and educational institutions, but that when it comes to this issue "as a wise man once said, 'knowing is half the battle.' Unfortunately we don't know."
"Given that [critical infrastructure] is owned privately and the previous absence of reporting requirements, I’m really not sure whether anybody has a good handle on the number of incidents," Callow told SC Media in an email. "We certainly don’t, and I couldn’t begin speculate as to whether there’s been an increase or decrease."
The lack of metrics around the scope and impact of ransomware is a major problem that policymakers must grapple with. A paper published last year by the Internet Policy Research Initiative at MIT found that, for a variety of different reasons -- ranging from a lack of technical and human resources to a lack of reporting mandates and an unwillingness by many companies to voluntarily share details about the attacks they've incurred -- basic information around how many critical infrastructure entities have been attacked or infected by ransomware is not available.
"Despite the government’s and public’s growing interest in addressing cybersecurity issues, the ability to fully understand and prioritize steps to combat ransomware-related risks remains elusive," the authors note. "This is partially driven by a dearth of ransomware information available that could help inform where additional security support would be most beneficial.”
The most popular entry points for ransomware actors described by these government agencies will not come as a surprise, since they are mostly all broadly popular forms of initial access that cyber criminals and state actors have been exploiting for years. Remote Desktop Protocol software has become a lifeline for businesses to remotely access distant computers in the COVID-19 pandemic, but they’re also one of the most prevalent tools ransomware actors use to gain access to victim computers and deploy their malware, along with timeless methods like phishing and software vulnerabilities.
The focus on leveraging RDP “likely remain[s] popular because of the increased use of remote work and schooling starting in 2020 and continuing through 2021,” the joint advisory noted. “This increase expanded the remote attack surface and left network defenders struggling to keep pace with routine software patching.”
They also track something that SC Media has been covering since last year: the evolution of entire support industries around the criminal ransomware ecosystem, spanning everything from the selling and buying of initial access vulnerabilities to the use of third-party ransom negotiators and payment arbitration over the cut different criminal groups take from victims.
Ransomware groups go pro
This “professionalization” of ransomware groups over the past few years has merged the criminal enterprise with a bloodless corporate profit structure. One that has transformed the extortion of victim enterprises into a multi-billion dollar global business and created a conveyor-belt process for processing the payments of current victims while building up a massive pipeline of future attacks. allowing actors to pick and choose where to engage with human personnel in order to wring the highest profit.
The agencies “assess that if the ransomware criminal business model continues to yield financial returns for ransomware actors, ransomware incidents will become more frequent.”
“Additionally, cybersecurity authorities in the United States, Australia, and the United Kingdom note that the criminal business model often complicates attribution because there are complex networks of developers, affiliates, and freelancers; it is often difficult to identify conclusively the actors behind a ransomware incident,” they added.
Interestingly, the agencies posit that high-profile actions by law enforcement and other entities to degrade the infrastructure used by ransomware actors has pushed them away from “Big Game Hunting” — or explicit targeting of larger organizations capable of paying higher ransoms — to focusing on smaller or mid-range organizations that may not bring as much heat or public attention.




