Researchers at Ermetic have found and reported a cross-site request forgery vulnerability software management tool that is used across multiple Microsoft Azure cloud services and would allow an attacker to take over and remotely execute code on a victim’s application.
The bug, first discovered by researcher Liv Matan and reported to Microsoft on Oct. 26, is the result of manipulating a series of misconfigurations and security bypasses in Kudu, a back-end source control management (SCM) tool that helps manage and modify web applications and is used by major services like Azure Functions, Azure App Service and Azure Logic Apps.
The name given to the bug, EmojiDeploy, derives from the way Kudu is configured by default in a way that makes it vulnerable to cross-site request forgeries. It would allow an actor to create a malicious Domain Name System record that can bypass an SCM server’s origin checks by using special characters. In this instance, the special characters used by the Ermetic researchers to bypass those checks and security controls were “._.”, resembling an emoji.
From there, the attacker must locate a vulnerable endpoint to deploy a malicious zip file through a browser. With one click, an attacker is able to run code and commands as the www user, steal or delete sensitive data, take over the app’s managed identity and conduct lateral movement across other Azure services and facilitate future phishing campaigns.
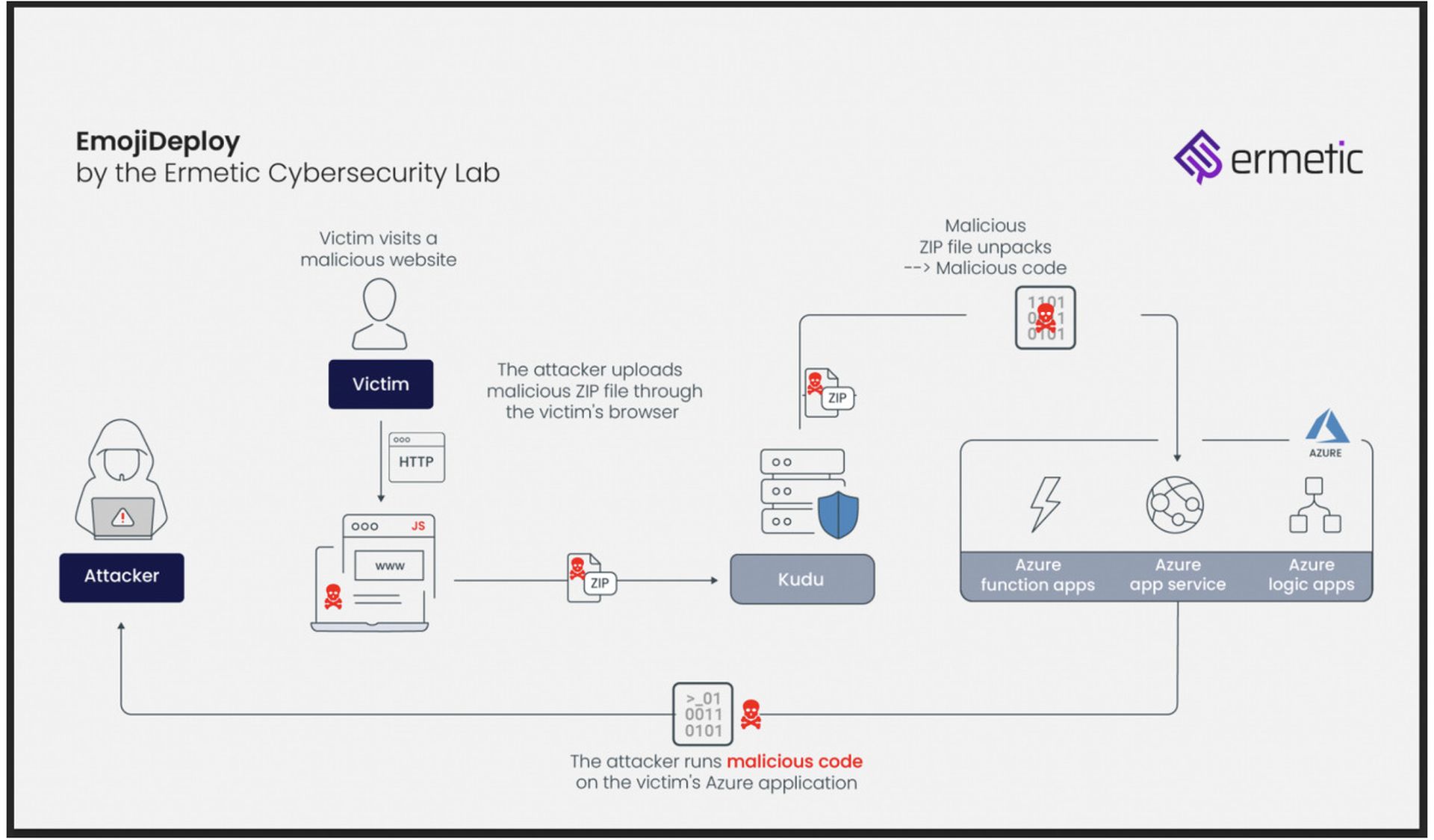
In an interview, Matan said that he eventually keyed in on Kudu, knowing that if he cound find a way to bypass its authentication protocols, it would likely give him broad-based access and capabilities across multiple Azure products.
“It seemed impossible for us to target all of those services at once, until we discovered [some] common ground between them,” said Matan. “Kudu deploys itself behind every application and every service … it triggered our researcher mindset, because if an attacker could potentially target and take over this service, it could run sensitive operations on behalf of the victim.”
According to Ermetic, the discovery resulted in Microsoft awarding a $30,000 bug bounty before the software giant rolled out a global fix on Dec. 6. As a result of the disclosure, Ermetic said Microsoft strengthened the origin check on the server and changed the same-site value of the authentication session cookies used by Kudu.
Igal Gofman, head of research at Ermetic, said a bad actor would need a certain amount of technical skill to find something like EmojiDeploy and it would still require a user to first click on a malicious link to exploit. However, once they have, it offers a fairly direct path to compromising web applications.
“It’s not a script kiddie vulnerability, but once an advanced attacker finds the vulnerability it is very easily exploitable,” said Gofman.
While Microsoft has patched the EmojiDeploy vulnerability, Ermetic researchers recommend a number of steps organizations can take to protect themselves from similar attacks. For instance, deploying least privilege access policies for back-end tools like Kudu that have broad-based privileges across multiple applications and services can help to limit the potential damage of a compromise.
EmojiDeploy is the second vulnerability disclosure this week targeting major Azure services.
On Tuesday, Orca Security published research on vulnerabilities that allow for server-side request forgeries and affecting Azure API Management, Azure Functions, Azure Machine Learning, and Azure Digitals.




