A year ago, a series of document leaks from the Conti ransomware gang offered a rare glimpse into the inner workings of cybercriminal organizations. However, Conti, as one of the largest and most prolific cybercriminal groups in 2021, is just a single representation of a vast range of underground businesses, each with their own unique structure and operating strategies.
To fully comprehend the complexities of the business, Trend Micro's study "Inside the Halls of a Cybercrime Business" sheds light on the importance of defining and understanding the size of these organizations.
"Size matters," said Jon Clay, vice president of threat intelligence at Trend Micro. "Like any other legitimate businesses, cybercriminals tend to develop their business models based on how large their organizations are. Therefore, understanding the size allows defenders to gain a better sense of their operational flow and ultimately infiltrate or take down the groups."
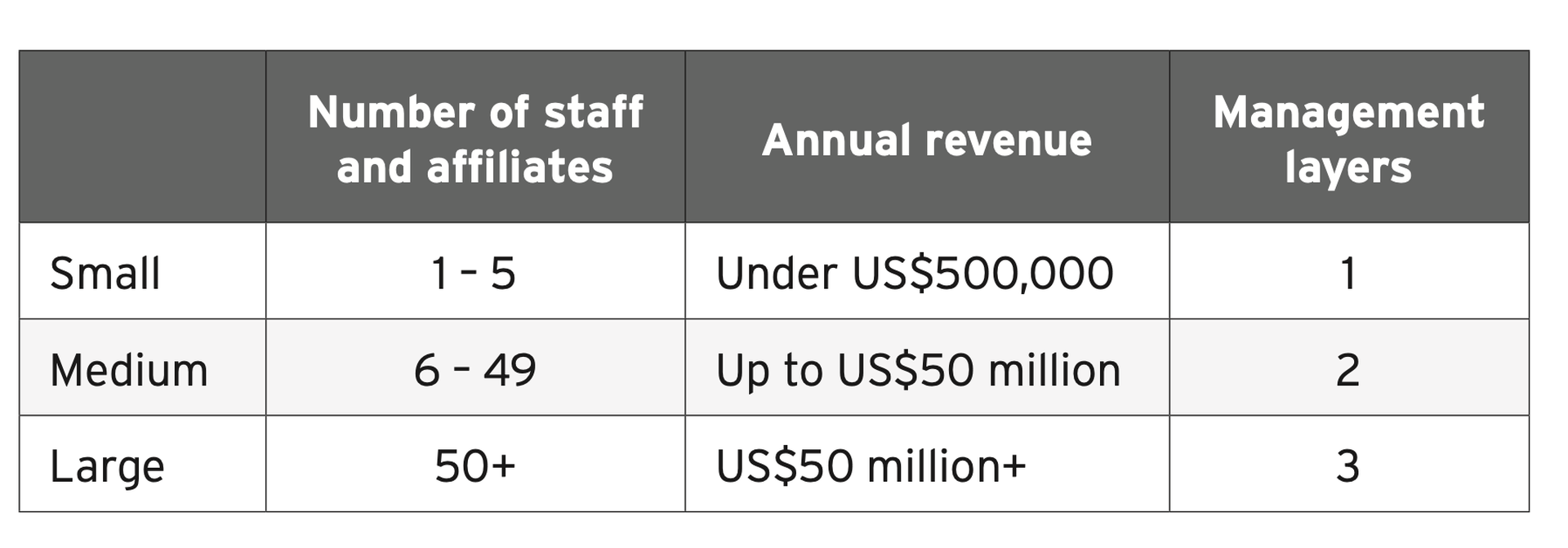
The traditional size classification used for legitimate companies, however, cannot be applied to cybercriminal organizations, as they are generally smaller in size.
In the study, researchers developed their own guidelines to define criminal business scale based on their observed employee counts, annual revenue, and hierarchical structures over time. Furthermore, researchers provided a detailed example of organizations that fall under each of the small, medium, and large categories, along with estimations of their quarterly financial reports based on insider information and law enforcement arrests.
"These size guidelines are not rigid numbers, just like the legitimate business do not always fit into the predefined categories, but they provide valuable insights in classifying and profiling cybercriminal organizations," Clay said.
Small criminal business: No hierarchy, highly specialized products, part-time employees
Small criminal organizations are the dominant players in the cybercrime market, with a few or even no management layers, one to five members, and an annual revenue under $500,000. Like real-world start-ups, these groups tend to specialize in one area to establish their reputation in the underground market — and if they do succeed, they are likely to evolve into larger organizations.
The study analyzed Scan4You, one of the most popular Counter Antivirus services that operated from 2012 to 2017, as an example of small cybercriminal business setups. The group was observed to be run by only individuals with no defined leaders — one responsible for technical infrastructure and the other for customer service — and made around $15,000 per month in 2013.
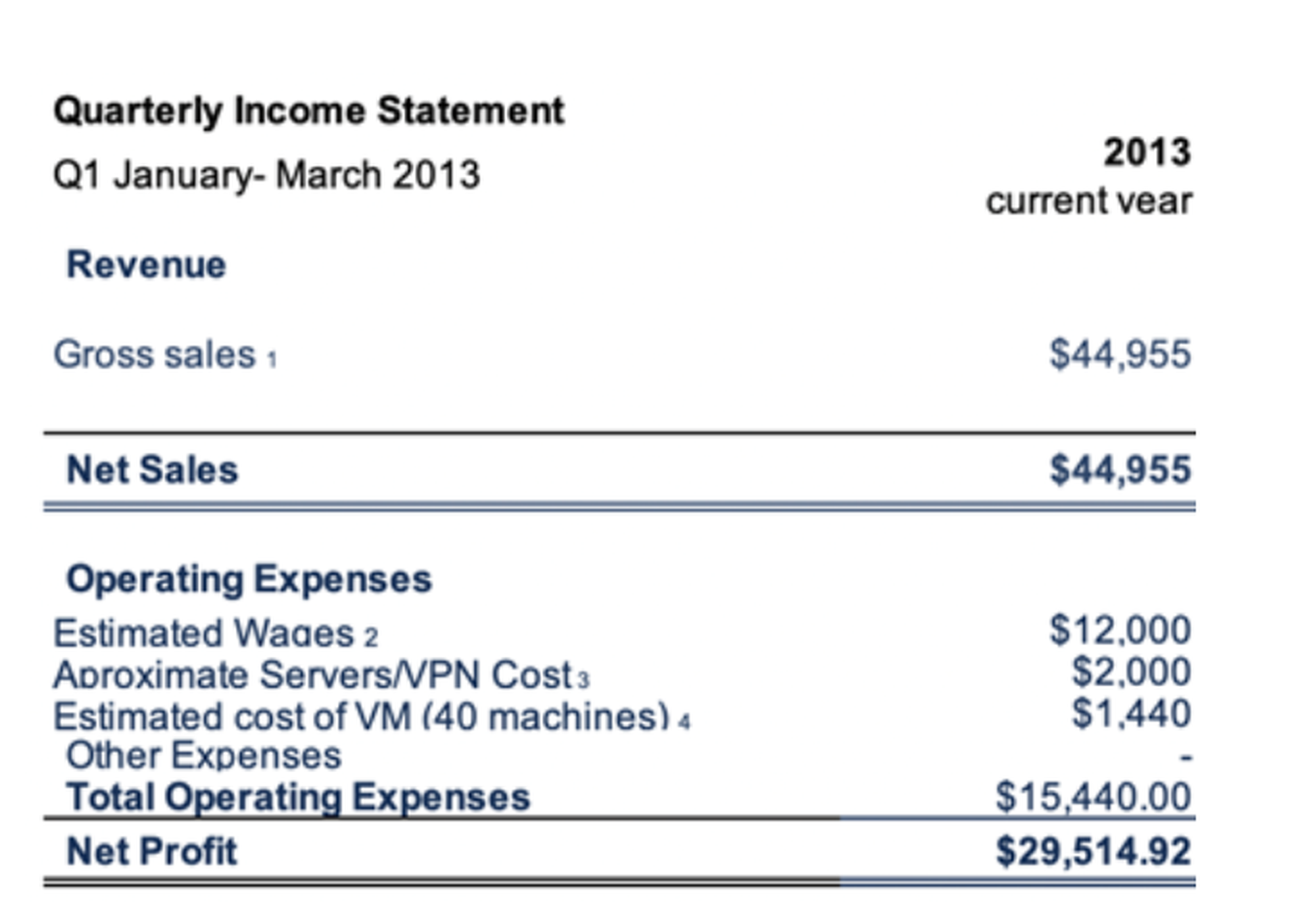
Scan4You's operators have day jobs on top of their role as cyber offenders, which is the case for most small criminal groups. Specifically, researchers found that one of its members, Ruslans Bondars (aka Borland), was a software developer at a global internet company and mainly worked on programming in Python. According to Glassdoor, as of 2022, a software developer like Bondars based in Latvia can earn around $,3000 per month.
Midsize criminal group: Basic reporting lines, full-time employees
Medium-size organizations, on the other hand, have a more hierarchical structure, typically following a pyramid-style organizational chart with two management layers, six to 49 members, and up to $50 million in annual revenue.
MaxiDed, a bulletproof hosting provider seized by Dutch police in 2018, is classified as midsize cybercriminal organization, with one boss leading at least five administrators and earning an estimated annual revenue of $925,000.
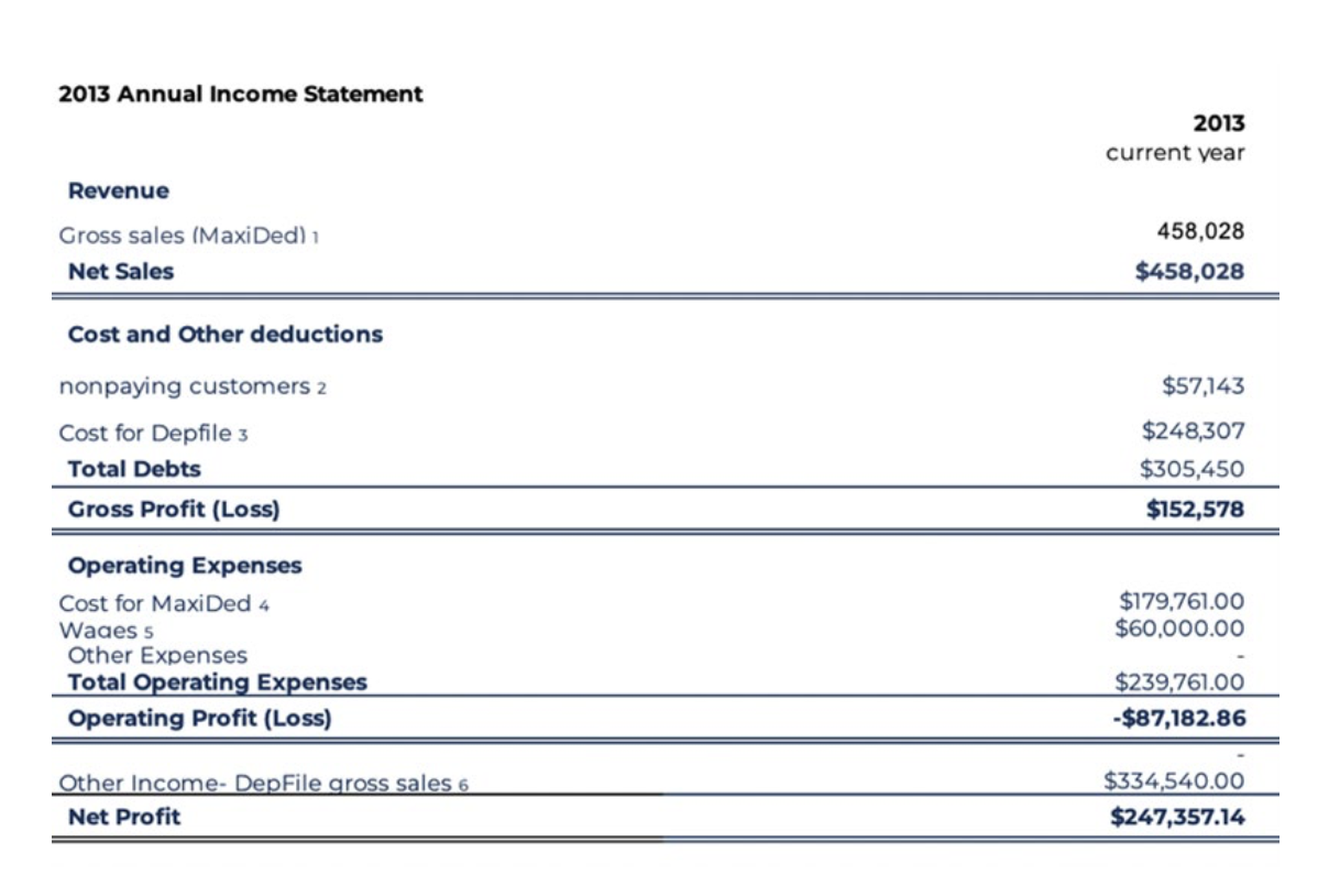
The group started off as a legal small hosting provider in 2008, and then turned into hosting illegal activities, including child abuse material, DDoS botnets, cyberespionage, malvertising and spam.
Unlike part-time operators in small criminal businesses, researchers suggested that MaxiDed administrators have to work full-time for at least eight hours a day and are "very busy" and "stressful." They have to handle support ticket requests queue and new server orders while making advertising on underground forums and answering questions about the company's service.
Large criminal organization: Highly hierarchical, six-figure monthly salary, employee programs
Large cybercriminal groups operate as highly organized enterprises with at least three management layers on top of the pyramid, more than 50 employees, and over $50 million in annual revenue. Plus, they have corporate-like departments such as human resources and information technology to support the operation. Some even have employee programs, such as yearly performance reviews and the recognition of exemplary employees.
Without a doubt, Conti sets a prime example of a large cybercriminal organization. Based on the leaked document from the group's internal chat logs in February 2022 and a previous study by Chainalysis, researchers estimate that it had a gross sale of $180 million and a net profit of $54 million in 2021. Its employees can be paid up to $165,000 per month with benefits including weekends off, federal holiday breaks, and bonus programs.
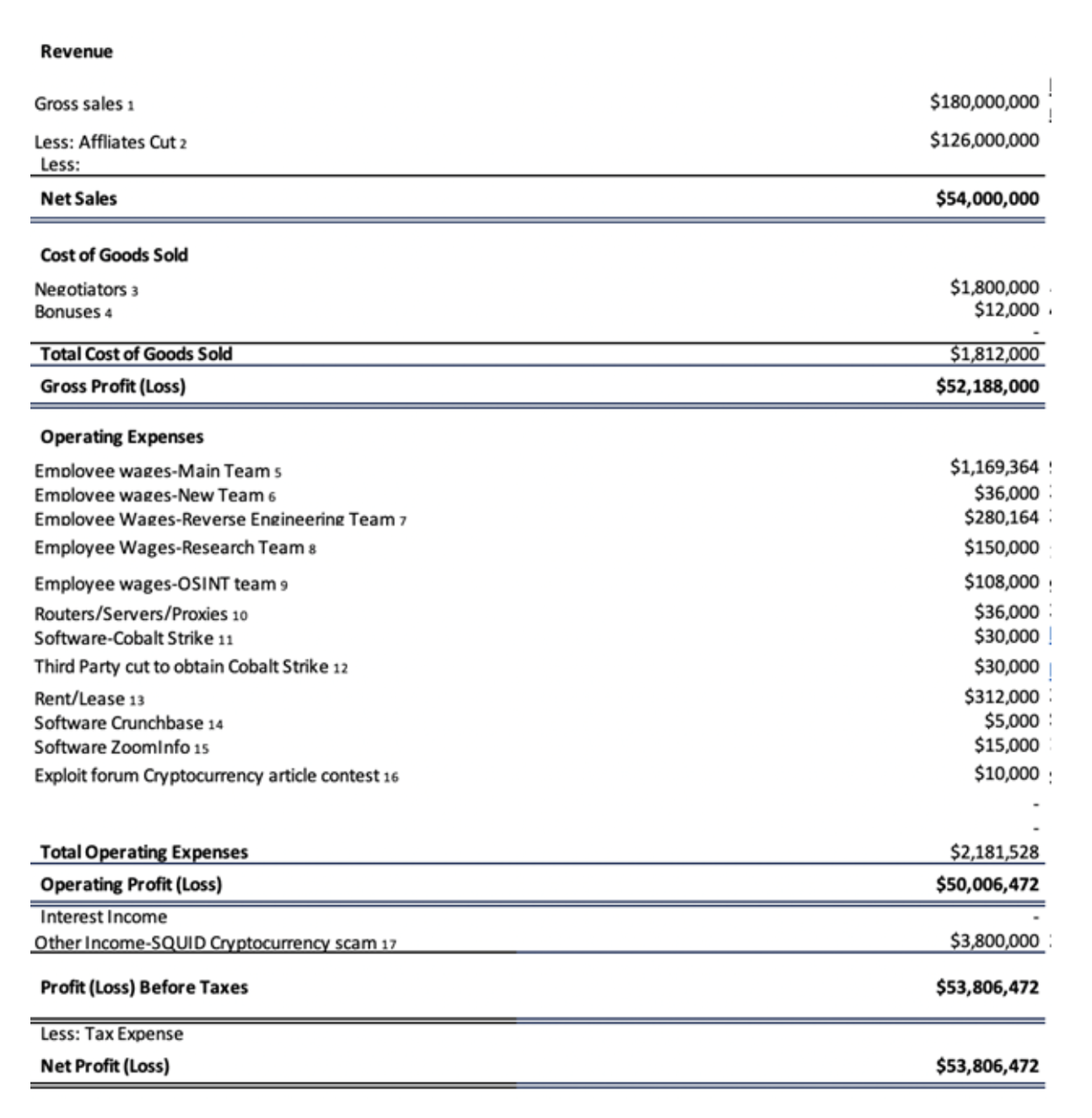
While large organizations are distinct in size and revenue, researchers highlighted that their complicated and hierarchical business models make them hard to manage, leaving more chances for defenders to disrupt and dismantle their networks.
"[Large organizations] grapple with more political issues and have more performers to deal with. They contend with more trust issues, aside from managing overhead expenses that come with the size of their operations," said David Sancho and Mayra Rosario Fuentes, threat researchers at Trend Micro, noting failing to address these concerns can lead to organizational collapse, as seen with Conti.
Size matters
Kurtis Minder, chief executive officer and co-founder of GroupSense, said understanding the size of cybercriminal organizations allows law enforcement agencies and researchers to allocate resources —such as time, personnel and technology — more effectively to prioritize the takedown of certain organizations.
To determine the size, Trend Micro researchers recommended investigating multiple sources, such as the organization's financial statements, list of employees, department-specific documentation, merger and acquisition data, software licenses, organizational charts, and shared calendars.
DiMaggio, however, said that locating an organization's actual documents can be challenging and dangerous, suggesting researchers start with browsing hiring ads posted in the underground forum to get an idea of the structure of those organizations before diving deep into the investigation.
"If there is something that leaked Conti chats have taught us, it's that information disclosure can be far more powerful in crippling a group's operations than server takedowns," said Sancho and Fuentes. "Once private information is leaked, the trust relationship between group members and between their external partners can be irreversibly eroded."




