Russian-aligned ransomware-as-a-service group Qilin is offering its affiliates sophisticated, user-friendly tools to snare their victims, along with a large cut of the proceeds they steal, according to researchers.
Qilin, also known as Agenda ransomware, was first identified by Trend Micro in August last year and has been targeting companies in the healthcare and education sectors.
In a blog post on Monday, Group-IB revealed previously unknown details of Qilin’s inner workings after infiltrating their operations, including its claim to have compromised at least 12 victims since July last year.
The group offers substantial flexibility in their tooling to help affiliates manage attacks on businesses and other organizations. Threat intelligence analyst Nikolay Kichatov wrote that the RaaS operator has recently pivoted from a solution using Go language (Golang) to a Rust-based ransomware that makes it easier to tailor attacks to Windows, Linux and other operating system environments.
“Many Qilin ransomware attacks are customized for each victim to maximize their impact. To do this, the threat actors can leverage such tactics as changing the filename extensions of encrypted files and terminating specific processes and services,” Kichatov wrote.
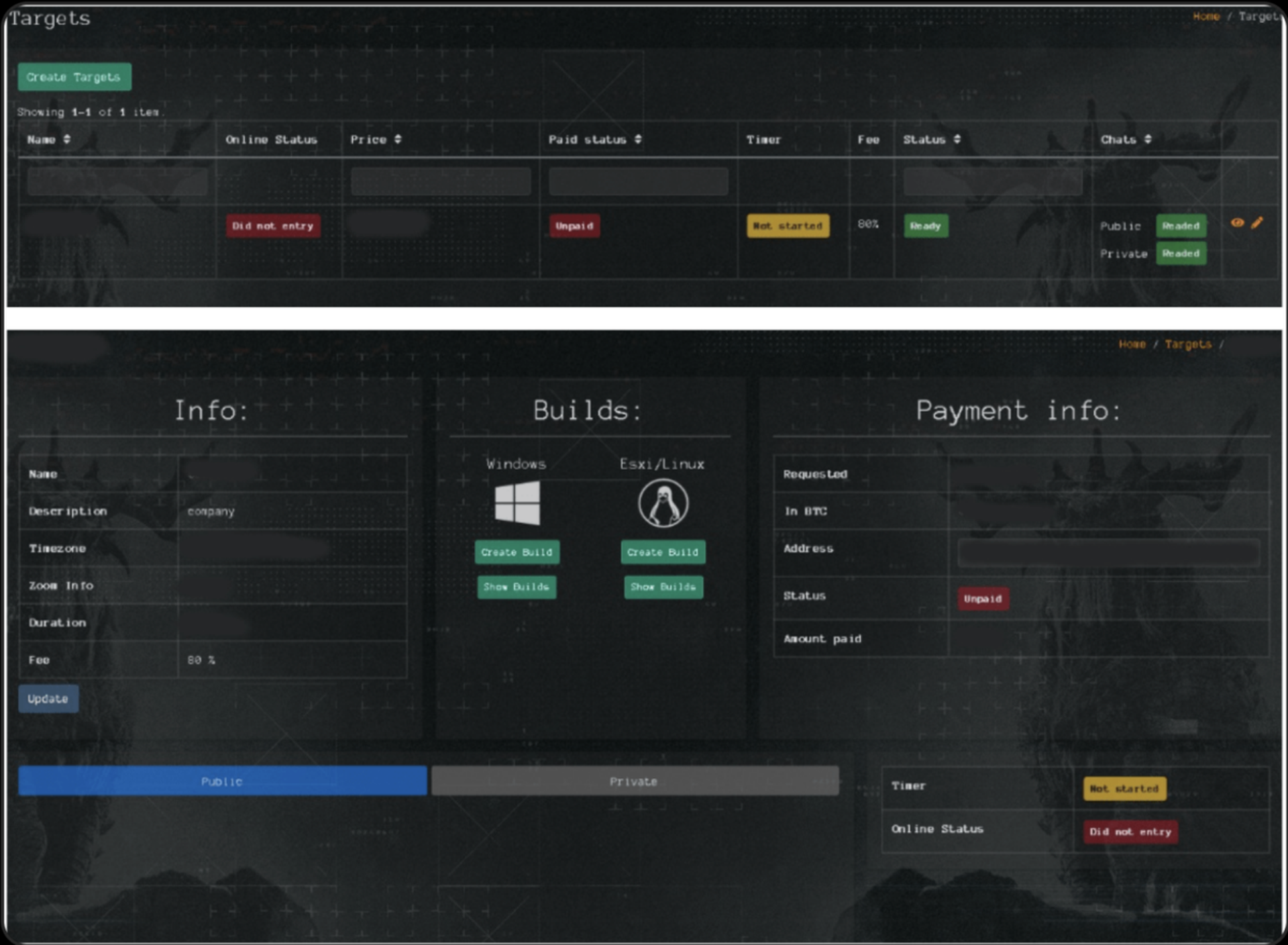
Having infiltrated Qilin, Group-IB threat intelligence researchers were able to analyze the inner workings of the affiliate program and the admin panel, which is divided into six sections. Kichatov’s post provides a breakdown of the functions of each section.
The “Targets” section contains information about attacked companies or intended targets, including company background, value of the ransom demand, allowable wait time for payment, content of the ransom note, processes that will be killed, login credentials for accounts, and other details.
There is also a “Blogs” section for affiliates to create and edit blog posts about attacked companies that have not paid the ransom; a “Stuffers” section to create accounts for team members and control whether they can witness attacks, build ransomware samples, or access chat channels; a “News” to post updates related to their ransomware partnership; a “Payments” section detailing information about the balance of affiliate wallets, transactions, and fees to the ransomware group and an “FAQ” section to provides affiliates with access to support and documentation, including details of the type of infections available, how to use the malware, and additional information about targets.
Group-IB researchers obtained a screenshot of a dark web post from Qilin advertising its RaaS service to potential affiliates. The post, written in Russian, said Qilin offers “customizable encryption modes to find the perfect balance of encryption speed and cryptographic strength”. This was achieved through four operating modes: “full” encryption of a compromised system, “step-skip” or partial encryption, “fast” encryption of the beginning of files, or a percentage encryption based on file size.
The post claims Qilin was “a unique project, and not another fork of other software sources lying in the public domain”. The post said the group “does not work in CIS countries,” a reference to the Russian-aligned Commonwealth of Independent States.
Group-IB’s threat intelligence team was able to obtain information about Qilin’s payment structure by entering a private conversation with one of the users on Tox (an open-end messaging app that offers end-to-end encryption), who was identified on the underground forum RAMP.
According to the information provided by the owner of the RaaS program, for payments totaling $3 million or less, affiliates kept 80% of the profits; for payments of more than $3 million, they kept 85%.
Qilin targets its victims through phishing emails to gain a foothold in victim networks before moving laterally across the victim’s infrastructure, searching for essential data to encrypt.
During the encryption process, the affiliates place a ransom note in each infected directory of the system with instructions on how to purchase the decryption key.
“They may also attempt to reboot systems in normal mode and stop server-specific processes to make it harder for the victim to recover their data. If the ransomware operator is successful in encrypting a victim’s files, it uses a double extortion technique as a means to increase its potential revenue,” Kichatov wrote.
On Qilin’s leak site, Group-IB researchers found data the ransomware actors claimed was stolen from 12 companies it had attacked: two each in the U.S. and Canada, with other victims based in Australia, Brazil, Colombia, France, Netherlands, Serbia, the United Kingdom, and Japan.