Industry experts expressed skepticism over new survey findings that suggest cyber adversaries are directly approaching business employees on a routine basis and asking for their assistance in helping set up ransomware attacks. But while such direct communication between attackers and workers may not occur quite as often as the research suggests, it certainly can happen; thus, it’s important companies know how to spot an employee that’s been turned into an insider threat, and how to nip such scenarios in the bud.
Conducted by Pulse on behalf of Hitachi ID, the survey polled 100 IT and security executives, 48% of whom said that they or other employees within their company have been approached to assist in planning a ransomware infection. Among those who say that they or other co-workers have been propositioned in this matter, 83% said such incidents have increased since employees started working from home.
Despite how prevalent ransomware has become, some experts took this finding with a grain of salt, noting that the numbers sounded quite elevated. Even an Hitachi ID PR spokesperson acknowledged the statistic “caught our attention given how high it was,” adding that “we are planning on digging into it a little further in our upcoming survey to glean additional insight.”
“This number is incredibly high,” agreed Jon DiMaggio. “If it's correct, why are there not more publicly known examples and/or law enforcement operations leading to indictments or arrests?... Don't you think there would be many more insider threat incidents, arrests, or legal investigations taking place? I do, which is why that figure is likely inaccurate or based on [executives’] perception and not quantitative threats or accurate data/metrics,” he said.
Allan Liska, senior security architect at Recorded Future, said he has been aware of ransomware groups trying to recruit insider threats for some time. However, “we haven't seen a big uptick in ransomware attacks initiated by an insider threat. That is not to say that it doesn't happen, but I would need a second survey showing this level of widespread ransomware insider threat adoption before I was convinced.”
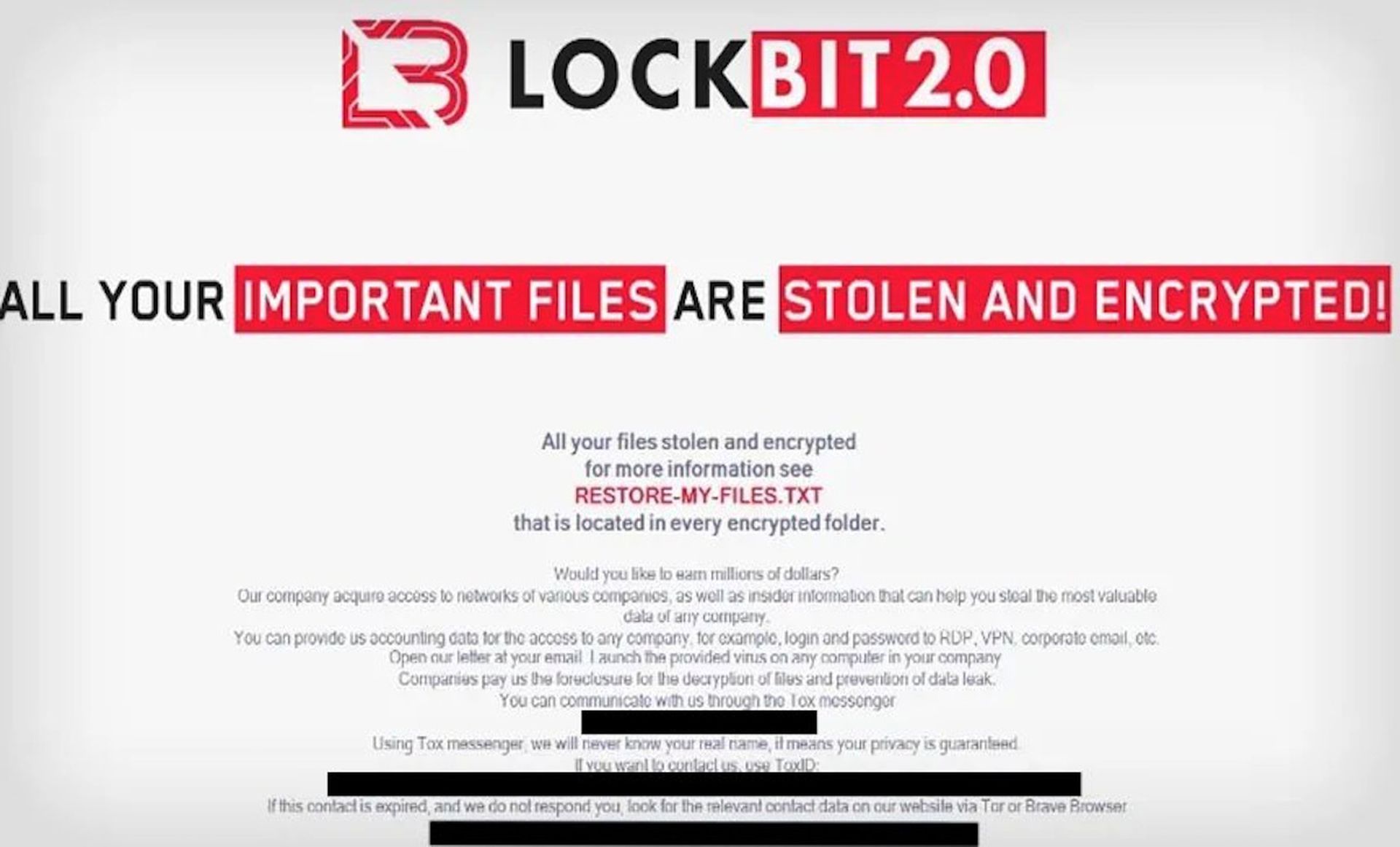
Still, when it does happen, the ask can be quite brazen. For instance, Liska, showed SC Media an example of a ransomware note from the LockBit ransomware group actively encouraging employees to reach out and assist with future ransomware attacks.
“Would you like to earn millions of dollars?” asks the note, which has several grammatical errors. “You can provide us accounting data for the access to any company, for example login and password to RDP, VPN, corporate email, etc. Open our letter at your email. Launch the provided virus on any computer in your company…”
Last year, a Tesla employee was offered $1 million in exchange for his cooperation in an attack against his company. “The ransomware actor met him in person and offered the employee a thumb drive to plug into his computer,” said Liska, noting that this is actually a poor strategy for carrying out an insider threat-based attack because “any company with any endpoint protection and monitoring will be able to trace that directly to the employee.”
Typically, when attackers are able to turn an insider against his or her company, that worker is offered a payment in bitcoins “in return for clicking on a file that the ransomware actor sends via email, in an attempt to make it look like an inadvertent phishing attack,” Liska continued.
Although such deals can fall apart: “I can also confirm that in one case where this happened the employee was caught and the ransomware group never actually paid the employee,” Liska continued. “This is a barrier to successful insider threat recruitment by ransomware groups: overall, employees do not trust [them]. The penalty for getting caught significantly outweighs the potential benefit of however much the ransomware group is offering.”
Still, sometimes the motivation isn’t always entirely financial. “More often… the adversary plays on the targeted employee's emotion,” said DiMaggio. “Disgruntled employees often feel helpless against a large corporation, and these opportunities provide a means for revenge. In cases involving ransomware, the employee simply has to visit a website, download a file, or click on a link in an email.”
DiMaggio said that cybercriminals can scope out potential traitors by digging through employees’ backgrounds on LinkedIn, and reading their forum posts on networks like Reddit and Blind. Using these, “you can find disgruntled employees and their contact information pretty easily,” he explained.
“With the rise in social engineering and the wealth of information individuals expose on the internet, it is not uncommon for threat actors have a deep understanding of their targets, agreed Armaan Mahbod, director of security and business intelligence at DTEX. What is this individual’s current marital status and family relationship? Are they falling on hard times personally, financially, or emotionally? What websites do they frequent?”
“I imagine that cybercriminals will only increase their engagement directly with employees over the coming years, identifying the weak individuals within a community,” and trying to recruit them. In some cases, extorted employees might even be forced to harm their own companies against his or her will. “let’s not overlook the common use of hacking into and stalking an individual’s life, where blackmail will also become a more prevalent concern,” Mahbod noted.
Regardless of how common it is for cybercriminals to turn employees into turncoats, when it does happen the consequences can be severe. Fortunately, experts did offer some recommendations on how to, prevent, identify and neutralize potentially damaging insider threat attacks.
“The same tools used to monitor for insider threats are the ones that can stop a successful ransomware attack: logging, endpoint protection, multi-factor authentication, network segmentation and monitoring,” said Liska. “In addition, security teams should be transparent with employees about what is being monitored. Adversaries will try to convince employees that the likelihood of being detected is non-existent… [but] let employees know your organization can detect these activities and remind them that ransomware groups are not trustworthy and should not be believed.”
Meanwhile, DiMaggio advised that companies harden their systems and infrastructure; create role-based access policies and follow the principle of least privilege; practice risk assessment on employees and monitor their activity; and train workers on how to respond if approached by a malicious actor.