The Lapsus$ extortion group posted screenshots to its Telegram channel Monday night they say prove they breached identity management vendor Okta. The group said the Okta breach was not intended to get data from Okta, but instead leverage the access to Okta to attack Okta clients.
Lapsus$ is a group that extorts the companies under the threat of leaking data — ransom without the ransomware — best known for leaks of Samsung files.
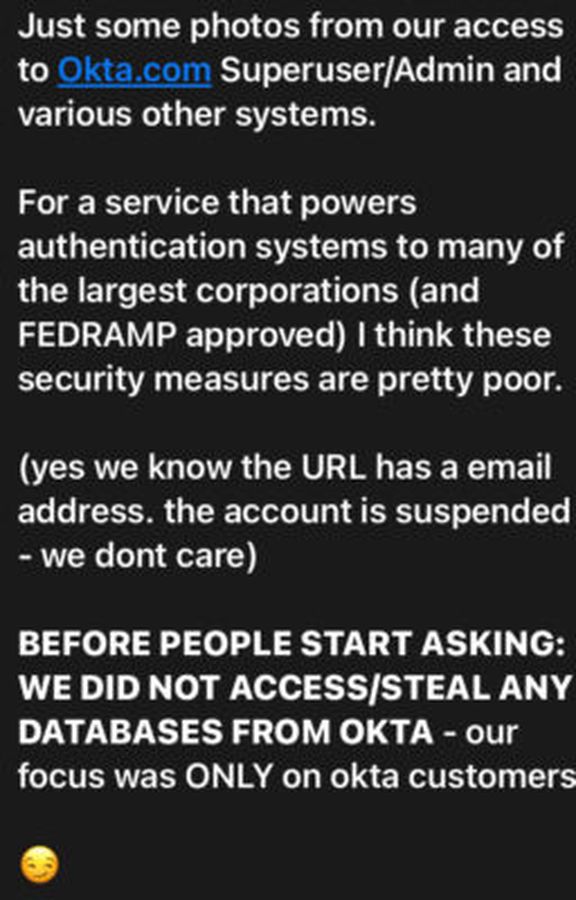
"For a service that powers authentication systems to many of the largest corporations (and FedRAMP approved) I think these security measures are pretty poor," the Lapsus$ post read.
In addition to the Okta announcement last night, they leaked what they claimed was source code for Microsoft's Cortana, Bing and Bing Maps.
On Twitter, Okta chief executive Todd McKinnon confirmed that the company had been breached in January, which Okta believes was the source of the screenshots.
"In late January 2022, Okta detected an attempt to compromise the account of a third party customer support engineer working for one of our subprocessors. The matter was investigated and contained by the subprocessor," he wrote.
After posting screenshots, Lapsus$ claimed in an all-capital-letters update, that Okta was breached not for its own data, but as a supply chain attack.
According to Brett Callow, a ransom group expert with Emsisoft, any Lapsus$ claims should be taken with a professional criminal-sized grain of salt.
"None of Lapsus$' claims should be taken at face value," he said via electronic chat. "Cybercriminals aren't noted for their honesty - however, their claims seem to have been accurate so far."
Investigators have so far found Lapsus$ a tough group to make sense of. They appear to be very disorganized while also being extremely capable, given their targeting, said Callow.



