One of the oldest and most widely spread banking fraud malware, URSNIF, has been re-tooled into a generic backdoor that could become a staple for ransomware actors, according to new research from Mandiant.
URSNIF, also known as Gozi or ISFB, is a high-risk banking trojan that steals system information, records keystroke data, and keeps track of network and browser activity. Multiple variants of the malware, including Dreambot, IAP, RM2, and RM3, have emerged since its source code was leaked in 2016. But researchers noted that this newest variant LDR4, which was first discovered in June, differs from previous iterations and “marks an important milestone for the tool.”
“This is a significant shift from the malware’s original purpose to enable banking fraud, but is consistent with the broader threat landscape,” Mandiant researchers Sandor Nemes, Sulian Lebegue, and Jessa Valdez wrote in a Wednesday blog post. “Given the success and sophistication RM3 previously had, LDR4 could be a significantly dangerous variant — capable of distributing ransomware — that should be watched closely.”
Researchers noted that the most notable change is that the new backdoor has applied a new strategy and removed its banking fraud features, similar to what EMOTET and TRICKBOT have done in the past. LDR4 is now focusing on getting VNC and remote shells into the compromised machine.
Like RM3’s distribution reported back in April 2021, LDR4 was first discovered in a malicious email with a recruitment-related lure. The email redirects users to a compromised website and presents a CAPTCHA challenge to download a Microsoft Excel document, which then fetches and executes the malware.
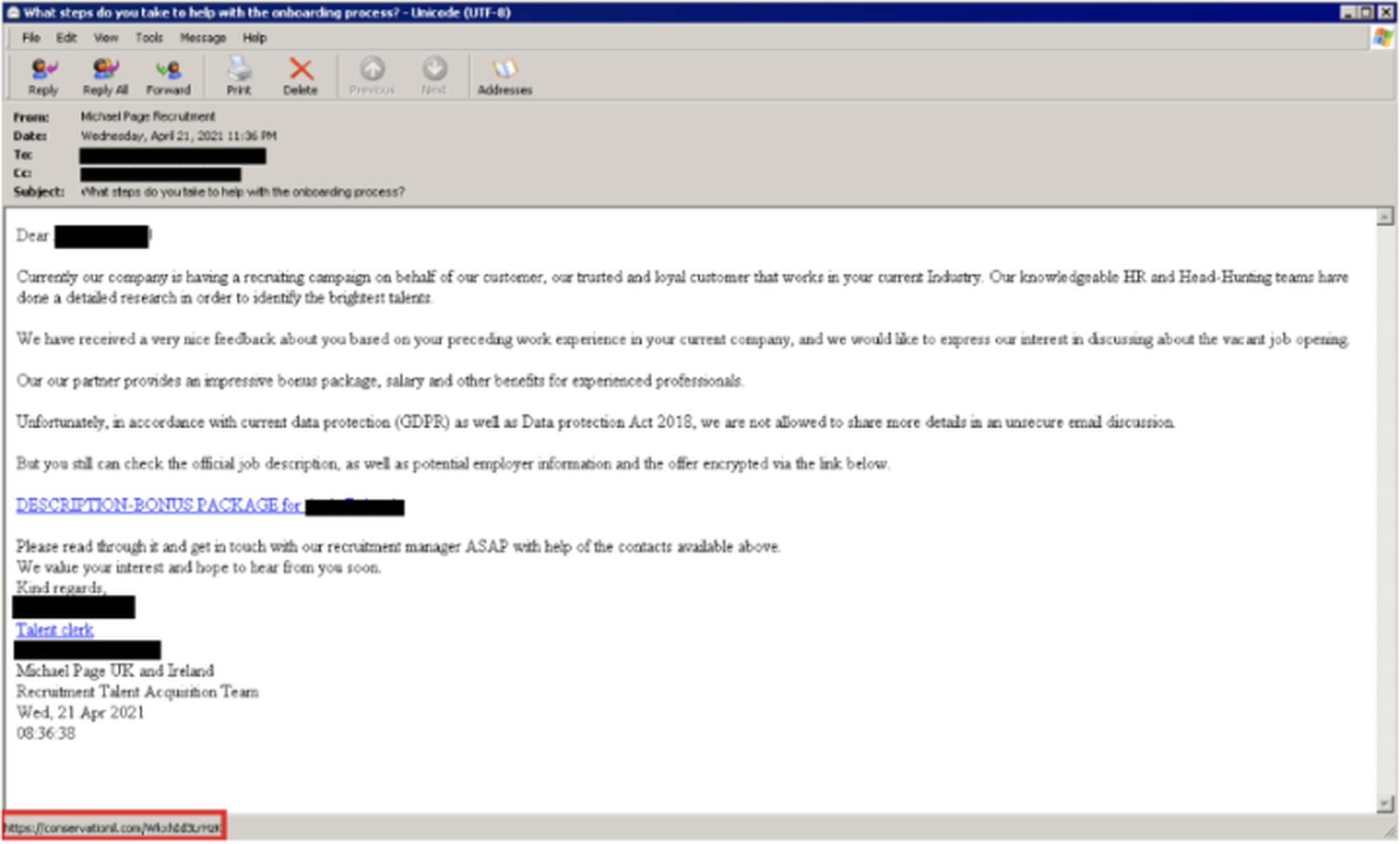
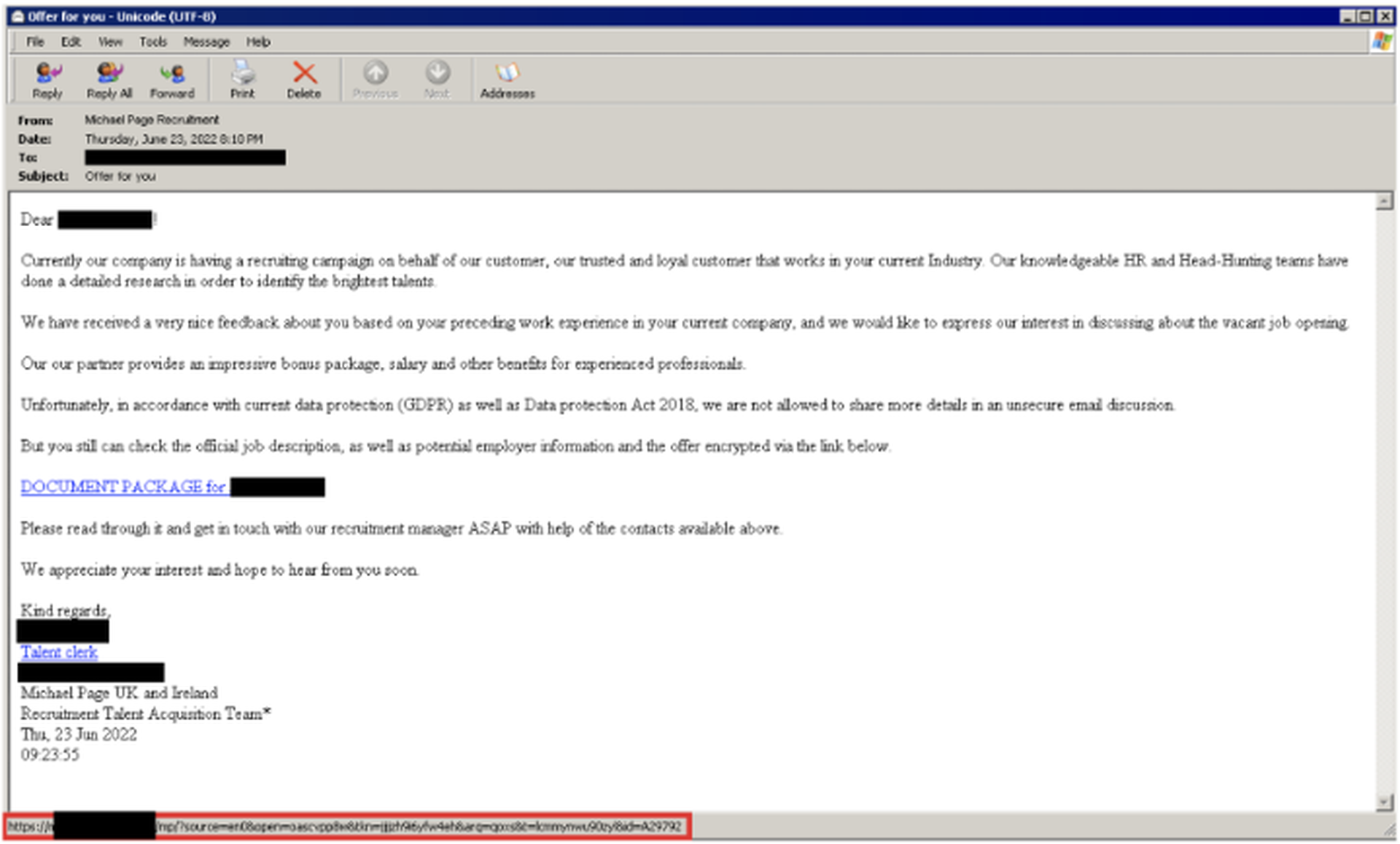
However, the backdoor abandons the custom PX executable format that RM3 first introduced. Researchers believe that the decision was made to simplify the troubleshooting of software problems.
In addition, the PX format can now be detected by antivirus and endpoint detection and response products. “From the attacker’s perspective, investing in a product that everyone knows how to detect is not a very efficient use of resources,” researchers added.
“It is also plausible that increased market competition from other malware operators, such as IcedID, may have led LRD4’s authors to seek ways to reduce the malware’s complexity and make detection efforts more difficult,” Jeremy Kennelly, senior manager of financial crime analysis at Mandiant, told SC Media in an email.
Kennelly noted that LDR4’s historical changes may highlight an increasing focus of threat actors toward participating in or enabling ransomware operations in the future.
“Ransomware operations, whether deploying the ransomware or offering services built around enabling ransomware distribution, continue to be very lucrative for the threat actors involved. And we anticipate this new variant was created to open new revenue streams for the authors,” Kennelly said.
According to Mandiant’s current dataset, researchers have observed LDR4 across Europe, including the UK and Australia which were impacted by previous iterations. Mandiant does not have enough data to assess whether the new variant is being deployed in specific industries.




