Researchers found a popular npm software package with nearly 4 million weekly downloads that is vulnerable to account takeover attacks and could affect over 1,000 organizations.
The package can be taken over by acquiring an expired domain name, software supply chain security company illustria said in a report. They urged maintainers to check their accounts and remove any unused email addresses to mitigate the threat.
Despite npm’s security measures restricting users to only one active email address per account, researchers said attackers can reset the GitHub password using the restored domain and publish malicious packages that lead to large-scale supply chain attacks.
“Initially, we believed it to be a false positive due to our familiarity with the highly popular package, but as we validated the finding it was confirmed that the risk was correct — a domain name associated with one of the maintainers of an npm package with over 3.5 million weekly downloads, had expired and is available for registration, which is indeed a potential account takeover for that package,” the report wrote.
To solidify the finding, researchers contacted the maintainer and got permission to conduct security research the exploitability of the flaw, confirming the package can be taken over by recovering an expired domain.
While researchers expected a high cost in purchasing the domain, it turned out that it was only priced at $8.46 per year.
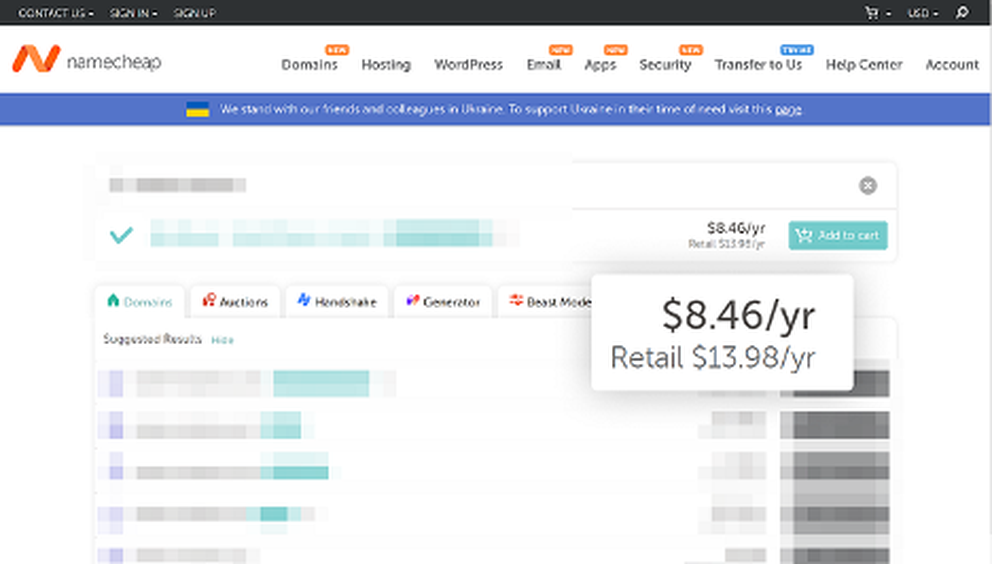
After the purchase, researchers found the package’s associated GitHub account is recoverable.
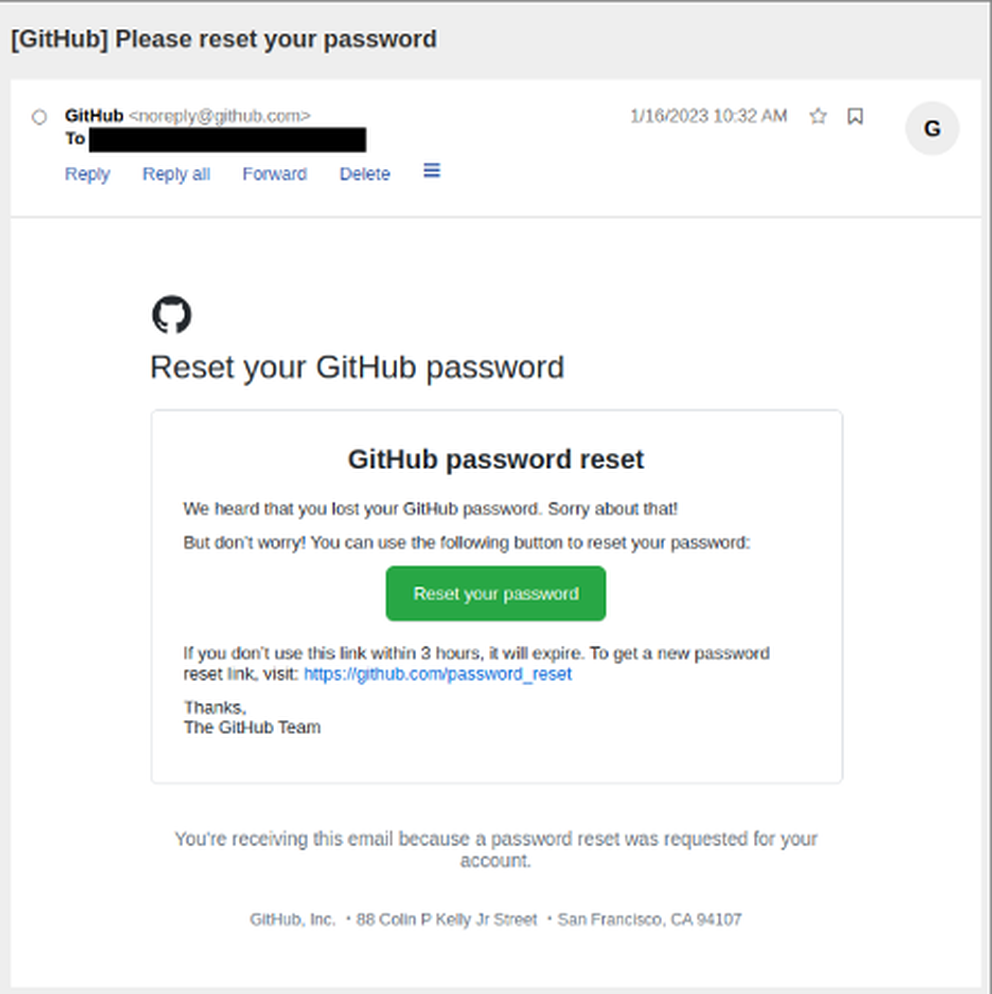
This is achieved using GitHub Actions, which automatically publishes npm packages on new code changes.
"To support such automation, the project maintainer defined an npm automation token for publishing packages automatically as a project secret. Even though the maintainer's npm user account is properly configured with 2FA, this automation token bypasses it," the report explained. "Despite being a secret, this npm automation token can be easily extracted from the GitHub Actions pipeline."
Researchers did not reveal the module's name but shared the information with the maintainer. The maintainer has deleted all the old domains on GitHub and npm to secure the account.
There have been multiple instances of developers' accounts being found vulnerable to takeovers. One such incident occurred in May 2022 when a threat actor registered an expired domain and used it to distribute trojanized Python and PHP packages.




