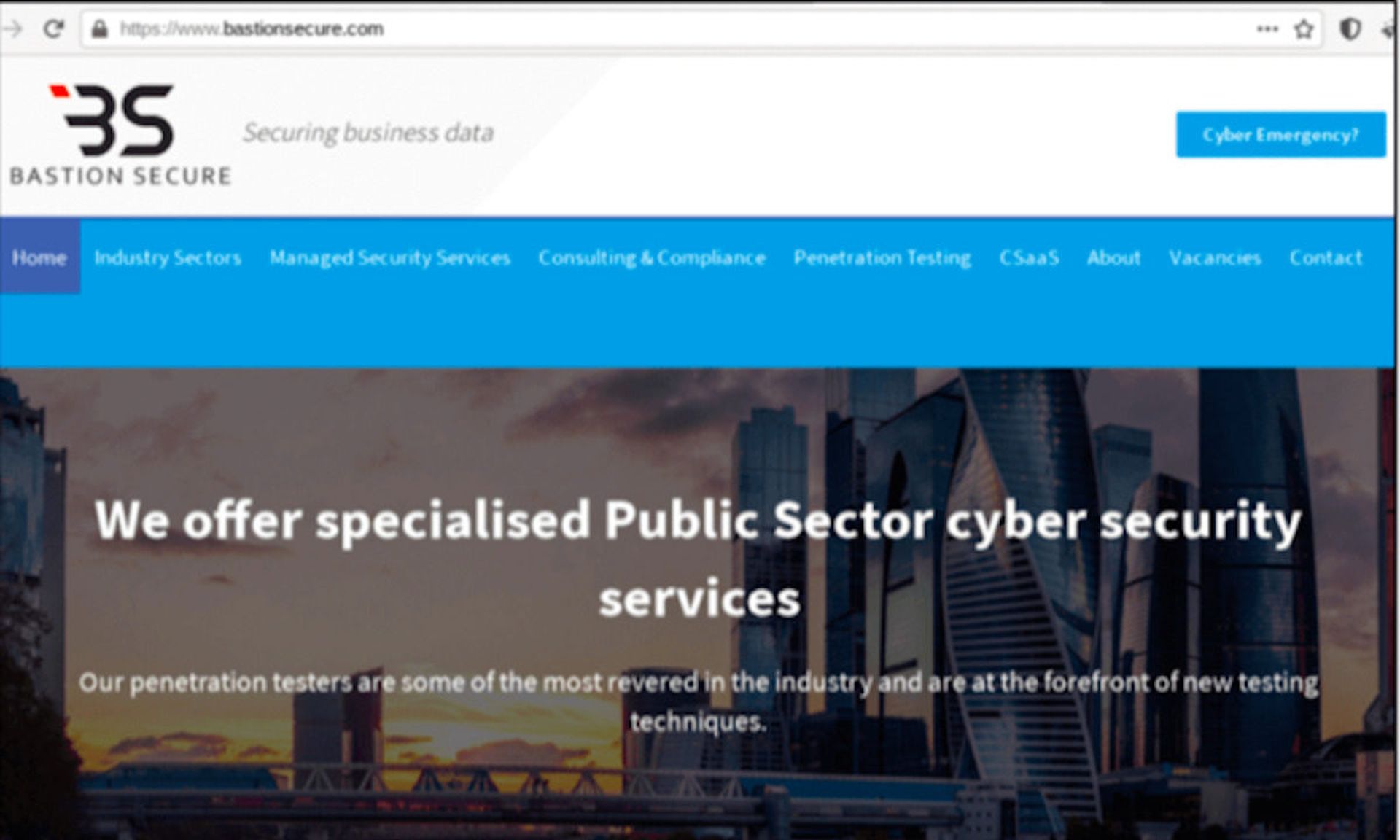
It seems the actors behind the FIN7 cybercriminal group are up to their old tricks, creating the fraudulent pentesting company Bastion Secure as a front to conceal their malicious operations. As part of this charade, the adversaries have even “hired” unsuspecting IT specialists to compromise their victims, under the false premise that they are conducting pentests on paid corporate clients.
On one hand, it seems hard to believe legitimate infosec practitioners could fall for such a scheme. But in the age of virtual CISOs and remote cyber workforces, it might be easier now than ever for malicious front companies to source talent from around the world while concealing the true nature of their motives.
“It would be quite easy for someone to hire a programmer to write some program that would later be used for some cybercriminal activity,” said Stas Alforov, director of research and development at Recorded Future subsidiary Gemini Advisory, which this month issued a blog post report about the scam. “It's all about compartmentalizing what each individual does in the company, so they don’t see the whole picture. So an individual could be hired for a seemingly legitimate task; however, that task could play into a cyber scheme."
"However, at the level that FIN7 operates, to create a website, and create a small infrastructure to hire and train individuals in mass, that is something that has been unique to them,” Alforov continued.
For groups like FIN7 (aka the Carbanak gang), which reputedly operates out of Russian territory and is associated with BlackMatter and Darkside ransomware, there are certain built-in advantages to setting up a fake company for the purpose of finding and exploiting talent.
“FIN7 can pay unwitting ‘employees’ far less than it would have to pay informed criminal accomplices for its ransomware schemes,” explained the aforementioned Gemini Advisory blog post. The Recorded Future subsidiary issued its report after one of its anonymous sources received a fake job offer from Bastion Secure, along with files that turned out to be the FIN7-associated post-exploitation tools Carbanak and Lizar/Tirion.
Earlier in October, Microsoft Cybercrime Intelligence Team Lead Nick Carr and Principal Software Engineer Christopher Glyer led a joint presentation at the 2021 Mandiant Cyber Defense Summit, revealing similar findings related to a group they call Elbrus. Elbrus, essentially, is what became of FIN7 after law enforcement authorities in 2018 issued an indictment against three of its key conspirators.
According to the researchers, FIN7 has previously employed this tactic of operating front companies, including a fake firm called Combi Security.
“There must be some utility in them in them creating front companies or potential front companies,” said Glyer during the presentation. For starters, “it opens up the recruiting opportunities you can recruit through… so you can be much more broad with your recruitment.” In that regard, the researchers indeed found online job postings for a Bastion Secure Windows administrator position in Kiev.
Among the skills required for the job was familiarity with the pentesting tool Metasploit, a tool can be abused for illegal hunting for vulnerabilities. Also, the listing called for “a basic understanding of PowerShell.”
“I'd say no, [more] like medium-to-advanced based on the way they do things,” remarked Carr, also mocking the company’s policies on lunch breaks.
“Given the breadth of job postings, it is likely the recruits made the first contact through submission of their résumé via an Eastern European focused job forum,” Glyer told SC Media in a separate interview. “There are many elements that could make an organization look convincing, including a semi-professional website, social media presence, video teleconference job interviews, and being interviewed by multiple team members.”
From a recruiting standpoint, job posting are "fairly common both among cybercriminal groups, as well as those who could be considered ‘gray’ in the space,” said Casey Ellis, founder and CTO at Bugcrowd. Other times, he noted, there’s a “direct recruitment approach, with a focus and consideration of the particular skills that might be required, rather than diverting people to ads and general opportunities.”
To make the job offer sound even more convincing, the FIN7/Elbrus attackers even set up a fake website for Bastion Secure, replete with its own professional-looking logo. Indeed, researchers have noted that the Bastion Secure website lifted its layout template and much of its content from the legitimate cybersecurity company CNS – including references to winning an award from SC Media. (We can assure you Bastion Secure did not win.)
Another advantage of creating a fake company: attackers can create employment agreements for potential workers to fill out their personal information, allowing them to perform “deeper vetting of potential candidates so that they don't get you know, potential law enforcement or other entity making their way into the into the organization,” said Carr. What’s more, while some naïve employees may not realize what they’ve gotten into; others may have a sneaking suspicion but still go along with it. For them, having at least the façade of working for a company “gives them some sort of plausible deniability with their family or friends or other things about where they work and where they're getting the income from.”
It may be reassuring to know that Glyer said cybercriminal enterprises operating fraudulently as offensive security employers are still a “fairly rare” scenario. Likewise, Alforov said scams like this are “more common in the FSU [former Soviet Union].” And Ellis Bugcrowd, speculated that it’s “more common in places where cybercrime is more of a business-as-usual thing.”
Still, “as Internet crime continues to proliferate, and as international boundaries become less important in cyberspace, I think its a good thing for practitioners to be vigilant about,” Ellis noted.
For those innocent infosec professionals who might worry they’ve been embroiled in this kind of scam, how can they confirm they were hired by a legit company, and are there certain telltale signs of illegal activity they might pick up on? Also, how should they act if they grow suspicious of their so-called employer’s motivations?
After all, “what normal employee is forced to question if the work their employer gives them is legal?” said Gabby DeMercurio, director of red team, social engineering and physical penetration testing at Coalfire. “That’s a tough call, depending on how the business was set up… They literally run the fake company as a real company.”
For starters, Alforov advised to take note if the hiring or interview process is conducted in an irregular fashion, such as over “unconventional messaging platforms.” You could also perform your due diligence and research a company you interview with to “confirm that there are no discrepancies in the information being provided about the company’s location or their C-level staff.”
“When it comes to vetting companies, I think the single most useful tool available would be to reach out via email or social media to those who’d be able to vouch for the organization in one direction or the other,” said Ellis. “In general, cybersecurity professionals are very willing to help, and we almost invariably have a desire to further our space and protect it from harm.”
“Luckily the cybersecurity community is very small. Everyone knows someone, and if a new company pops up and no one in the community has ever heard of any of the founders, I’d beware,” added DeMercurio.
But even if all of that doesn’t raise any red flags, “most individuals – even if they were duped during the interview – would figure [it] out fairly quickly based on the illegitimacy of the type of work conducted,” Glyer told SC Media. “One hypothetical example, as a result of illegitimate work, is that you see ransom victims show up on public ransomware leak sites right after the work of the ‘penetration tester.’
“Additionally, most red teaming/penetration testing organizations communicate directly with their client/customer through email at a minimum, though often via phone, defining the scope of work, deliverables, pricing for the engagement, and status updates on progress,” he added.
Indeed, “there has to be ongoing communication between red (pentesting) and blue (defender) teams,” the Alforov noted. “Red teams should never be told to [just] go attack that target. The red team must agree with the blue team in advance what the scope of the test would be, how the findings will be presented, and remediation recommendations. Thus, if the communication is not present and the red team is sent to attack, then it is likely a key element in indicating that there is something amiss.”
In the same vein, another clue of wrongdoing, said DeMercurio, would be “that you don’t have a customer contact; you have more of a ‘handler’ where they give you the scope of the test and ask you to deliver on it.”
Experts also advised security professionals to contact their federal law enforcement authorities if they suspect they have been hired to conduct illegal hacking activity.