Bad actors are clearly embracing the concept of “go big or go home.” Earlier this month, Microsoft reported that roughly 10,000 businesses were attacked in a months-long adversary-in-the-middle (AiTM) campaign that raked in estimated millions in financial fraud.
In a detailed description of the phishing campaign, which is estimated to trace back at least as far as September 2021, Microsoft outlined detailed process diagrams, and described how the sophisticated AiTM attacks were able to often bypass multi-factor authentication (MFA) to meet their fraudulent goals.
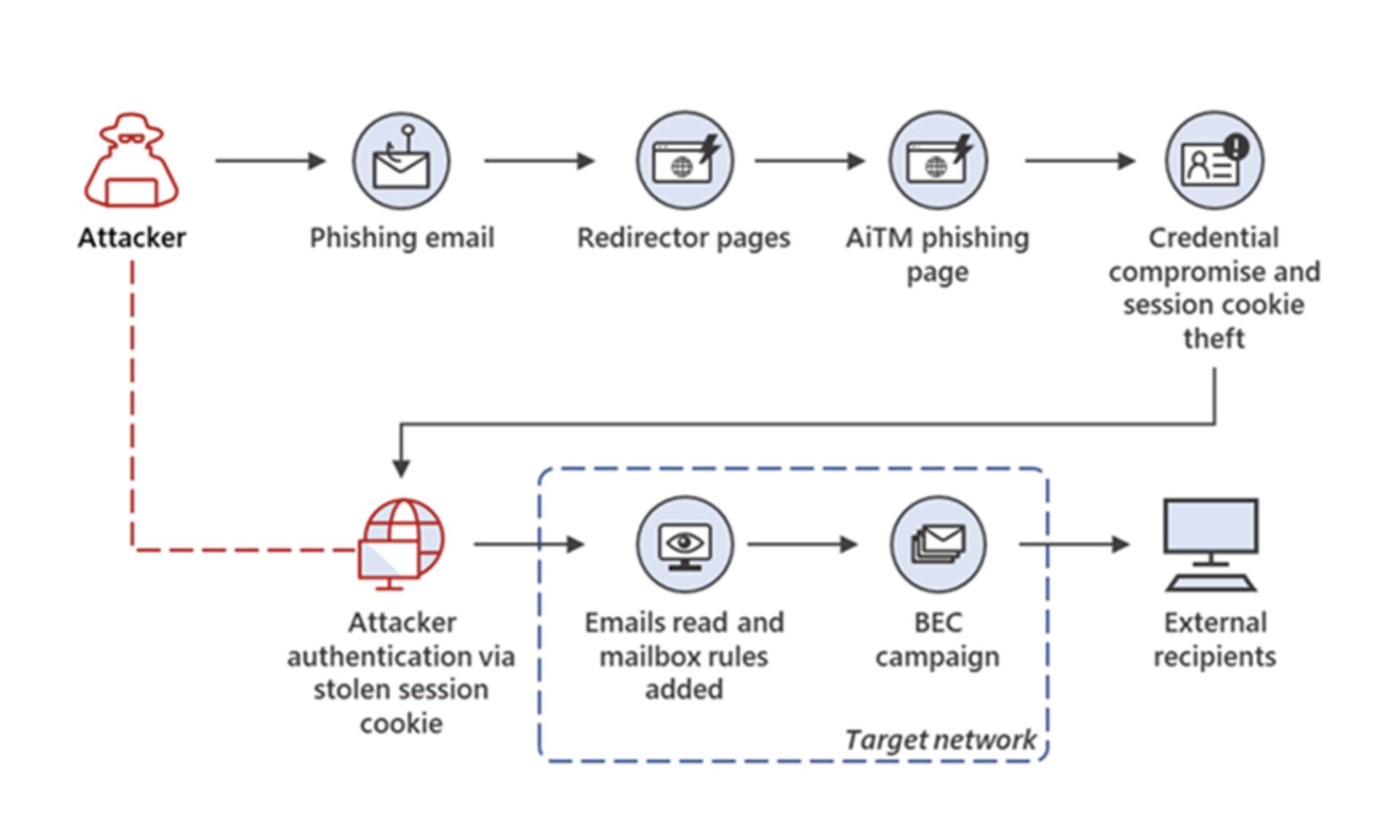
“A large-scale phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA),” an excerpt from the Microsoft site read.
“The attackers then used the stolen credentials and session cookies to access affected users’ mailboxes and perform follow-on business email compromise (BEC) campaigns against other targets,” it added.
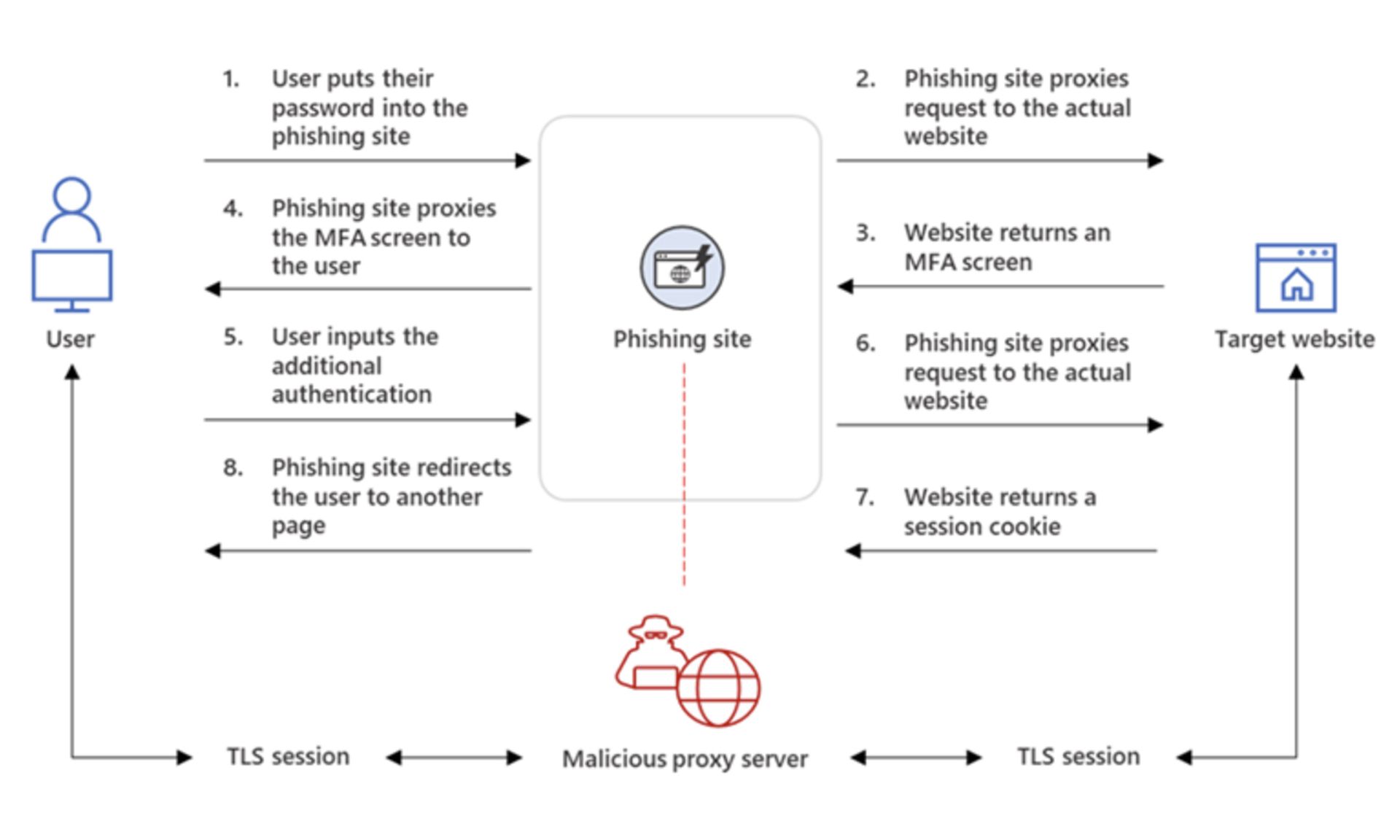
In AiTM phishing campaigns, attackers deploy a proxy server between a target user and the website the user wishes to visit, which the attacker impersonates. This arrangement allows the attacker to steal and intercept the target’s password and the session cookie that proves their ongoing and authenticated session with the website. "Since AiTM phishing steals the session cookie,” Microsoft research concluded, “the attacker gets authenticated to a session on the user’s behalf, regardless of the sign-in method the latter uses,” even with multi-factor authentication.
BEC scams caused more than $43 billion in global financial losses in more than 241,000 incidents between June 2016 and December 2021, based on financial institution filings reported to the FBI’s IC3 unit, according to a notice from the agency in May.
There was a 65% jump in identified global financial losses due to BEC scams between July 2019 and December 2021, according to FBI reports.
“This increase can be partly attributed to the restrictions placed on normal business practices during the COVID-19 pandemic,” according to the FBI’s public announcement, “which caused more workplaces and individuals to conduct routine business virtually.”
Paul Laudanski, head of threat intelligence at Tessian, says that the financial services industry in particular is “often a ripe target for these attacks.” Tessian flagged more than two million malicious emails last year, and financial firms were “the top most impersonated industry,” receiving 19% of all those malicious emails and accounting for 8 out of 10 impersonation attacks, according to Tessian’s recent State of Spear Phishing report.
Laudanski pointed out that the payments and financial industries are among “the more mature and highly regulated and scrutinized sectors today. Generally speaking, payments providers are more likely to be effectively managing this class of risk compared to organizations in other markets,” he added. “That said, no controls are ever perfect and some level of risk always exists.”
For its part, Microsoft found phishing attacks double in 2020, according to its 2021 Microsoft Digital Defense Report. The software giant anticipated that MFA will provide “an added security layer against credential theft, and it is expected that more organizations will adopt it, especially in countries and regions where even governments are mandating it,” according to its blog post. “Unfortunately, attackers are also finding new ways to circumvent this security measure."



