
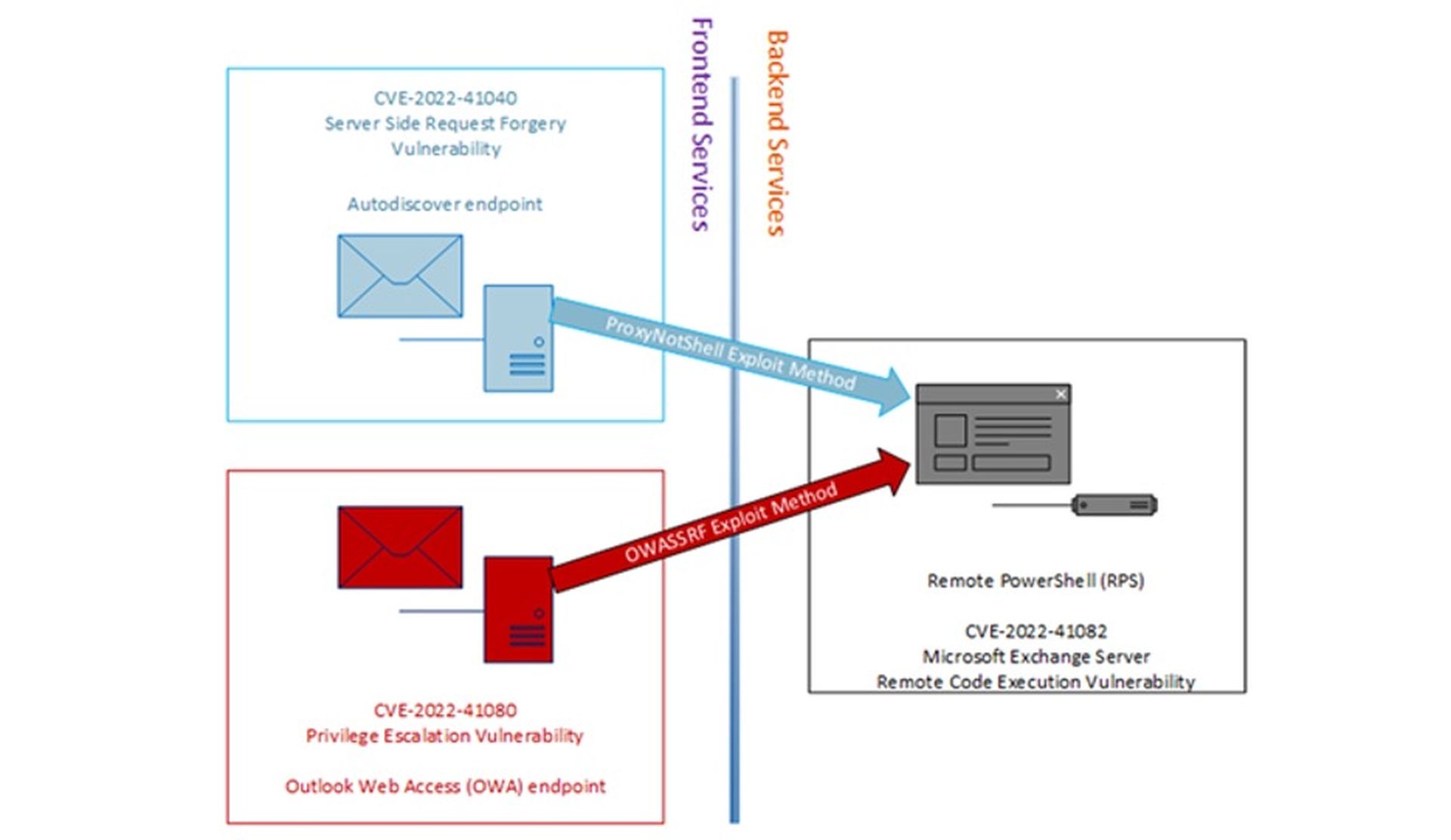
Threat actors affiliated with the Play ransomware strain are leveraging a never-before-seen exploit method that bypasses Microsoft's ProxyNotShell URL rewrite mitigation to gain remote code execution through Outlook Web Access (OWA).
CrowdStrike researchers identified the new exploit (called OWASSRF) during their investigations into several Play ransomware intrusions where the common entry vector was suspected to be Microsoft Exchange ProxyNotShell vulnerabilities CVE-2022-41040 and CVE-2022-41082. The team, however, found that initial access to targeted networks was not achieved by directly exploiting CVE-2022-41040, but was made through the OWA endpoint.
“The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint provided by Microsoft in response to ProxyNotShell,” CrowdStrike researchers said in a Dec. 20 blog post. “[This] seemed to show a novel, previously undocumented way to reach the PowerShell remoting service through the OWA frontend endpoint, instead of leveraging the Autodiscover endpoint.”
While ProxyNotShell exploits CVE-2022-41040, CrowdStrike found that the newly discovered exploit likely takes advantage of another critical flaw tracked as CVE-2022-41080 (CVSS score:8.8) after abusing CVE-2022-41082 for remote code execution.
“After initial access via this new exploit method, the threat actor leveraged legitimate Plink and AnyDesk executables to maintain access, and performed anti-forensics techniques on the Microsoft Exchange server in an attempt to hide their activity,” CrowdStrike added.
CrowdStrike also noted that a proof-of-concept Python script found and leaked by Huntress Labs threat researcher Dray Agha on Dec. 14 may be used by the Play ransomware actors for initial access. This inference is backed up by the fact that CrowdStrike is able to replicate the malicious activity logged in Play ransomware’s attacks using the leaked tooling.
Microsoft has addressed all three vulnerabilities during its Patch Tuesday in November. However, it is unclear whether CVE-2022-41080 was abusing the Microsoft Exchange attack chain as a zero-day exploit alongside the other two critical ProxyNotShell flaws.
“These incidents are fresh evidence of threat actors continuing to take advantage of Microsoft Exchange vulnerabilities and innovate to deploy destructive ransomware,” Thomas Etheridge, chief global professional services officer at CrowdStrike, told SC Media.
A Microsoft spokesperson told SC Media in an email that the new exploit has not applied to the company’s latest security updates, and customers should prioritize installing Nov. 8 patches for Exchange.



