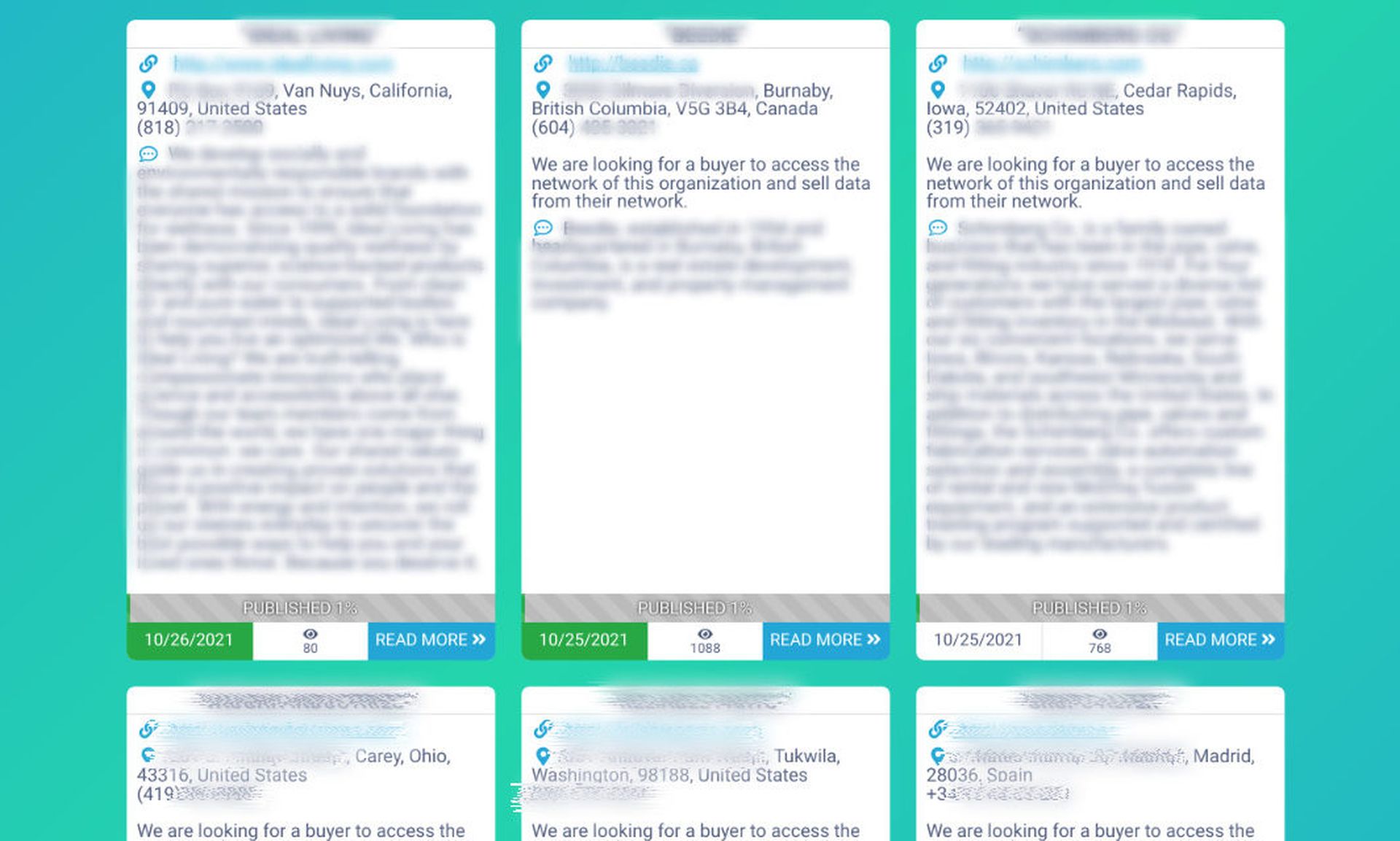
Conti is changing its business model. Rather than post leak data as a threat, Conti is now offering stolen data from victims who have not paid ransoms for sale to outside buyers. It may be the next evolution for ransomware gangs left with boatloads of unmonetized data after victims have become dramatically less likely to pay ransoms over just the past quarter.
"In general, we're just seeing fewer people pay," said Allan Liska, a ransomware expert with Recorded Future. "And so whenever that happens, the ransomware actors sort of try and launch new ventures as far as 'how else can we coerce money out of people or monetize the data that was stolen.'"
Conti's leak site is now checkered with offers to purchase data where leaks once would have been. That includes an American HVAC supplier, a European pharmaceutical and other firms.
While the total dollar amount of ransoms has risen, the percentage of victims infected with ransomware paying those ransoms has declined. The law firm BakerHostetler, which has a significant cyber practice and tracks client trends, has seen a dramatic decline in the number of its clients paying ransoms.
"In 2018 and 2019, over 50 percent [of our victimized clients paid a ransom]," said Ted Kobus, a BakerHostetler partner. "Last year, we averaged below 50 percent. This year, we're averaging below 30 percent."
There may be a number of factors in play for the decline. In fact, with traditional extortion schemes, there would have to be.
Ransomware operators often pursue multiple threats during an attack; they will encrypt files and threaten to leak data. A decline in paying means neither threat was threatening.
On the network end, better preparation could be a factor. The insurer Corvus, for example, believes that is a key reason for a dramatic drop in the number of victimized clients paying any amount of ransom. Corvus takes an active role in ensuring clients have usable offsite backups, which it credits for the lower-than-average need to pay ransom to start with. But improving client backups appears to have further improved results. According to a report released last week, between the second and third quarter of 2021, victimized clients paying ransoms dropped by half, from 24 percent of clients to 12 percent.
"What I get most excited about is we're starting to see that curve happen where the numbers are catching up to organizations who are investing in a more resilient solution to ensure that they can keep pace with the evolving threat landscape," said Jason Rebholz, CISO of Corvus.
At the same time, said Liska and Kobus, ransomware actors may not be doing as good of a job getting to the most damaging data on a network. That could result from better network segmentation or the inexperience of new actors in the threat space. The latter may be manifesting in other ways, too, including failures in the exfiltration process.
While leak posts are up, said Liska, they are not as far up as he would expect given the increase in attacks and decrease in payments. That could be the result of not getting the best files or it could be bureaucratic delays on the part of actors — a backlog of data being prepped for leaks (Liska said it can take some operators months) or hesitancy to leak files during negotiations.
Conti is working unposted files and offers to sell data into its extortion pitch.
A text box on the top of their page now warns victims who have not paid the ransom and do not see their data on the site "this does not mean that we forgot about you, it only means that data was sold and only therefore it did not publish in free access!"