There are a bevy of reasons that ransomware attacks should have declined during the Russian invasion of Ukraine. Squabbles between Ukrainian affiliates and Russian Ransomware designers. Destruction of Ukrainian infrastructure. Enlistments. Fear of boiling the emerging cold war.
But measured by postings to leak sites, ransomware did not decline year-over-year during the war — in fact, it flourished. New data from GuidePoint Security show similar peaks and valleys day-by-day from 2021 to 2022, with 2022 seeing considerably more action overall.
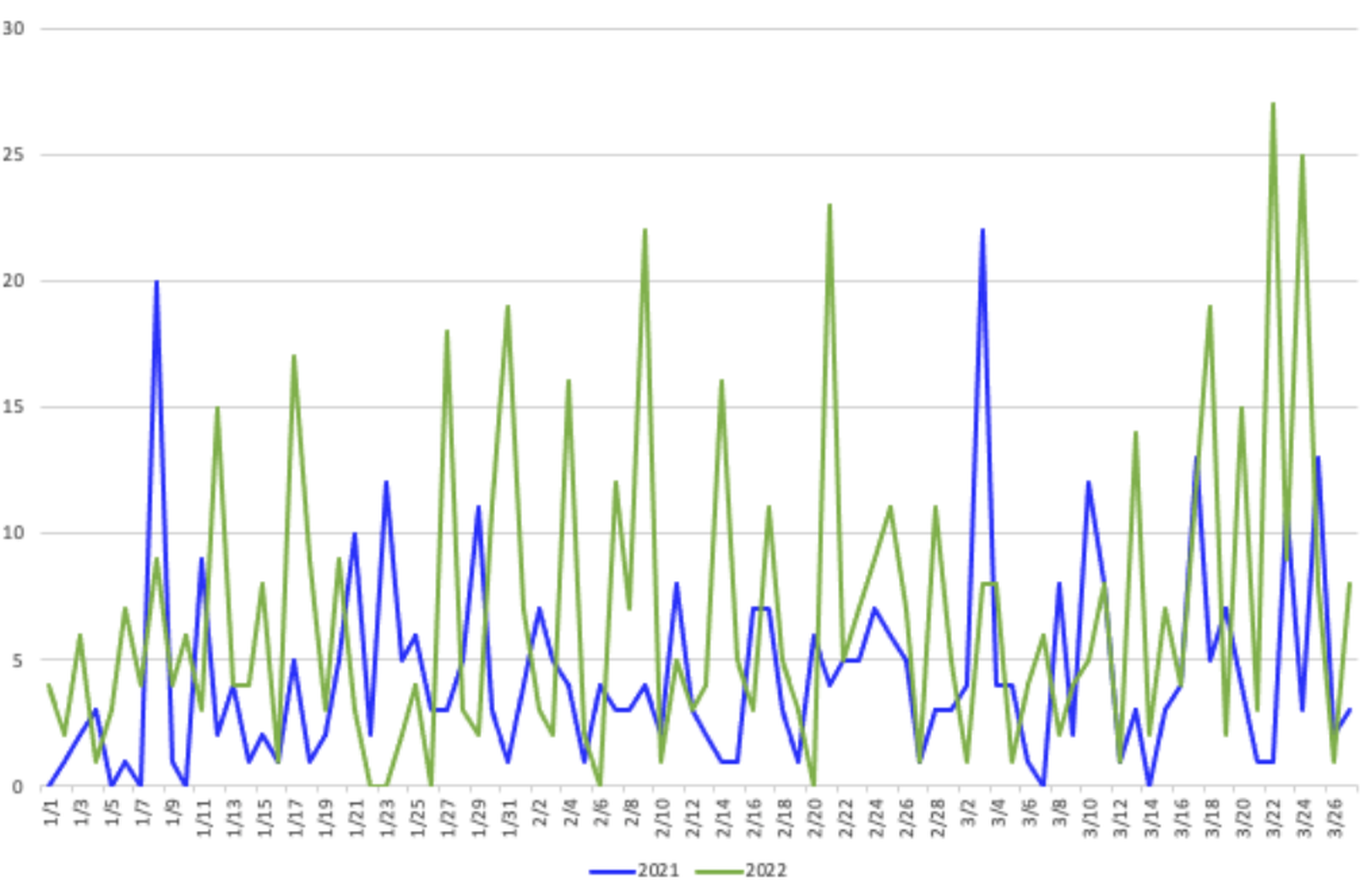
"What we have concluded from the data is that there really hasn't been a slowdown and the amount of ransomware activity from a public leak site posting perspective during the time leading up to, or even after, the conflict started," said Drew Schmitt, ransomware negotiator and principal threat intelligence analyst with GuidePoint.
No ransomware group had more reason to see a decline during the conflict than Conti, who inflamed its affiliates by issuing a threat to the infrastructure of any country that harmed Russia. A member or members of Conti's affiliate chat group leaked internal chats and source code in retaliation, leading the group to dismantle and reconstruct internal systems.
Yet, as researchers have already noted, Conti is flourishing.
Between Jan. 11 and Feb. 23, the eve of the invasion, Conti averaged fewer than one victim post per day, based on GuidePoint's research. It jumped to 1.5 a day from Feb. 24 to March 3, more than 2.5 a day for the week following that.
"One of the hypotheses that we had tackled during this most recent research that a leak of data would have a pretty significant impact on a ransomware group's ability to conduct operations, similar to how any kind of organization that had sensitive data leaked would have an issue," said Schmitt. "What we're seeing as far as the the Q1, 2022, data is that Conti has not had short-term or semi- short term impacts from the leaked data."
Ransomware and all cybercrime with a Russian nexus generally declines between the end of one year and the first week of January, while local criminals celebrate New Year and Orthodox Christmas (Jan. 7), the date observed in Russia. Emsisoft tracked only around half the ransomware submissions to its ransomware identification service in December as it did during last year's peak in July.
That lull may have given the illusion that ransomware is on the decline, when, year over year, this year's Q1 slump may still be outpacing last year's Q1 slump.
For incident responders, even a seasonal decline is a welcome chance to catch their breath.
At the law firm BakerHostetler, which had to start scheduling attorneys to be on call to field ransomware inquiries on a dedicated hotline they set up, the beginning of the year marked the first extended period where no one had to abandon their weekend couch.
"We normally get at least two calls every weekend at least," said Ted Kobus, who heads the Digital Assets and Data Management practice at the firm. "And we went through a period of, I think, four weeks where no one called the hotline over the weekend. That is a big indication that ransomware had decreased."




