Some ransomware groups are shifting focus from financial gains to destructive attacks under growing geopolitical tension and economic turbulence.
According to Dragos Q3 industrial ransomware analysis, ransomware trends are tied to “political and economic reasons,” such as the conflict between Russia and Ukraine and political tensions between Iran and Albania.
Immanuel Chayoya, SonicWall’s threat detection and response specialist, told SC Media that compared with financially motivated ransomware attacks, nation-state threat actors tend to be more destructive in nature. There is evidence that some nations, like North Korea, run or manage their own ransomware operations for financial gain, while hacking groups tied to countries like Iran have been observed deploying ransomware in their own operations.
In September, researchers at Cyderes and Stairwell discovered hints of ransomware groups testing ‘data destruction’ attacks. The data corruption capabilities are linked to Exmatter, a.NET exfiltration tool that has been used as a part of the BlackMatter ransomware attacks.
“Instead of encrypting files for ransomware, attackers corrupt and destroy files,” Chayoya explained. “It is difficult to attribute motivations behind it, but rising geopolitical tensions can be a significant factor contributing to the new tactic.”
The global energy crisis triggered by Russia’s invasion of Ukraine may also lead to an increase in ransomware activities targeting the energy sector, according to Dragos research.
The Colonial Pipeline attack carried out by the Russian-based cybercriminal group DarkSide in 2021 has highlighted an urgent need for the US to defend the country’s critical infrastructure from malicious actors. However, even as subsequent international government and law enforcement actions drove groups like DarkSide underground, new threat actors, such as Ragnar Locker, have become prevalent within the ransomware family.
According to the FBI, RagnarLocker ransomware has targeted 52 entities across ten critical infrastructure sectors as of January this year. In August, it became the ninth most active ransomware gang after attacking the Greek pipeline company DEFSA.
Carl Wearn, head of threat intelligence analysis at Mimecast, told SC Media that the situation might be exacerbated by the onset of winter when European countries work to fill gas storage and ensure heating through the coldest month.
“If threat actors target the energy sector as the winter approaches, victims will have an extra compulsion to pay ransoms as they must get back to work as soon as possible,” said Wearn.
While RagnarLocker ransomware mainly targets the energy sector in Q3, Julian Zottl, chief technology officer of cyber protection solutions at Raytheon Technologies, warned that it could also shift to other industries.
“Ransomware groups will target whatever sectors that are most profitable to them. They go after the energy sector now because of the supply chain shortage, but they may shift to others if the energy crisis is over,” Zottl told SC Media.
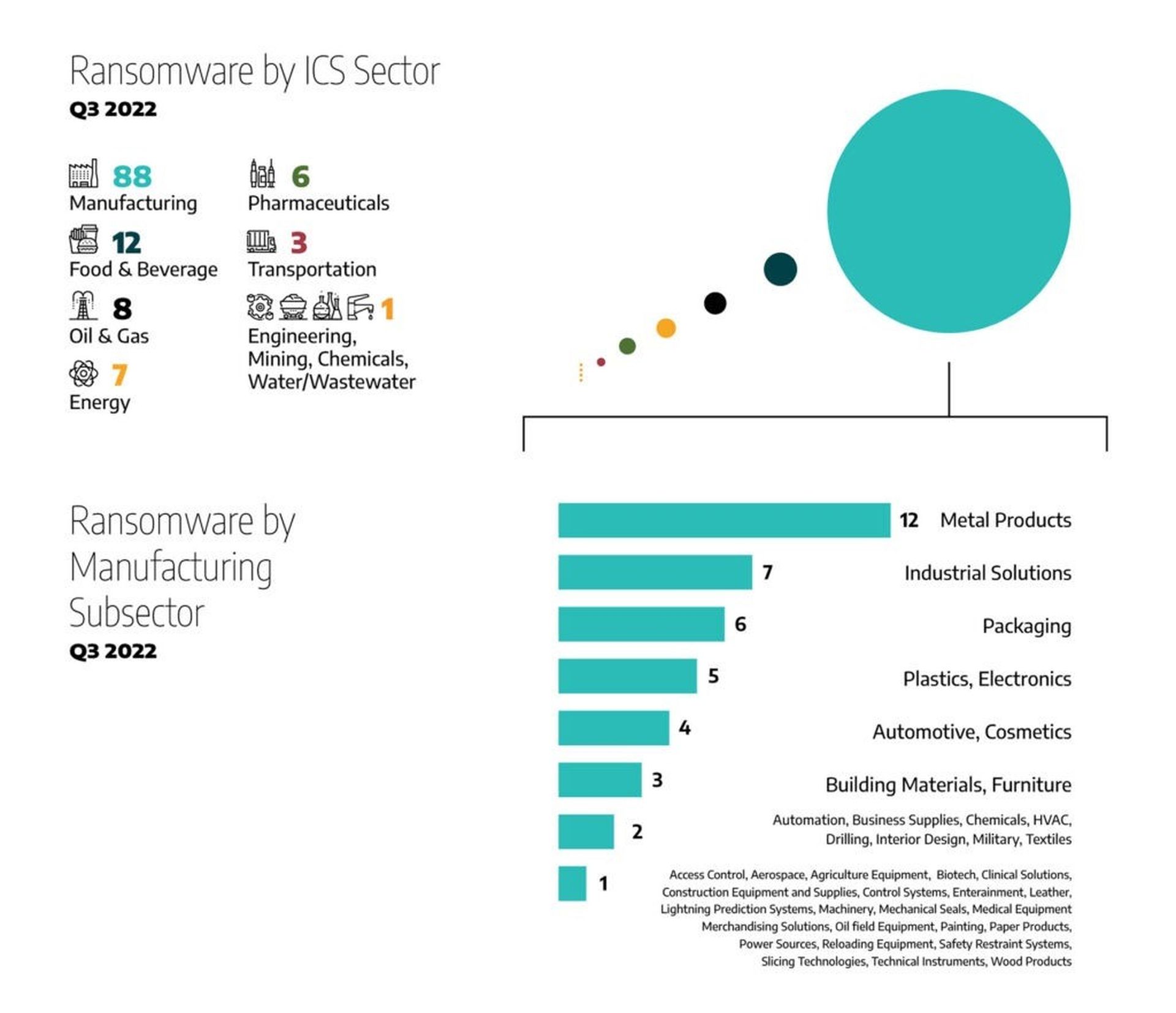
The Dragos report indicates the manufacturing sector remains the most targeted sector in critical infrastructure, with 68 percent of observed attacks, the same percentage reported in Q2. As for other industrial segments, nine percent of attacks targeted the food and beverage sector, followed by six percent targeting the oil and natural gas sector. The energy sector and pharmaceuticals sectors collectively account for 10 percent of attacks.
In terms of changes in ransomware groups during Q3, the report also noted that multiple new campaigns, such as SPARTA BLOG and BIANLIAN, are targeting industrial entities. However, researchers cannot confirm if these groups are reformed from other ransomware groups, such as Conti, who shut down their operation in May.
“While it is quite easy to speculate about whether a new ransomware group has roots in or is reformed from another one, confidence levels surrounding such assessments require deep analysis of the code the ransomware groups use for TTPs such as initial access, credential harvesting, lateral movement, filesystem enumerations, and encryption. It is, therefore, too early for Dragos to determine similarities between groups beyond what is publicly reported,” Tom Winston, director of intelligence content at Dragos, told SC Media.
Dragos researchers warned that besides those new ransomware gangs that emerged in Q3, more groups would appear in the next quarter due to the leaking of LockBit 3.0 builder.
“[We] assesses with high confidence that ransomware will continue to disrupt industrial operations, whether through the integration of OT kill processes into ransomware strains, flattened networks allowing for ransomware to spread into OT environments, or through precautionary shutdowns of OT environments by operators to prevent ransomware from spreading to OT systems,” the report read.




