Federal agencies are concerned about a little-known data extortion group that private researchers have tied to a much larger and well-known criminal hacking group.
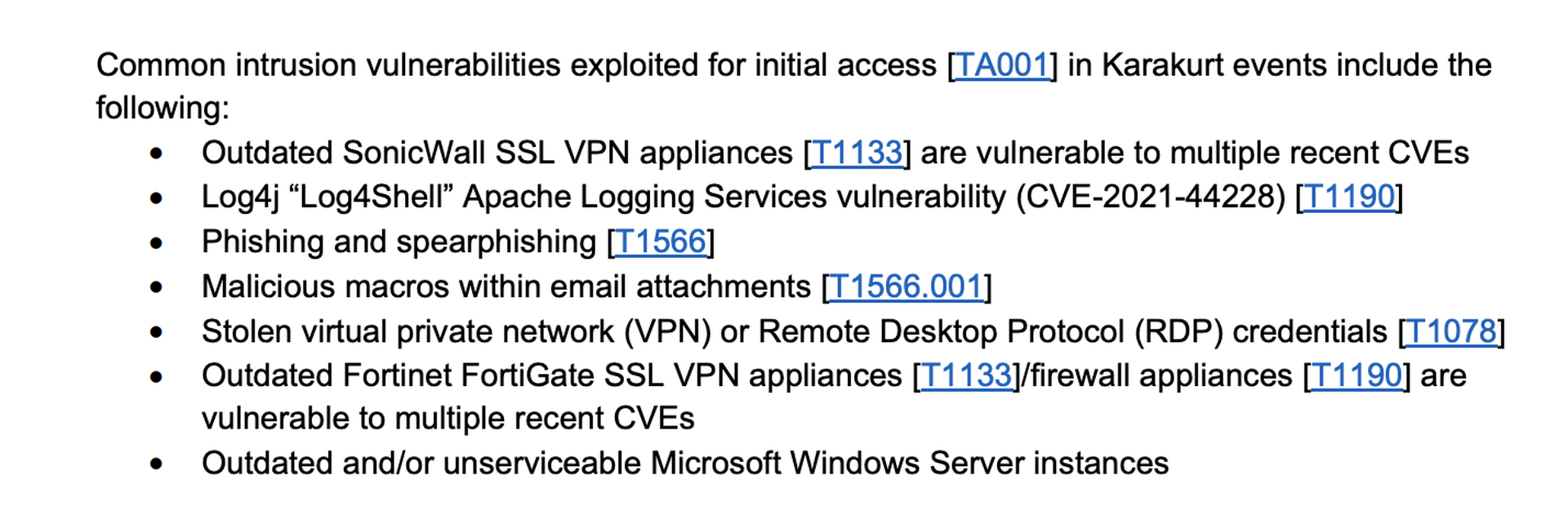
The FBI, Cybersecurity and Infrastructure Security Agency and the Department of the Treasury released a joint alert this week detailing the operations of Karakurt, a small, obscure group that has nevertheless created “significant challenges for defense and mitigation” for businesses and other organizations.
According to the agencies, the group’s targeting appears indiscriminate — not a surprise as many ransomware and data extortion groups are set up to identify and hack vulnerable or unpatched assets wherever they can be found on the internet, regardless of who they belong to or which industry they operate in.
"Karakurt has primarily targeted smaller US-based companies or corporate subsidiaries, although they have also attacked organizations in Canada, the UK, and Germany," said Ivan Righi, a senior cyber threat intelligence analyst at Digital Shadows.
Unlike ransomware groups, Karakurt typically doesn’t bother encrypting devices or systems. They simply steal a company’s data and then rely on the other part of the “double extortion” racket: threatening to leak the information online if the victim doesn’t pay up.
Their ransom demands range as low as $25,000 and as high as $13 million, typically paid through Bitcoin, and victims are often given one week or less to pay before the data is leaked. They’re also known for contacting the employees, business partners and customers of their victims to reveal that their data has been stolen and urge them to put pressure on the company to pay.
Alert intended to head off a new (but familiar) threat?
It’s not clear why the federal government is choosing to highlight this particular group in a joint alert. Karakurt isn’t particularly well-known, prolific or publicly connected to the kind of high-profile hacks that accompanied previous alerts, such as the ones that came out for DarkSide following the Colonial Pipeline hack and for the Conti ransomware-as-a-service operation issued in the midst of at least 400 hacks observed by law enforcement that relied on the malware.
Two ransomware experts told SC Media that while the group’s brand isn’t well-known, they are believed to be a spin-off or partner of Conti. The joint alert does not reference or connect the outfits, but a report from blockchain tracking firm Chainalysis and Tetra Defense last month concluded that Karakurt is “operationally linked to both the Conti and Diavol ransomware groups.”
"Many cryptocurrency wallets used by Karakurt to receive victims' payments were sending money to Conti wallets. It is realistically possible that Conti had formed a business relationship with Karakurt, or that Karakurt was a side business of Conti," said Righi.
With Conti “shutting down” earlier this year, many cybersecurity observers have long expected the group to break up into smaller, quieter teams with different branding. Within that context, the alert could represent an effort by the U.S. government to head off a known threat before it does make the headlines, particularly after the group pledged loyalty to Russia and threatened to attack U.S. and Western infrastructure in the immediate wake of the the Ukraine invasion.
“There is some concern about ties between Karakurt and Conti with the seemingly recent breakup of Conti into smaller groups, it is likely that the team behind Karakurt will roll into one of those groups and share stolen data with that group,” said Allan Liska, a ransomware analyst for Recorded Future. “So, while Karakurt is quiet now, we could see activity from them in the near future.”
Brett Callow, a ransomware researcher at Emsisoft, said that while Karakurt has been seemingly inactive “for a while” (the alert says their leak site has been offline since April) the connections to a damaging group like Conti while it’s in the midst of a rebrand warrant attention.
“As far as I know, the operation has been inactive for a while and the leak sites are offline,” Callow said in an email while stressing that public evidence doesn’t tell the whole story of a group’s impact. “However, as the Conti brand appears to be being closed, perhaps CISA is considered that Karakurt activity will start to ramp up.”