A new ransomware campaign has been targeting transportation and logistics organizations in Ukraine and Poland, according to Microsoft.
The novel ransomware, labeled "Prestige ransomware," was first identified October 11 and targeted numerous victims within the same one-hour window, according to Microsoft's Threat Intelligence Center.
Researchers were not able to tie the strain to any of the 94 active ransomware groups they are currently tracking. The victim profiles share similarity to recent Russian state-aligned activity and overlap with previous victims of HermeticWiper malware, but researchers noted that the campaign is separate from those destructive attacks, which have been targeting Ukrainian organizations since before the Russian invasion began in February. Russia is also one of the global epicenters of ransomware, where many of the top criminal hacking groups are based and maintain an ambiguous and symbiotic relationship with the Kremlin and intelligence agencies.
Microsoft is continuing its investigation and is temporarily tracking the campaign as DEV-0960. The company is also working to notify affected users who have not yet paid a ransom.
Researchers noted that the campaign used three different methods to deploy the payloads across the victims’ network, which is uncommon for ransomware attacks.
“Most ransomware operators develop a preferred set of tradecrafts for their payload deployment and execution, and this tradecraft tends to be consistent across victims, unless a security configuration prevents their preferred method,” MSTIC explained. “For this DEV-0960 activity, the methods used to deploy the ransomware varied across the victim environments, but it does not appear to be due to security configurations preventing the attacker from using the same techniques.”
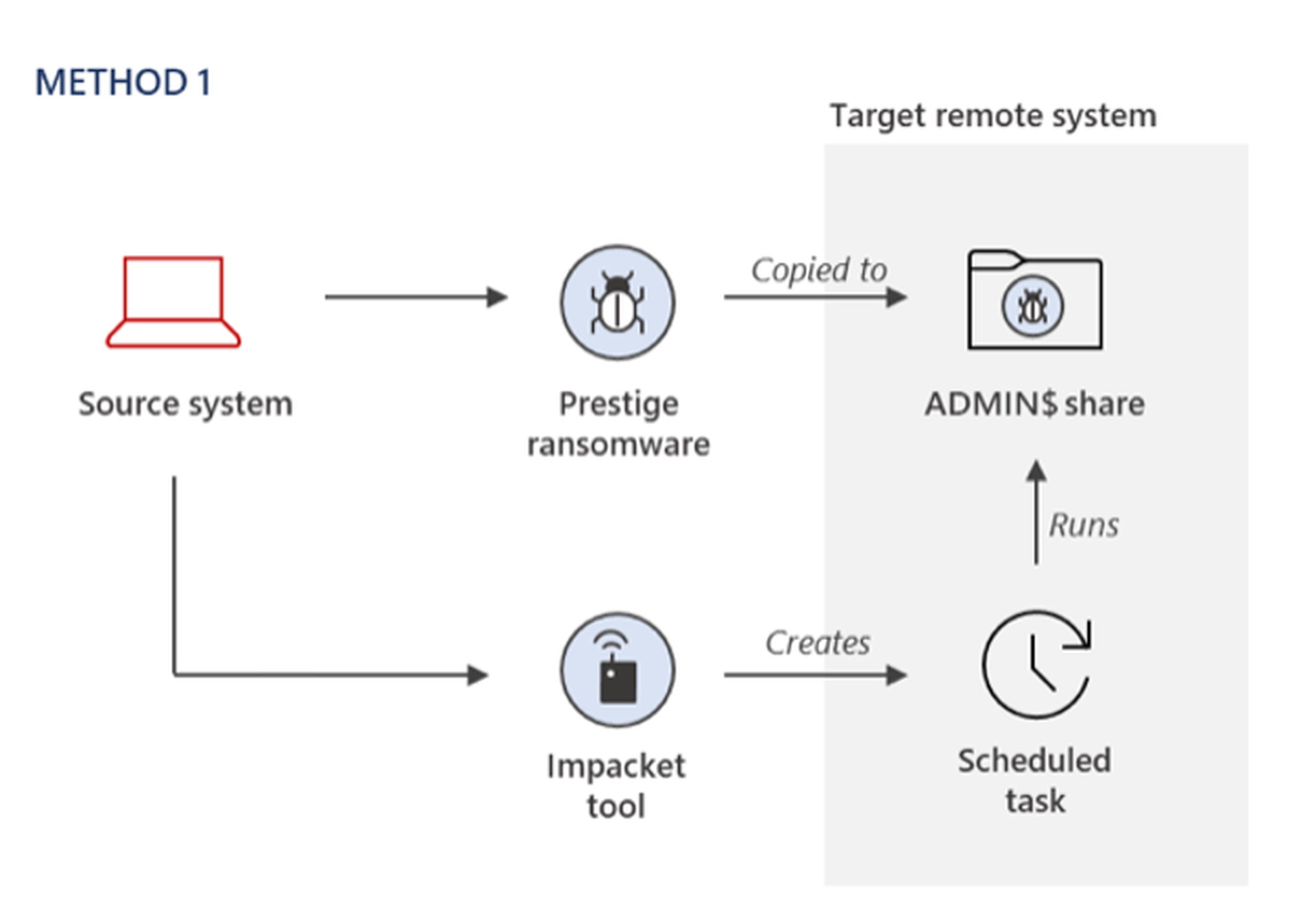
In one method, the ransomware payload is copied to the ADMIN$ share of a remote system, and an Impacket is used to remotely create a Windows Scheduled Task on target systems to execute the payload.
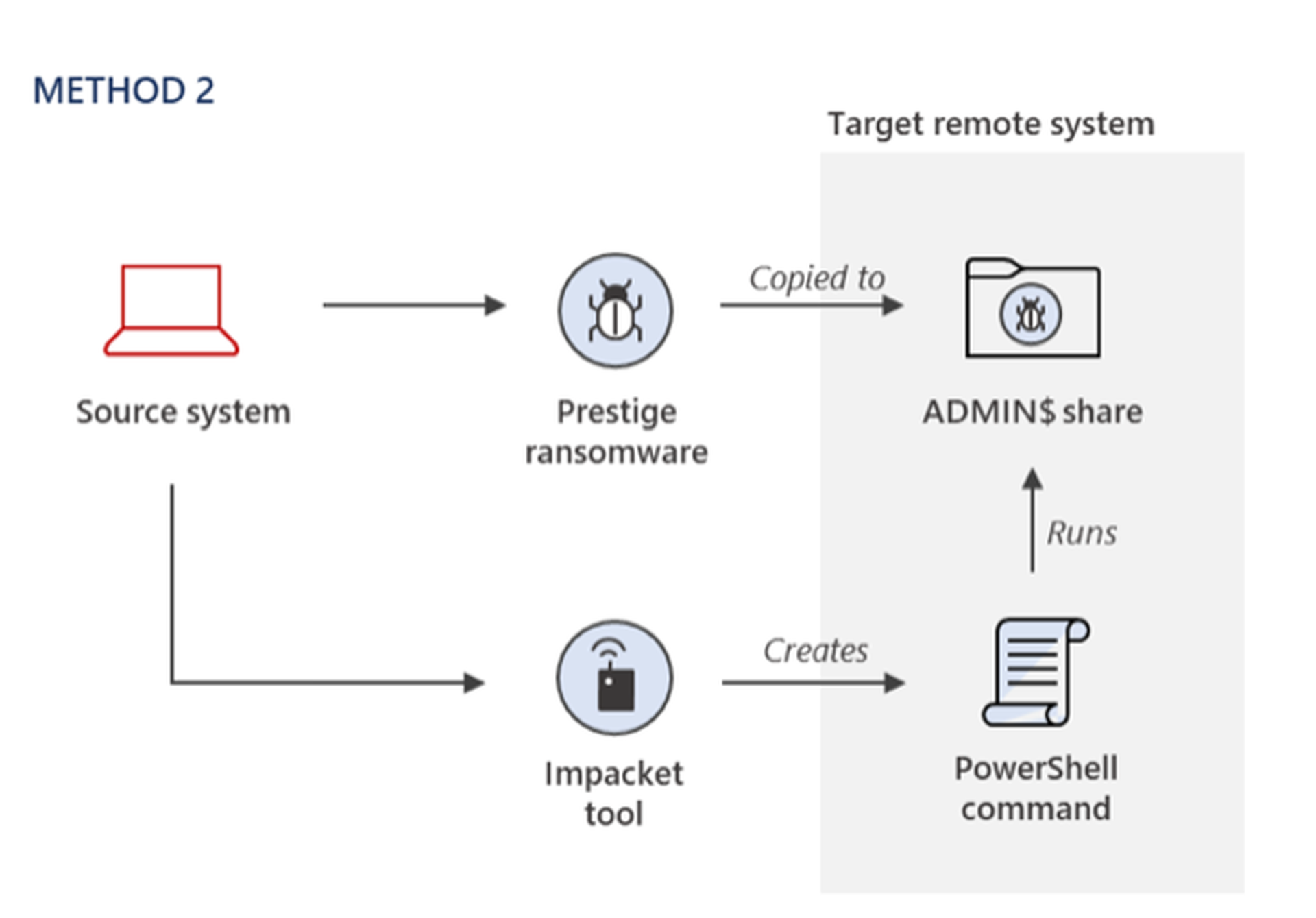
In another, the payload is copied to the ADMIN$ share of a remote system, and Impacket is used to remotely invoke an encoded PowerShell command on target systems.
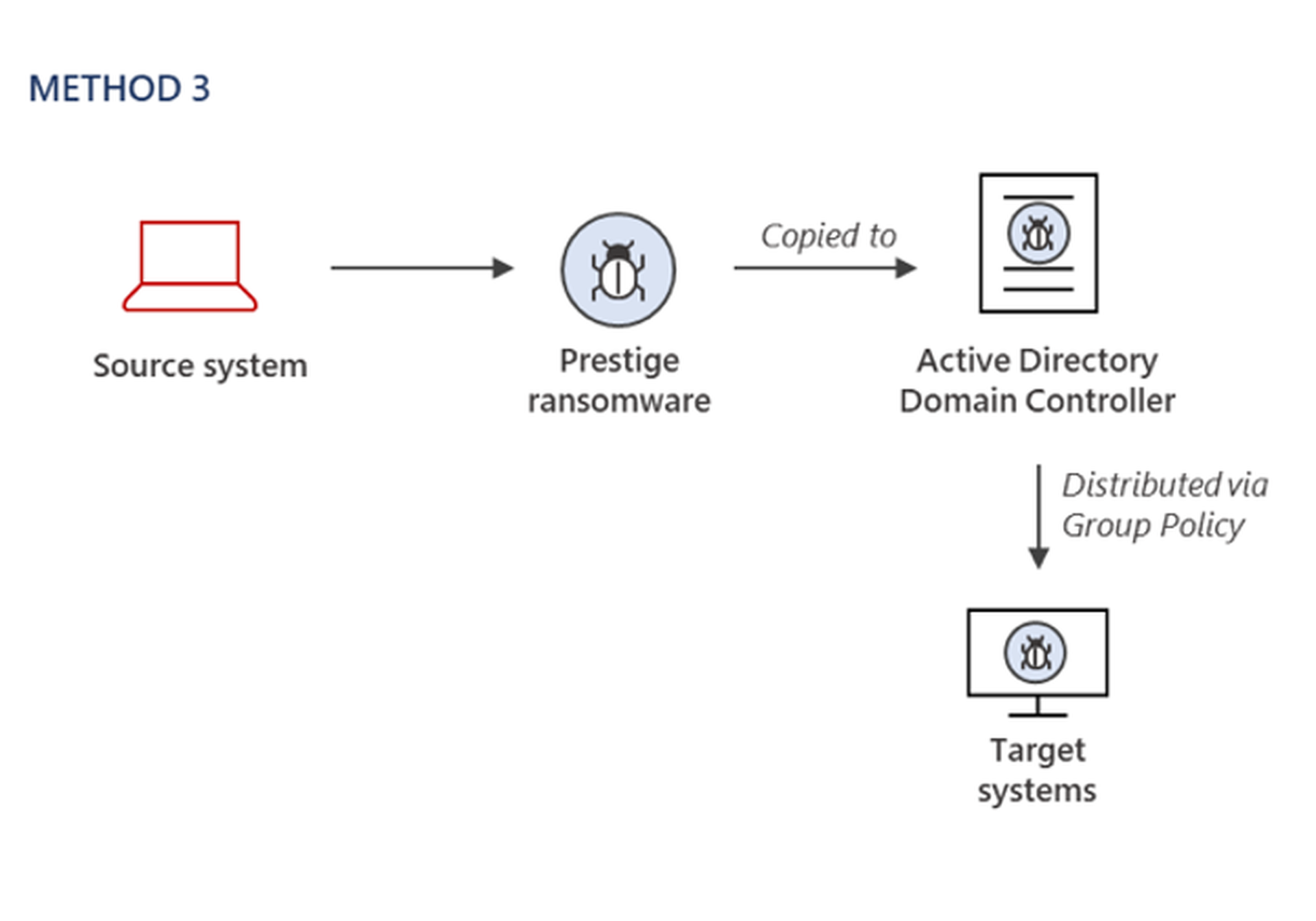
Researchers also found cases where the ransomware payload is copied to an Active Directory Domain Controller and deployed to systems through the Default Domain Group Policy Object.
In response to the complexity of the threat actors, Microsoft recommended several actions to help organizations defend against potential attacks.
The mitigation advice includes blocking process creations that originate from PSExec and WMI commands to stop lateral movement, enabling Taper protection to prevent attacks from stopping or interfering with Microsoft Defender, turning on cloud-delivered protection in Microsoft Defender Antivirus, and enabling multi-factor authentication to enforce any remote connectivity.
“Targeting countries that are assisting Ukraine is a possible next step for Russian cyber actors and represents an escalation of the conflict in this sphere. Neighboring countries are the most likely to be affected," Dick O'Brien, principle intelligent analyst at Symantec's Threat Hunter Team, told SC Media in an email.




