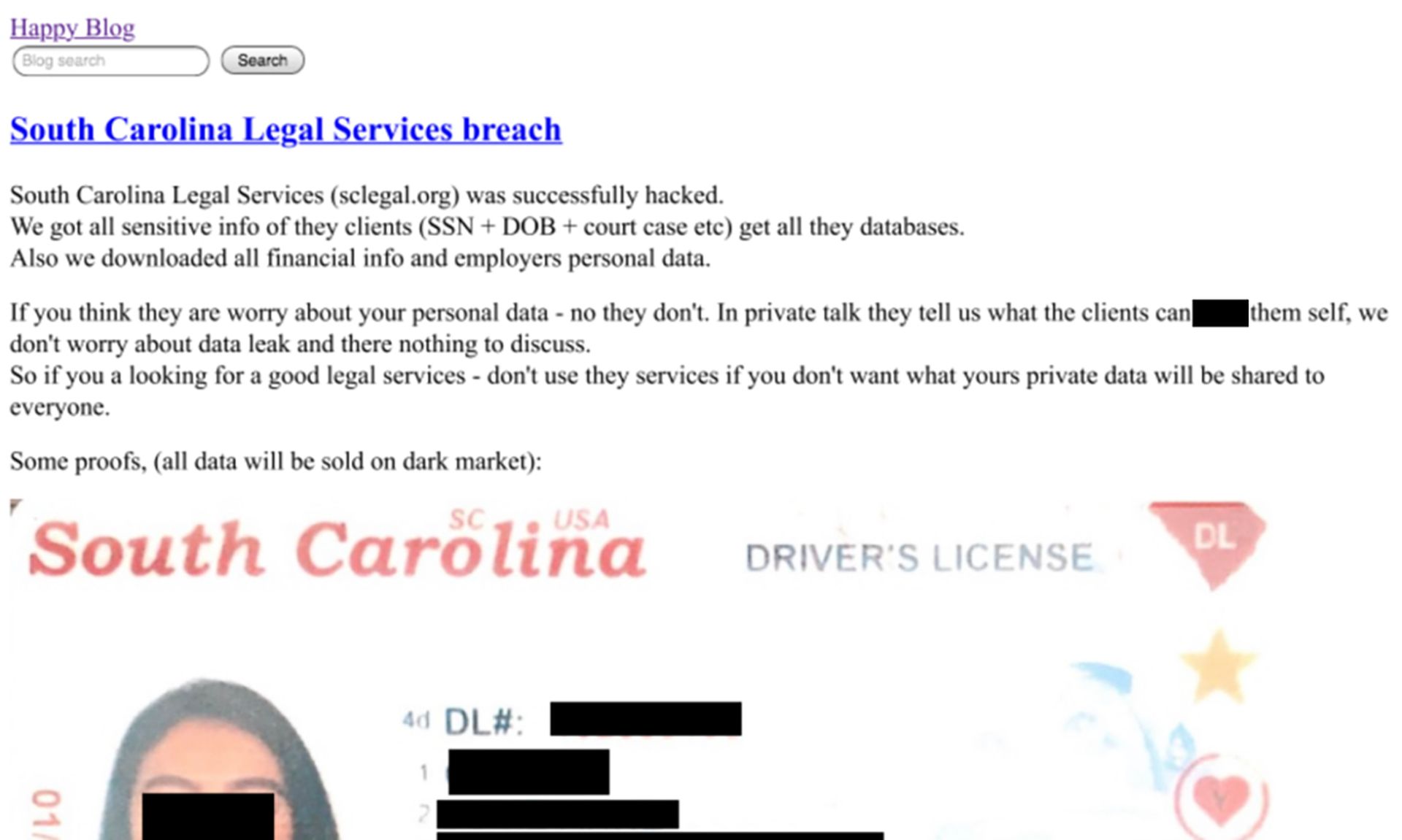
With new samples of REvil malware being discovered in the wild, the noted ransomware group has resumed posting proofs of breaches on its leak blog.
REvil, also known as SODINOKIBI, relaunched its "Happy Blog" last week after months offline. The group went dormant in July after the Kaseya ransomware attacks for reasons as yet unexplained by the group.
A new victim was added for the first time since relaunch on Sept. 11, said Mandiant director of financial crime analysis Kimberly Goody.
"On the same day that these sites reemerged, a message was shared with REvil affiliates stating that the infrastructure had previously been turned off and moved to other servers for safety reasons," said Goody via email. "The threat actor who posted the announcement also highlighted various, minor updates to the SODINOKIBI ransomware.
Mandiant is aware of new samples of REvil malware uploaded to a malware repository as early as Sept. 4. Allan Liska, a threat intelligence researcher at Recorded Future said similar repositories have logged at least two distinct samples of REvil malware over the past week.
The blog now contains a new "proof of breach" post for a United States-based materials company. That company did not respond to requests for comment to confirm the attack or its timeline in relation to REvil's hiatus.
REvil has also established its presence on criminal forums and to "restore its reputation," according to research from Flashpoint. A criminal on the XSS forum "boriselcin" announced on Sept. 8 that an arbitration claim against REvil leader UNKN (pronounced "unknown") on the forum had been settled. Boriselcin had claimed REvil had not paid debts from before the group went underground.
On Sept. 9, a user calling themselves "REvil" signed up for the Exploit forum, claiming to be the new representative for the group, according to Flashpoint. In a post on Sept. 9, later clarified on Sept. 10, that user claimed the Kaseya attacks netted the group around $10 million and provided some explanation for how Kaseya obtained a decryptor without paying ransom. A human error in the key generation process accidentally created a universal key across all the attacks.
"Apparently, when all the decrypters were collected together, people found the universal key among them," wrote REvil, in Russian (as translated by Flashpoint)."
The same actor claims UNKN's whereabouts are unknown, and that it was other group members who restored operations from backups, according to FireEye.
But, wrote "REvil," the group's operations are as trustworthy as ever — at least, for its criminal affiliates.
"No one was scammed. We are in contact with our affiliates, we aren’t hiding anything," "REvil" posted.