Five years ago, a mysterious group of actors leaked a set of tools used by the Equation Group – a moniker security researchers gave to an APT group believed to be tied to the NSA’s elite Tailored Access Operations hacking unit.
It was a damaging loss of capability for the U.S. government, one made all the more embarrassing when malicious hackers were able to refashion one of the leaked exploits, called EternalBlue, into a component of the notorious NotPetya worm that in 2017 wrought devastation to computer systems across the globe.
Now, an Israeli cybersecurity company claims to have found “the Rosetta Stone” for identifying victims compromised by DanderSpritz, one of the leaked tools.
Researchers at Check Point said previous research detailing a Chinese APT leveraging malware code that was nearly identical to code used by the Equation Group a full two years before the Shadow Brokers leak inspired them to continue searching the historical record for other examples.
Was there any evidence that other parties were using the same or similar tools before they were known to be publicly released?
“First of all, we are glad to say the answer is (probably) no. Best that we can tell, APT31’s apparent early access to the leaked exploit was the exception, not the rule,” wrote Itay Cohen, head of research at Check Point. “This makes for a less exciting headline, but should help all of us sleep better at night.”
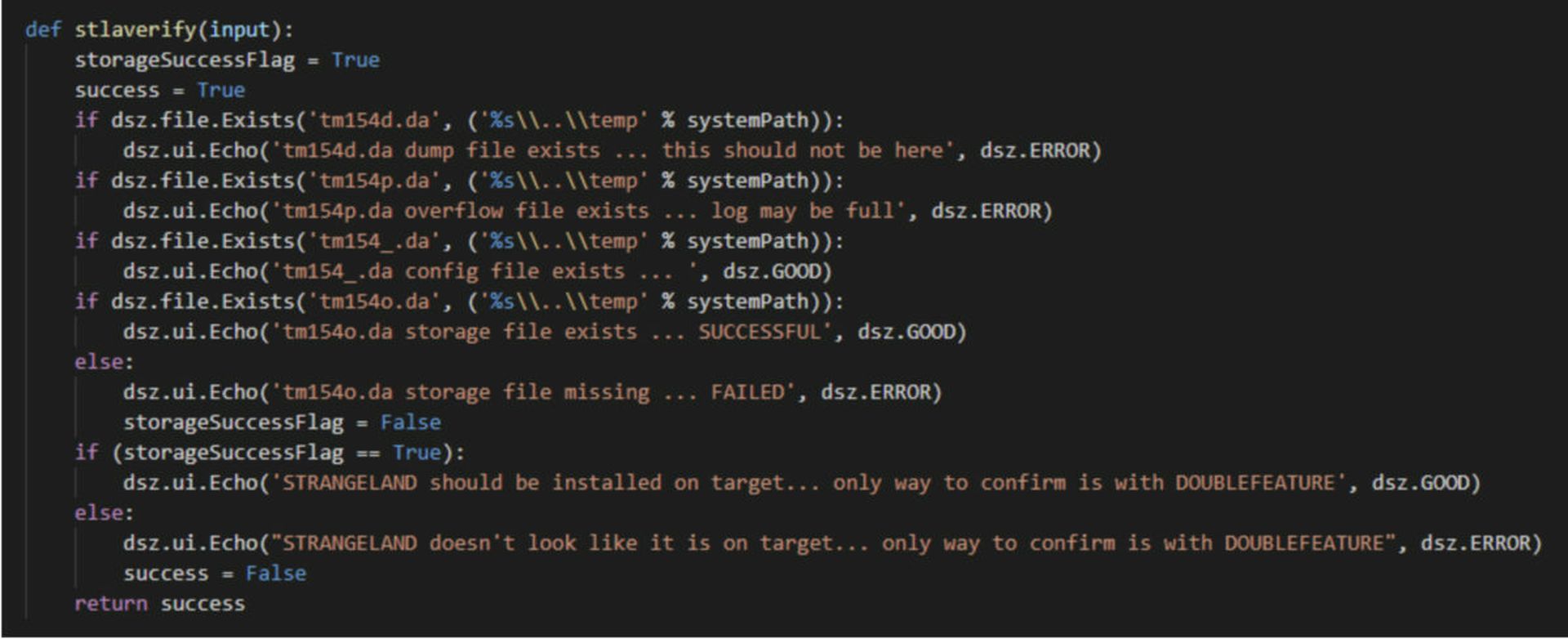
What they did find was a detailed look at a component for DanderSpritz – one of the leaked Equation Group tools – that the company described as “an incident responder’s pipedream" and key to detecting compromised systems in the wild.
The component, called DoubleFeature, acts as a plugin dashboard and diagnostic tool for DanderSpritz. Created in Python, the purpose of DoubleFeature is to scour the victim’s IT environment, generating logs and reports that help the attacker determine what type of tools are best suited for post-exploitation activities on a particular victim’s system.
Internal documentation for the tool claims that DoubleFeature is the only way to confirm a system has been compromised by DanderSpritz. Check Point researchers eventually realized that if this was true, those same capabilities could be turned to the defender’s advantage.
“After some pause, we figured that at least this means DoubleFeature could be used as a sort of Rosetta Stone for better understanding DanderSpritz modules, and systems compromised by them,” the researchers note.
Indeed, that's what they were able to do. Through DoubleFeature, the company was able to uncover new indicators of compromise for several other leaked Equation Group plug-ins, including remote access tool UnitedRake, a data- exfiltration implant called StraitBizarre, a persistence and evasion plug-in called KillSuit, a covert network access tool called FlewAvenue, a validator tool that identifies honeypot environments called MistyVeal and others.
“DoubleFeature effectively, well, doubles as a diagnostic tool for victim machines carrying DanderSpritz — It’s an incident response team’s pipe dream,” Cohen wrote.
The researchers said the technical sophistication of the tooling demonstrates the vast gap in capabilities between the average cybercriminal group and apex predator APTs like Equation Group. However, Cohen noted that the fact that we are still finding out new insights about tools that were released more than four years ago demonstrates that there's much we still don’t know about how they’re being used today or tomorrow.
“Cybercriminals periodically produce the umpteenth Cryptolocker clone or, at most, another modular jack-of-all-trades Emotet wannabe; in the meanwhile, nation-state actors tend to clandestine, gigantic codebases, sporting a huge gamut of features that have been cultivated over decades due to practical need,” he noted. “On the defenders’ side, we have the duty to study these marvels of infosec engineering carefully and apply the lessons learned — before lower-tier, run-of-the-mill attackers do the same.”