As Russia begins its invasion of Ukrainian territories and Western governments continue to warn about the potential or Russian cyberattacks in response to sanctions, U.S. and UK agencies have detailed what they claim is another malware tool used by Russian APT hacking group Sandworm.
Dubbed Cyclops Blink, the malware affects the Executable and Linkable Format (ELF) of Linux operating systems and exploit a Linux API function to download malicious files, execute attacks, maintain persistence on victim networks. A joint advisory from the UK’s National Cyber Security Centre and the U.S. FBI, NSA and Cybersecurity and Infrastructure Security Agency claims the malware has been associated with a botnet known for attacking small and home offices since June 2019.
The agencies do not provide any information or insight into which countries or organizations may have been targeted or compromised by the malware. Cyclops Blink is composed of a core component and four built-in modules that are designed to execute on startup to allow for the uploading and downloading of malicious files, reconnaissance, malware updates and communication with command and control servers.
It also uses a custom binary protocol to communicate with command and control that operates beneath the Transport Layer Security system and encrypts individual messages, making it difficult for defenders to detect or track an ongoing intrusion.
“Cyclops Blink appears to have been professionally developed, given its modular design approach,” the agencies wrote. “A comparison of the core component functionality between the analysed samples indicates that they have most likely been developed from a common code base.”
It’s also designed to use the firmware updating process to maintain persistence on victim devices.
“The developers have clearly reverse engineered the WatchGuard Firebox firmware update process and have identified a specific weakness in this process, namely the ability to recalculate the HMAC value used to verify a firmware update image. They have taken advantage of this weakness to enable them to maintain the persistence of Cyclops Blink throughout the legitimate firmware update process.”
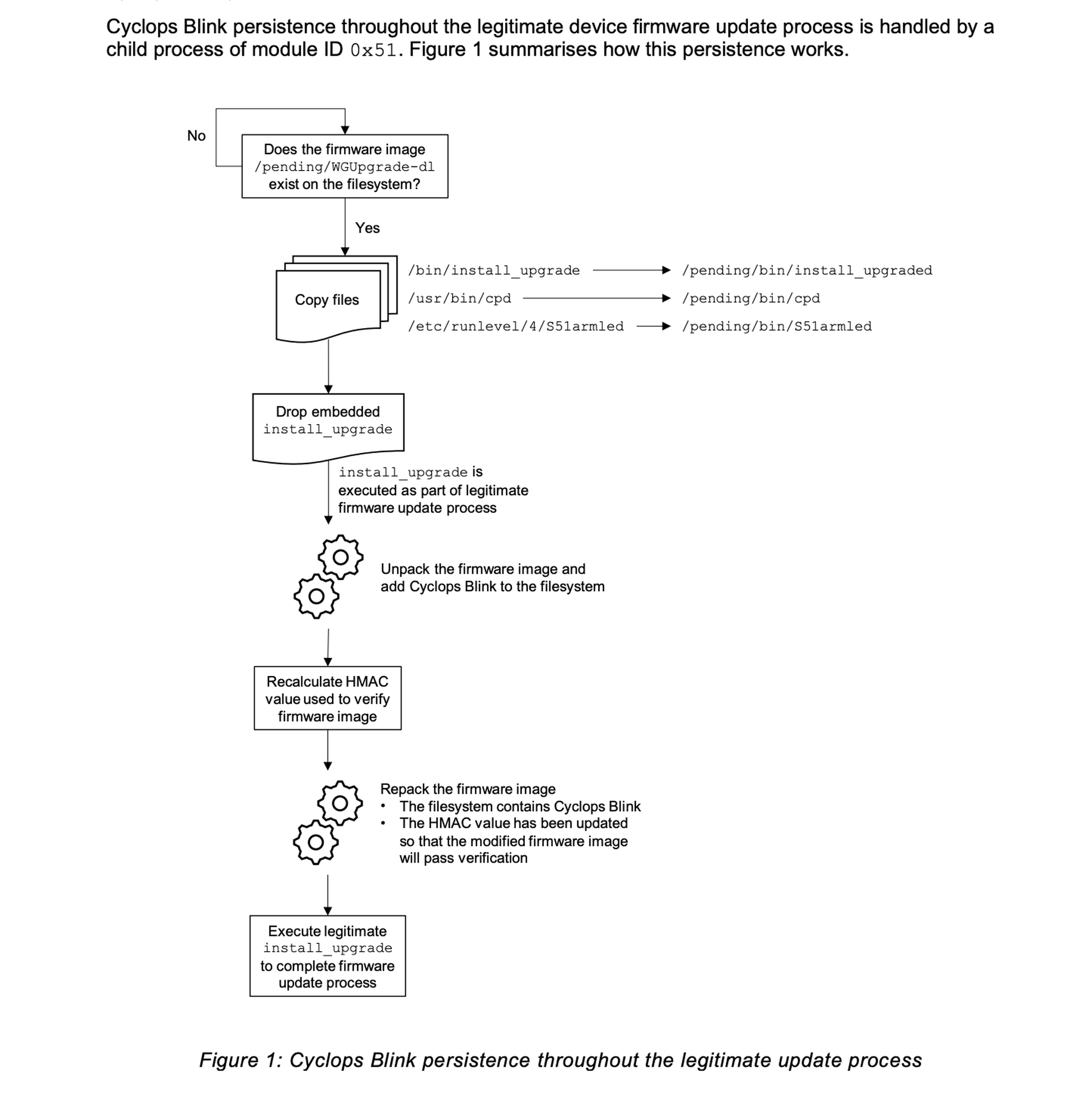
The samples obtained by the U.S. and UK were compiled for the 32-bit PowerPC architecture, but the Western agencies said it is likely that different variations are available for other WatchGuard devices with the same firmware update flaws.
Sandworm is considered one of the most dangerous and capable hacking units tied to the Russian government, and it is believed to be behind the 2017 NotPetya attack, a series of cyberattacks disrupting the Ukrainian electric grid in 2015 and 2016, the spearphishing of world leaders in France, attacks on the IT infrastructure of the 2018 Winter Olympics and other well-known incidents.
That history positions Sandworm at the forefront of concerns floated by Western governments and security research firms in recent months that Russia could seek to respond to Western government sanctions by levying disruptive cyber attacks against industry and governments.
“The timing of this revelation couldn't have been much better,” wrote Mandiant’s John Hultquist on Twitter reacting to the disclosure. “Sandworm is a player we are very concerned about given their history as the premier Russian cyberattack capability. It's a great time to get smart on this actor.”
While officials have claimed that a response from Russian hacking groups is possible, both the U.S. and UK governments have tempered those warnings with qualifiers that there is no intelligence indicating an imminent attack or campaign.
"There are no specific credible threats to the U.S. homeland that we know of currently, [but] we all recognize that threats to our digital infrastructure are, of course, not bound by national borders, and we saw that very starkly in July of 2017" during the NotPetya attacks, CISA Director Jen Easterly said last week.




