For years, Chinese hackers have been using previously known vulnerabilities for network devices to compromise telecoms in a wide-ranging espionage campaign, the U.S. government warned this week.
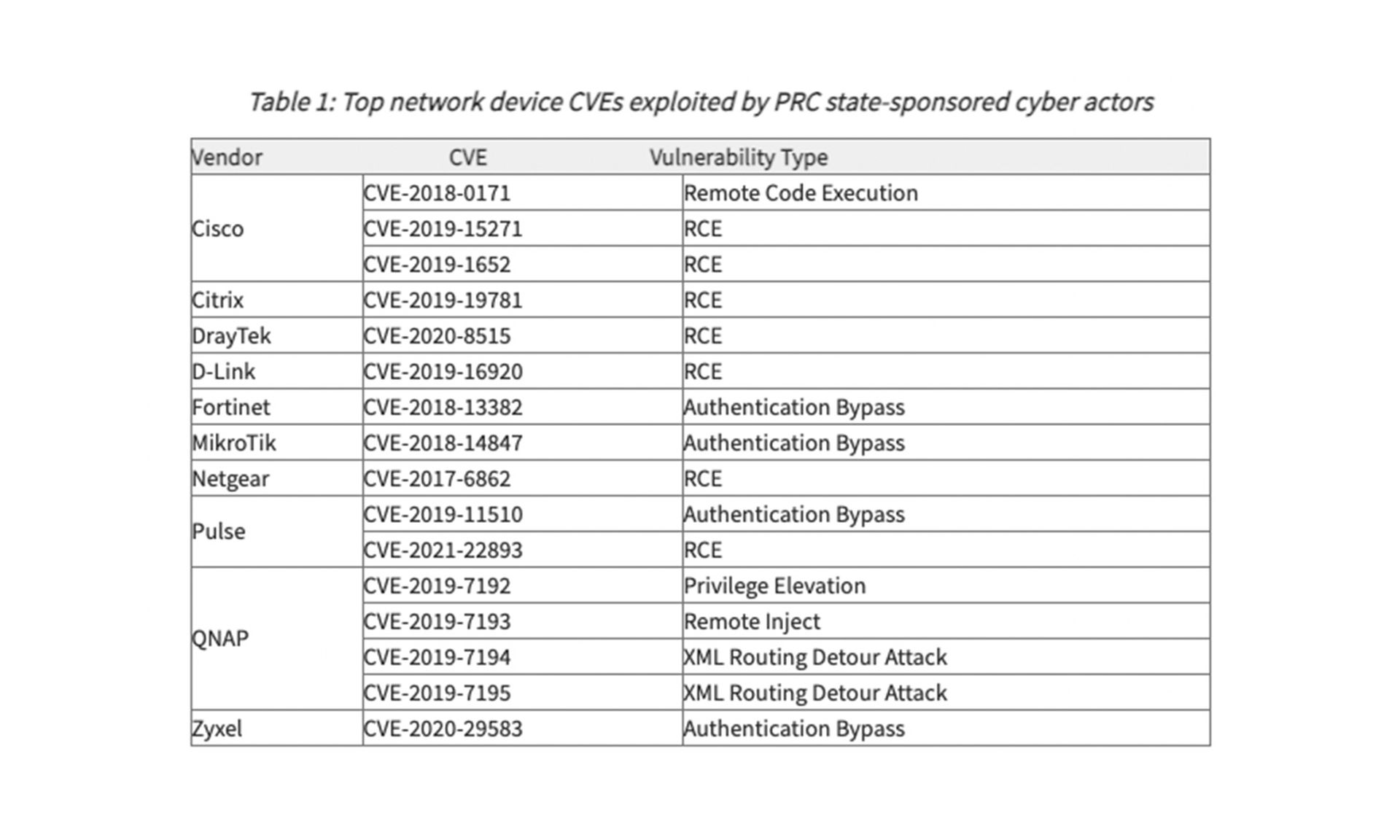
In a joint advisory this week from the Cybersecurity and Infrastructure Security Agency, the FBI and the National Security Agency, officials highlighted 16 common vulnerabilities in networking devices across 10 different vendors like Cisco, Citrix and Fortinet, saying threat groups working for Beijing have been using them to hack into telecommunications companies and network providers. The purpose behind these intrusions, according to the agencies, was to establish “a broad network of compromised infrastructure.”
“Since 2020, PRC state-sponsored cyber actors have conducted widespread campaigns to rapidly exploit publicly identified security vulnerabilities, also known as common vulnerabilities and exposures (CVEs),” the agencies warned. “This technique has allowed the actors to gain access into victim accounts using publicly available exploit code against virtual private network (VPN) services or public-facing applications without using their own distinctive or identifying malware — so long as the actors acted before victim organizations updated their systems.”
Click here for all the coverage coming out of RSAC.
Leveraging previously publicized vulnerabilities to attack unpatched systems is common among many advanced persistent threat groups (APTs), but officials say these hackers have also shown remarkable resilience and flexibility that allows them to evade detection from U.S. private sector network defenders, often matching custom hacking tools with publicly available ones that are native to the victim’s local IT environment.
“These cyber actors are also consistently evolving and adapting tactics to bypass defenses. NSA, CISA, and the FBI have observed state-sponsored cyber actors monitoring network defenders’ accounts and actions, and then modifying their ongoing campaign as needed to remain undetected,” the agencies wrote.
The alert provides no details as to which telecoms and network providers have been compromised or where they operate, but the fact that three U.S. agencies wrote and developed it could indicate the actors are targeting U.S. domestic entities. Access gained on telecom networks today could be used to facilitate future attacks and campaigns against U.S. industry, governments and critical infrastructure tomorrow.
The warning came the same day that officials from the Department of Justice and FBI acknowledged that disrupting domestic command-and-control infrastructure known to be used by foreign hacking groups, including some cases where that infrastructure is owned by a U.S. private entity, is “the future” of U.S. law enforcement efforts to blunt the impact of damaging cyberattacks on U.S. society.
Last year the FBI raised eyebrows when it secured a court order to remove malicious webshells from private unpatched Microsoft Exchange servers that Chinese hackers and other actors exploited to compromise swaths of public and private organizations. The servers had gone unpatched for months after the Exchange vulnerabilities were publicized ,and U.S. officials said it was a benign move meant to prevent future attacks. Still, it raised eyebrows about the government’s increasing willingness to touch private sector IT infrastructure when pursuing foreign hackers.
“I think I heard Director [Christopher] Wray make an analogy to the post 9/11 transformation that the FBI went through and it was clear that we were no longer going to be solely focused on investigating crimes after the fact, but using our unique position in terms of being involved in law enforcement and the lead domestic intelligence agency in the United States to act, to take action to disrupt threats and prevent them wherever possible,” said FBI assistant director Tonya Ugoretz at the RSA Conference in San Francisco. “That is not wholly new but I think the analogy does apply somewhat to how we’re looking at cyber.”




