Ask any security practitioner what causes them the most pain and endpoint security will surely be somewhere near the top of the list. This is especially true in the last two years, amid a pandemic that forced a massive shift to remote work, creating many more endpoints to keep track of.
“The endpoint is the key security battleground,” says Jonathan Gohstand, Director of Technical Marketing and Security at HP Wolf Security. “It’s where people, data, and the Internet meet. Organizations invest a lot in endpoint security, since that’s still where most attacks originate. Clearly, security teams have not ‘solved’ the endpoint security problem.”
Endpoint security must be made as efficient as possible to reduce costs, minimize user experience issues and reduce operational complexity, he says. Endpoint isolation is the way to do this, but many people are unfamiliar with the technology.
Gohstand says there are three key components to endpoint isolation. This article focuses on the second one: introspection of tasks.
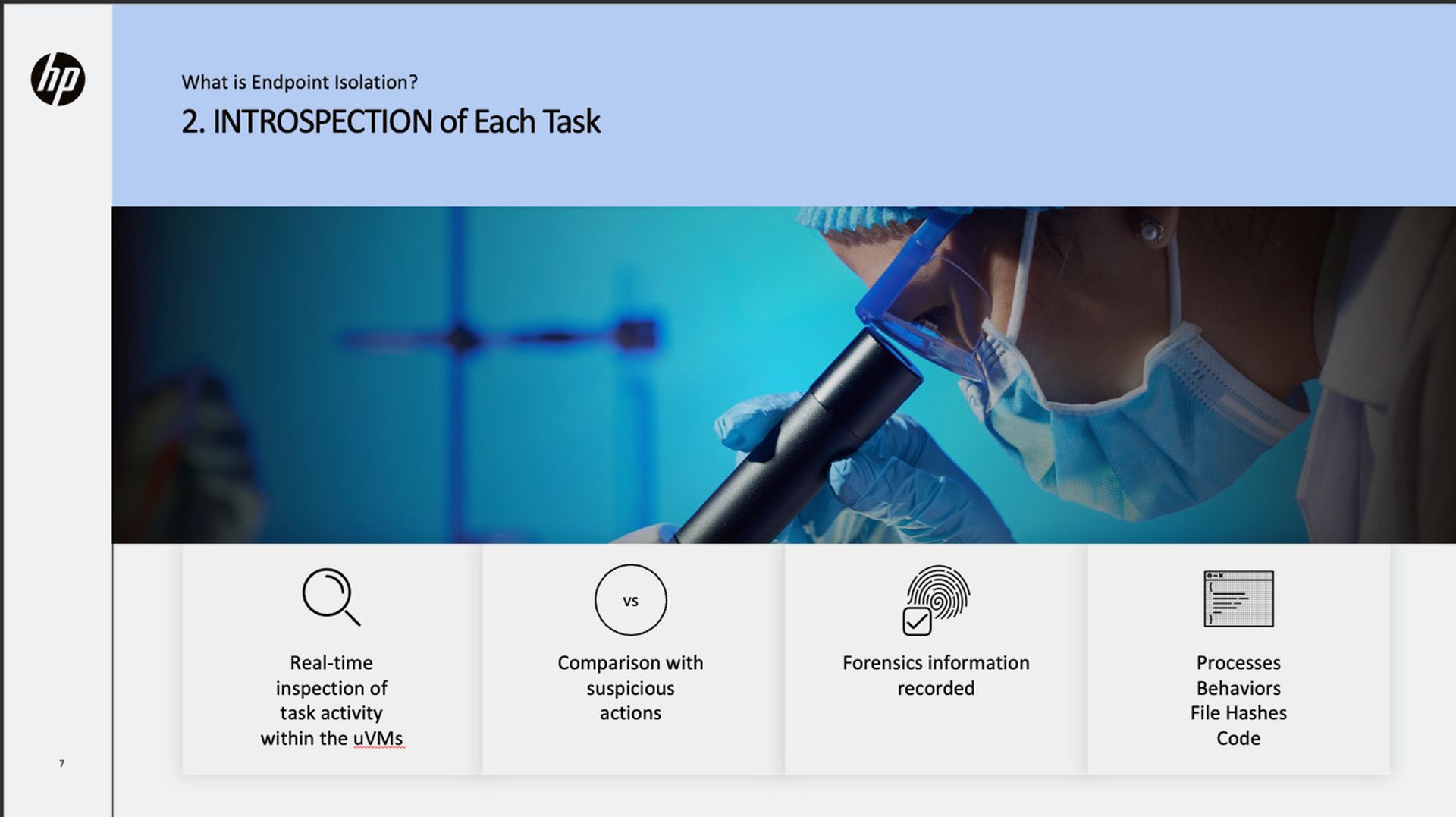
With introspection of tasks, real-time inspection of task activity occurs within the uVMs, examining processes called, comparing suspicious actions, recording forensics information and processing behaviors.
Unlike sandboxing, it leverages the actual endpoint environment, including user interaction with the malware.
This makes malware execution far more accurate providing better data for analytics.
Value propositions
Here are just a few of the benefits of endpoint isolation, according to Gohstand:
Inherent protection:
- Zero Trust is achieved because all untrusted sources run within an isolated space on the endpoint. Nothing received is assumed to be trustworthy.
- It doesn’t rely on detecting anything – it inherently protects.
- It protects against attacks leveraging both corporate and personal vectors, including personal email accounts.

Accuracy
- Isolating tasks in a realistic execution environment catches what other approaches miss.
- Catches malware that requires user interaction to activate
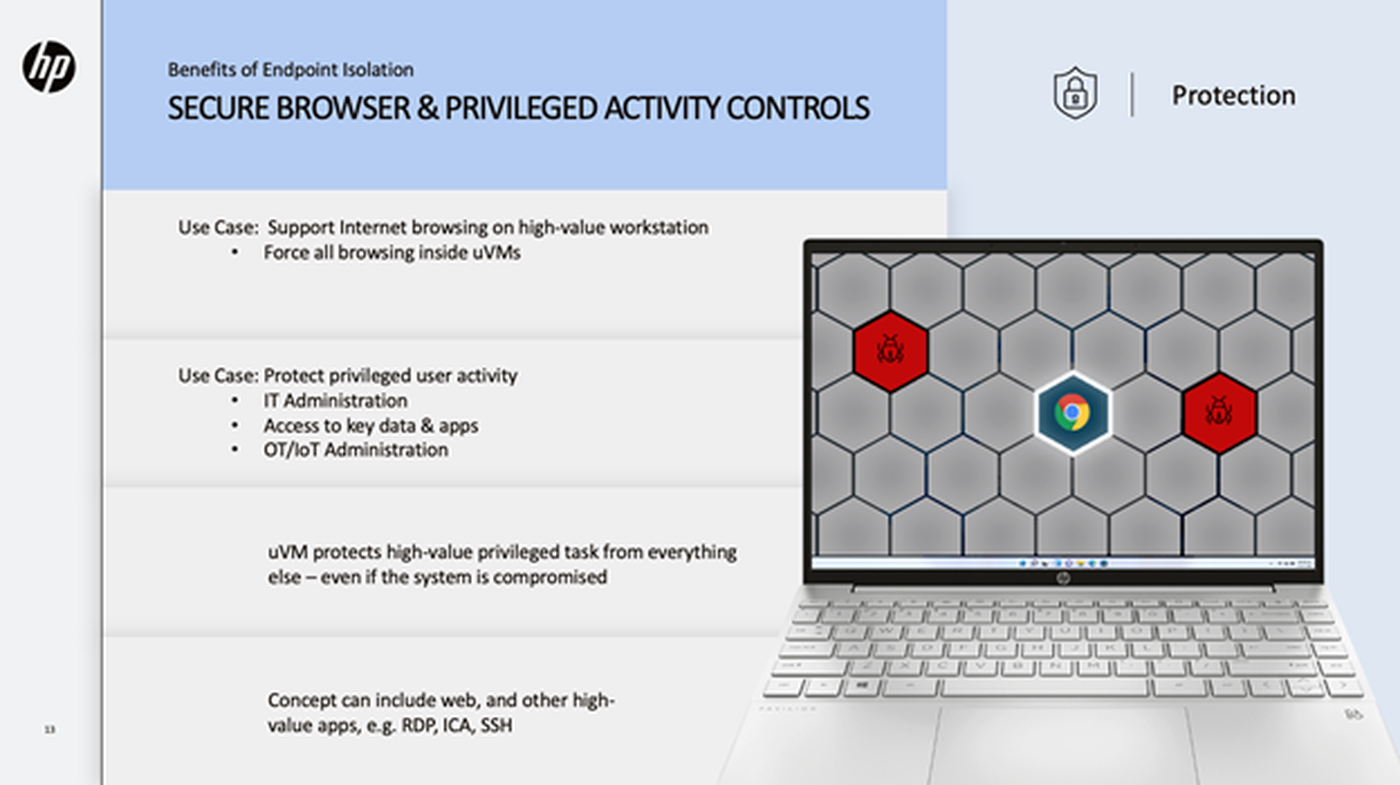
Secure browser and privileged activity controls
- Force all browsing activity inside uVMs allowing a PC to both access sensitive data and be used for personal web browsing
- Isolate and protect privileged user activity (IT administration, access to key data and apps and OT/IoT administration) from everything else on the machine – even if the system is compromised
- Isolate privileged activity using web portals, Citrix ICA, RDP and SSH.
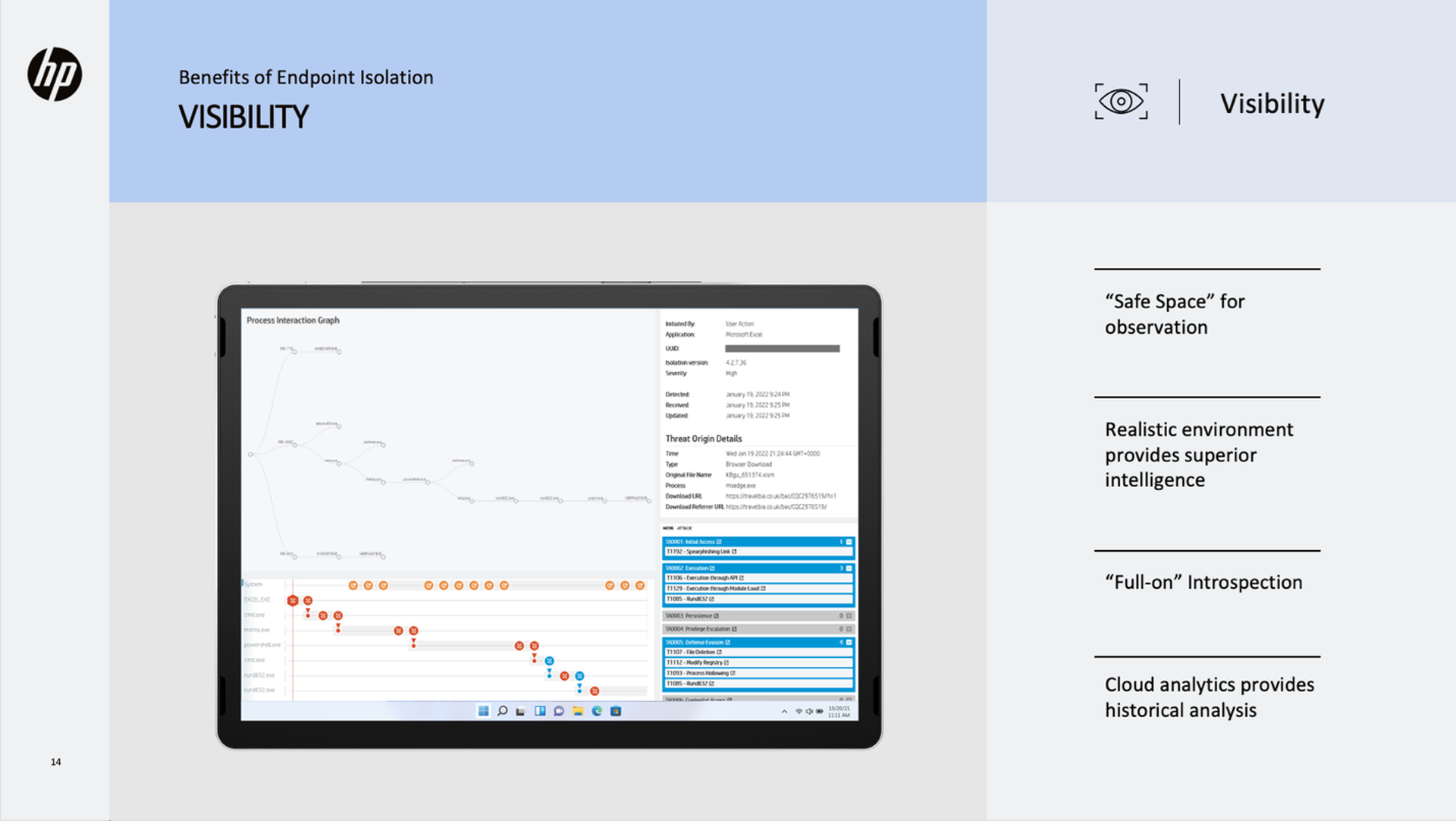
Visibility
- Safe space for executing malicious code
- A realistic environment for suspicious code providing superior threat intelligence
- Full-on introspection: full forensics on malware TTPs
- Cloud analytics for historical analysis
Security Efficiency
- Reduce support tickets, especially high-priority tickets
- Decrease endpoint remediation with fewer false positives
He also cites other benefits, including not compromising user experience, removing the need to use a sandbox, and more efficient compliance controls. Click here for details on HP Wolf Security’s approach to endpoint isolation.



