Note: This story and headline have been updated on 2/16/2023 and 2/17/2023 following new information and statements from both Atlassian and Envoy.
Australian software company Atlassian confirmed that employee data has been leaked on the web through an account they use on a third-party application. While independent researchers at cybersecurity firm Check Point have backed up claims that the data does not appear to have come from Atlassian's systems, the makers behind the app say an Atlassian employee's compromised credentials are to blame.
In a statement sent to SC Media, an Atlassian spokesperson said the leak appears to have originated via their acount with Envoy, which makes and sells workplace collaboration software.
“On February 15, 2023 we learned that data from Envoy, a third-party app that Atlassian uses to coordinate in-office resources, was compromised and published. Atlassian product and customer data is not accessible via the Envoy app and therefore not at risk,” the spokesperson told SC Media. “The safety of Atlassians is our priority, and we worked quickly to enhance physical security across our offices globally. We are actively investigating this incident and will continue to provide updates to employees as we learn more.”
After SC Media reached out to Envoy for comment, a spokesperson sent a statement saying the company is not aware of any evidence that their systems were breached, claiming their own research indicates the incident stemmed from a compromise of an Atlassian employee's credentials.
"We’re investigating this right now and are not aware of any compromise to our systems. Our initial research shows that a hacker gained access to an Atlassian employee's valid credentials to pivot and access the Atlassian employee directory and office floor plans held within Envoy’s app," the spokesperson wrote.
In an update Friday, an Envoy representative told SC Media they found log evidence of requests confirming that hackers obtained valid user credentials from an Atlassian employee account and used that access to download the affected data from Envoy’s app. The representative also claimed no other customer data was stolen.
An Atlassian's representative also reached out to confirm that the leak began with compromised credentials.
"We learned the hacking group compromised Atlassian data from the Envoy app using an Atlassian employee’s credentials that had been mistakenly posted in a public repository by the employee. As such, the hacking group had access to data visible via the employee account which included the published office floor plans and public Envoy profiles of other Atlassian employees and contractors," the spokesperson wrote. "The compromised employee’s account was promptly disabled early in the investigation which was proven effective in eliminating any further threat to Atlassian’s Envoy data. Atlassian product and customer data is not accessible via the Envoy app and therefore not at risk."
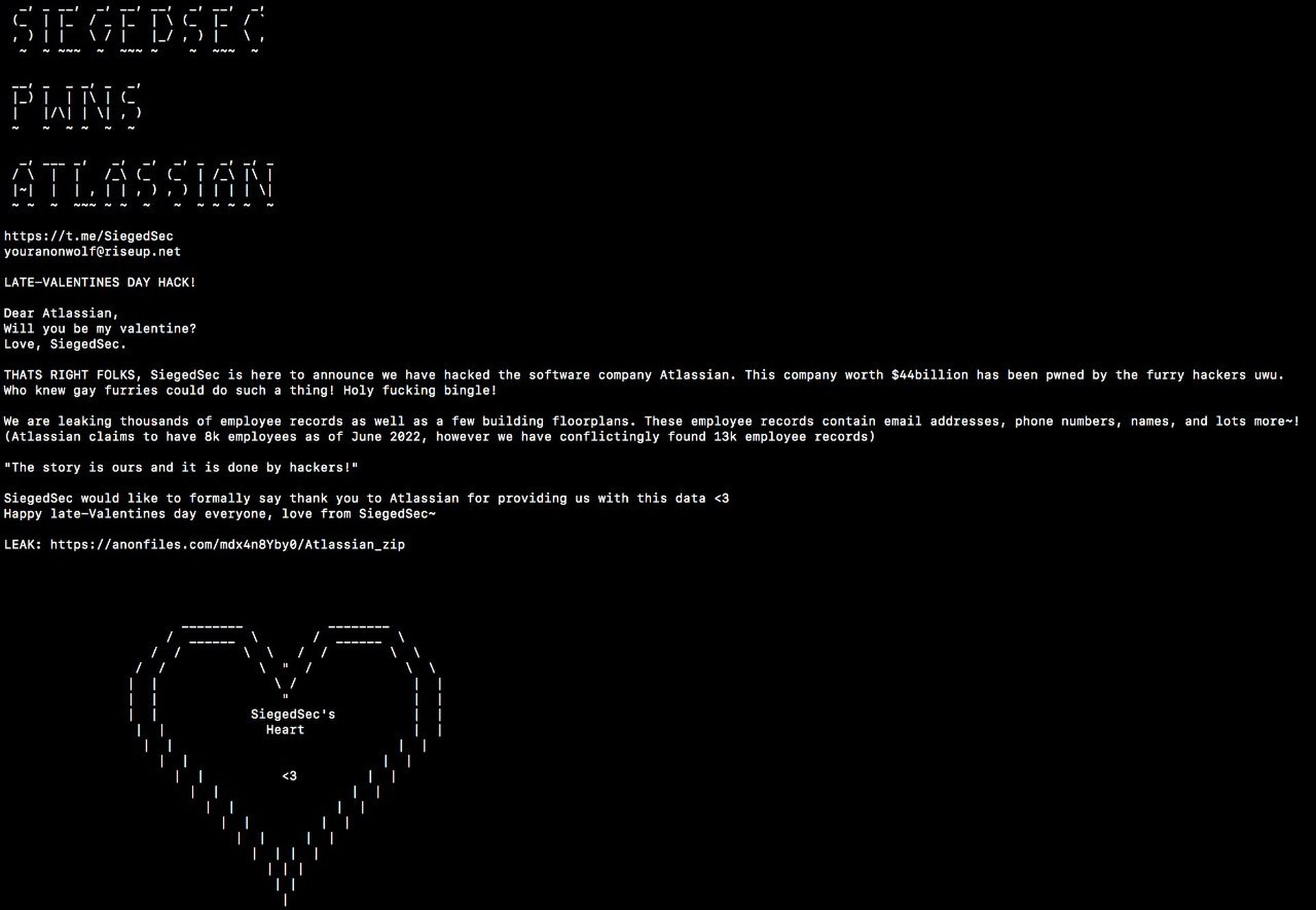
Earlier this week, a hacking group calling itself “SiegedSec” began posting on Telegram that they had compromised Atlassian's network and leaked employee data in a Valentine’s Day-themed note, claiming to have obtained email addresses, phone numbers, and names of employees as well as “a lot more!”
“SiegedSec is here to announce we have hacked the software company Atlassian,” the hackers wrote, according to a screenshot obtained by SC Media. “This company worth $44 billion has been pwned by the furry hackers uwu…We are leaking thousands of employee records as well as a few building floorplans. These employee records contain email addresses, phone numbers, names and lots more!”
However, independent researchers corroborated some of Atlassian’s claims, including their core contention that the data leaked online does not appear to have been taken directly from Atlassian systems.
Check Point researchers told SC Media the files and blueprints involved are consistent with the type of third-party data that Envoy would have stored and were stamped with Envoy’s logo. Lending further credence to the idea, despite claiming to have hacked directly into Atlassian’s systems, SiegedSec did not leak any other types of data.
The data leaked does not appear to be particularly valuable, and researchers at Check Point said it's not clear whether SiegedSec's motivations are financial, self-promotional or simply to cause chaos.



