Editor's Note: This set of reviews originally appeared in October 2020. To find out more about SC Labs, contact Adrian Sanabria at [email protected].
SC Labs took another look at deception networks tools this past October. There was no shortage of innovation or developments this year and these products have added powerful, impressive capabilities. Deception networks tools, in their most basic form, create decoy assets, environments, and full-blown OSes. These collectively create a deception fabric within an environment, which encourages adversaries to engage with the mimicked assets versus the real ones, preventing living-off-the-land attacks and data exfiltration.
All of these products have extensive machine learning functionality that adds a dynamic element to deception technology, changes with each environment and keeps pace with attackers. The realism of decoys lures in attackers and records every action that occurs during the engagement to offer security teams with a comprehensive understanding of the adversary and the techniques they used. Security teams can then use this attack intelligence information to close gaps and proactively strengthen defenses to prevent future intrusions and infections.
We were excited to hear that organizations are embracing these deception network tools. The conversation has moved from educating people on the basics of deception technology and reviewing tool capabilities to companies actively making additional feature requests and offering feedback on solutions. From that, it sounds like these powerful platforms are becoming staples in security stacks. If deception network tools are still not on your list, we confidently recommend that a company’s security posture will greatly benefit from deploying one.
Group Opener
SC Labs took another look in October 2020 into deception networks tools. These powerful solutions are continually becoming increasingly sophisticated. We were impressed with the growth and innovation the tools have undergone since last year and excited to see the new developments. Deception network tools are moving away from an emerging classification and steadily becoming more commonplace as the knowledge and awareness of these products continues to spread. These carefully constructed platforms add tremendous value to any organization that prioritizes the security of its environment and looks to bolster overall security posture.
Deception technologies are not a recent one and certain elements, such as honeypots, have been around for years. However, the nature of deceptions has undergone significant changes over time and continues to move further from its original aims as an information gathering and analytics tool, and closer to a proactive threat detection, hunting, and response platform. Security teams are looking for more from their deception products and demanding they do more than just offer intelligence; security teams want their deception tools to trigger automated responses based on the intelligence provided to help carry the burden of addressing security concerns and cutting through the ever-present alert noise.
The realism of these deception tools and the traps, decoys and breadcrumbs they employ continue to develop. The ability to create deceptions that are indistinguishable from real assets and environments has reached a near universal level. Machine learning continues to spread throughout the cybersecurity industry and deception tools are no exception. Many of the solutions we assessed this month have dynamic deception capabilities that utilize machine learning technology to reshape the network and create more decoys on the fly as adversaries engage with them, making reconnaissance and fingerprinting virtually impossible. Security teams still have the freedom and flexibility to create their own deceptions without compromising effectiveness, either from scratch, or using predefined templates, with many of these solutions. Attack surfaces are constantly growing, and the threat landscape continues to develop, becoming more advanced and sophisticated. Deception network tools are some of the most equipped solutions to keep pace with these changing techniques and the adversaries that employ them.
We are very excited to see where the continuous growth and innovation takes deception networks tools, especially now that they have become more frequently used and easier to manage. Security teams will likely be intrigued by the ability of the tools to automatically and dynamically create near-perfect deception environments and keep pace with merciless adversaries. Considering the newly-refined threat response abilities and automation functions, we think deception network tools may indeed have the capacity to become the catchall security tools the world of cybersecurity so desperately needs.
October Reviews:
Acalvio Technologies, Inc. ShadowPlex v5.2
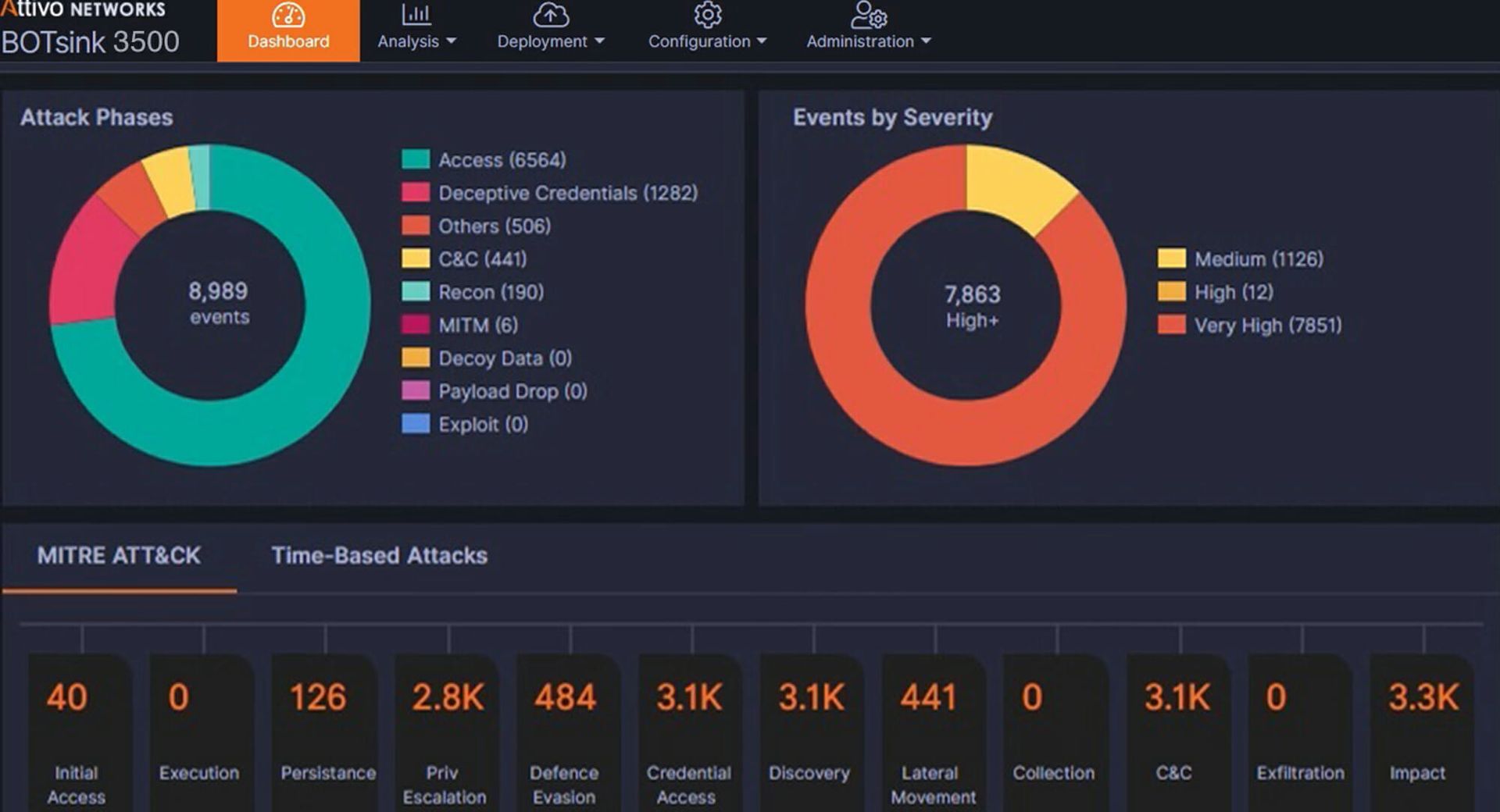
Attivo Networks ThreatDefend Platform v5.0
CounterCraft Cyber Deception Platform v2.6.0
Deceptive Bytes Active Endpoint Deception v2020.04.01
Illusive Networks Attack Detection System v3.1.126
PacketViper, LLC Deception360 v5.0
TrapX Security, Inc. DeceptionGrid v7.0