One of the largest healthcare providers in the country confirmed a data security incident Monday, saying at least 11 million patients across 20 states had their data stolen.
Tennessee-based HCA Healthcare, which runs 180 hospitals and 2,300 healthcare sites across the United States and was founded by the family of former Senate Republican Majority Leader Bill Frist, said the breach occurred through the compromise of an external storage location for an unnamed software system used to automate the formatting of emails.
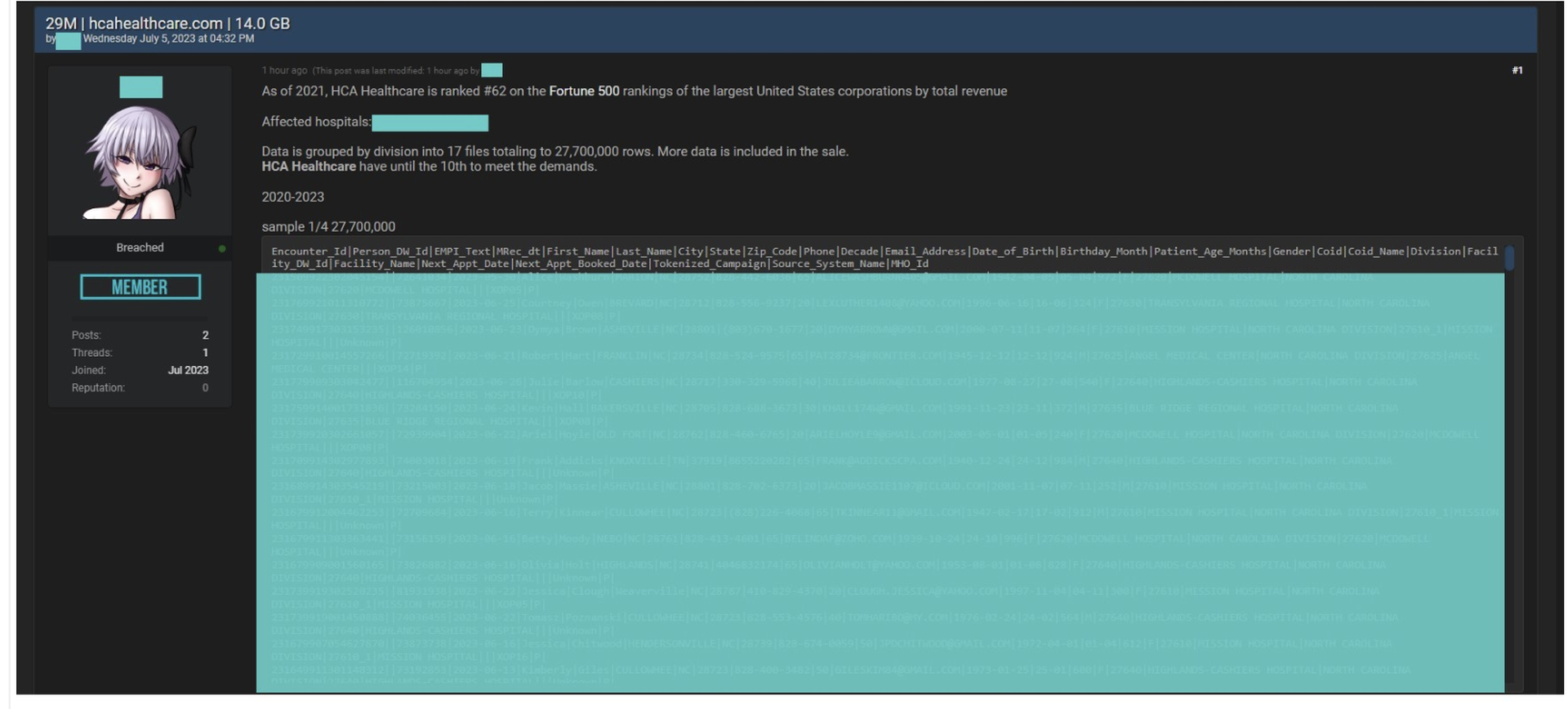
The provider said the breach was “recently discovered” and that the stolen data contains information “used for email messages, such as reminders that patients may wish to schedule an appointment and education on healthcare programs and services.” User access to the storage was disabled upon learning of the incident.
Thus far, the types of data confirmed as stolen include patient names, city, state, zip code, email, telephone number, date of birth, gender, patient service data, location and next appointment dates.
“The investigation is ongoing and we cannot confirm the number of individuals whose information was impacted,” the announcement states. “HCA Healthcare believes that the list contains approximately 27 million rows of data that may include information for approximately 11 million HCA Healthcare patients.”
The company gave a qualified statement expressing confidence that more sensitive forms of data were not taken, though cybersecurity experts routinely caution that the full impact of a breach is not always clear in the immediate wake of an incident.
“We do NOT believe that clinical information (such as treatment, diagnosis, or condition), payment information (such as credit card or account numbers), or other sensitive information (such as passwords, driver’s license or social security number) is involved,” the company wrote.
According to HCA, there have been no care or service disruptions related to the incident, nor has it impacted day-to-day operations, and the company said it does not believe it will impact business, operations or financial results.
Thus far, states with affected facilities includes Alaska, California, Colorado, Florida, Georgia, Idaho, Indiana, Kansas, Kentucky, Louisiana, Missouri, Mississippi, Nevada, New Hampshire, North Carolina, South Carolina, Tennessee, Texas, Utah and Virginia.
The confirmation was made five days after DataBreaches.net posted a screenshot of hackers advertising sale of the data on an underground online forum, which gave HCA Healthcare a deadline of July 10 to “meet the demands.” After being contacted, the seller told the site that they hacked the automated formatting system and contacted the provider on July 4.
The provider is offering credit monitoring to affected victims, and urged patients to reach out to a listed number if they receive a potentially fraudulent invoice that includes the stolen data. HCA Healthcare said it reported the incident to law enforcement and hired an outside threat intelligence provider and forensic investigator, claiming there is currently no evidence of malicious activity indicating a compromise of their networks and systems.
SC Media reached out to a media contact for HCA Healthcare and left a voicemail seeking further comment.
If confirmed, the 11 million figure would eclipse the largest healthcare data breach of 2022, which was the 4.11 million patients affected by a ransomware attack on printing and mailing vendor OneTouchPoint.




