When is a war really a not a war, at least as far as an insurance company is concerned?
That is the question the cybersecurity and insurance industries are likely to find out at the conclusion of a court case between Zurich International and the U.S. food company Mondelez International, one of the many firms victimized by NotPetya last year. No matter which company leaves the courthouse victorious this case may set a strong precedent for how other cyberinsurance policies are settled and act as a guide for what specific clauses and coverages are included in these contracts.
The issue at hand is Zurich is refusing to pay off on a property insurance policy, that Mondelez believes covers the company in this particular incident, but the insurer said is outside its coverage.

The answer will likely have a wide impact on the cyberinsurance industry, but in the meantime, companies should double check their policies to make sure the contract they have cover as many cyber-eventualities as possible, said Judy Selby, an insurance lawyer specializing in assisting firms purchasing cyber coverage.
“In this case the exclusion is in the form so there should not have been a surprise,” Selby said, but she believes Zurich faces an uphill battle as it must now prove the NotPetya attack was from or backed by a nation-state.
The case began in June 2017 when Mondelez was hit with the NotPetya wiper malware resulting almost $190 million in losses. In an SEC filing Mondelez broke this cost down saying NotPetya caused a 0.4 percent loss of net revenue, on the $25.9 billion in net revenue posted that year, along with $84 million in additional recovery costs.
Mondelez put in a claim with its insurance provider, Zurich America, based on a clause in its contract that stated it was covered for "all risks of physical loss or damage" to property, including "physical loss or damage to electronic data, programs, or software, including loss or damage caused by the malicious introduction of a machine code or instruction." Along with any loss or expenses incurred by the company for the period its business was interrupted.
Zurich eventually declined to make a payment citing an exception to coverage because NotPetya was a "hostile or warlike action" by a "government or sovereign power” so Mondelez countered with a $100 million lawsuit.
The U.S., U.K. and other governments have fingered Russia as the culprit behind the attack, but whether or not that will hold up in court is hard to say.
“This is now Zurich’s burden of proof. I’m not sure if they can get enough proof to satisfy the court,” she said.
There are steps that can be taken if a company does not want to end up in Mondelez’s position in the future.
The first step for any company, regardless of size is realizing that not only are they vulnerable to a cyberattack, but have probably already been victimized.

Tony Fenton,
Nationwide Insurance
Tony Fenton, vice president of underwriting and product for commercial auto, casualty, national programs and new product development at Nationwide Insurance, said a recent study by his firm found most companies don’t even understand what a cyberattack entails.
“According to Nationwide’s fourth annual Business Owners study, which surveyed 1,000 business owners with between 1-499 employees, only nine percent said their business had been a cyberattack victim when asked directly. Yet when given a list, 50 percent said their business experienced at least one type of harmful cyber activity,” he told SC Media.
This lack of knowledge may be one reason behind the fact that cyberinsurance is still not widely purchased. A survey conducted in December 2018 by the IT social network Spiceworks of 581 IT admins from organizations across North America and Europe found only 38 percent of organizations are currently covered by a cyberinsurance plan. The good news is this figure is quickly rising with 45 percent of those covered having obtained a plan in the last two years.
“We also talked to IT pros who belong to the 62 percent of organizations that don’t carry cyberinsurance to better understand why they’re going without it. The top reason businesses don’t carry cyberinsurance is because it’s not a priority at their organization (41 percent),” Spiceworks said.
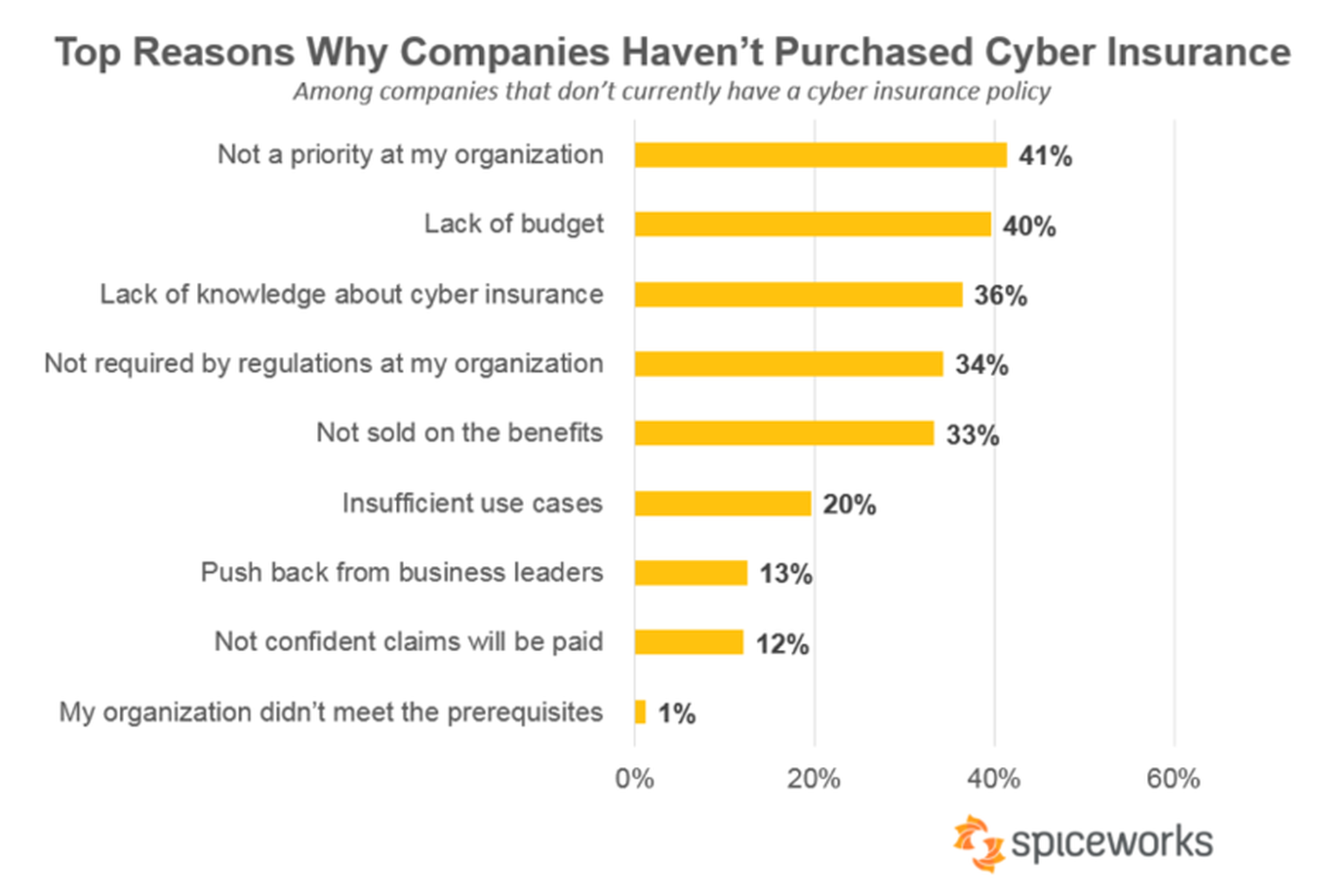
Sadly many more companies, despite cases the massive data breaches taking place, exposed databases being found and hordes of cybercriminals looking to steal every byte of data that is not nailed down, just don’t see the need.
A company in the market for cyberinsurance should first figure out what it needs to protect, Selby said, and then put together a package that best fits those needs.
Fenton agreed noting basic policies are offered on a customizable basis because every business has unique needs, but in general, there are some basic areas that should be covered in all such policies:
• Notifying customers about a data breach.
• Providing credit monitoring services as required by some states.
• Setting up a call center for affected individuals to obtain additional information and sign up for credit monitoring.
• Protecting your electronic data and computer systems from damage and computer attacks.
• Assisting with any associated legal expenses.
The next step is figuring out exactly how much coverage is needed. Just as with a home or auto policy not everyone needs the maximum amount of coverage, but at the same time, one does not want to get caught short.
“Given protection needs are unique to each business, we suggest that a customer review their risk and protection needs with their insurance agent. Since limits, coverage, and deductible options vary it is important to select the appropriate protection to match desired exposure mitigation,” Fenton said.
However, as Mondelez learned not every cyber policy is created equal.
“Customers should look for insurance coverage that goes beyond the cyberattack, such as adding business interruption coverage. These things need to be worked into the overall equation,” Selby said.
In addition, many non-cyber policies may have some level of cyber coverage so Selby recommends a company makes sure it is not paying extra for something for which it is already covered.
While most established insurance firms, and many lesser known names, offer cyberinsurance there is a danger for both parties if they do not do their due diligence in vetting their opposite number.
Even though cybersecurity, data breaches and massive attacks are all over the news, it is still a relatively new insurance area so not all brokers are up to speed on the topic so one must make sure the insurance company is properly knowledgeable on the topic before signing on the dotted line.
On the other side of the equation, insurance firms make certain the policies are being issued to companies that understand the role they play in keeping their companies safe.
Fenton said Nationwide makes several tools available, such as eRiskHub, that can give a business owner some insight into their level of exposure so they can be prepared for a cyberattack or data breach. This includes an incident response plan roadmap, which provides suggested steps to take following a cyberattack or data breach and online training modules on privacy best practices as well as risk management tools, including self-assessments and state breach notification laws.
Nationwide also has a list of recommendation for those it covers to help keep them safe. This includes employee education, conduct risk assessment, updating and patching software, evaluate employee exit strategies, remote project protocol, on and offsite data storage practices and then establish and enforce procedures and establish a comprehensive breach preparedness plan.
As the Molendex-Zurich case is proving even having some type of coverage is not protection enough. Phil Neray, VP of industrial cybersecurity for CyberX, said companies must take on the majority of the responsibility themselves.
“The primary insight for boards and management teams is that they cannot rely on regulatory compliance or cyberinsurance to protect their production facilities from the risk posed by modern cyber threat actors. To reduce the risk of destructive attacks like NotPetya that directly affect the bottom line, they need to provide their teams with sufficient resources and top-down attention to shore up their industrial cybersecurity, which has been neglected for far too long,” he said.



