In 2022, security practitioners struggled to address the growing attack surface created by their rapid push to remote work and cloud-based operations during the previous two years. Cyber criminals exploited new vulnerabilities – including those introduced by the growing use of third-party software – to launch ransomware and other attacks.
But with tools like zero trust, XDR and more automated threat intelligence tech to bolster vulnerability management, cloud, email and endpoint security, organizations fought back – and established plans to invest more to secure networks and data in the next two years.
Click here to download the full 2022 Cybersecurity Year in Review Report from SC Media.
The following is the final installment of a seven-part series about where security practitioners struggled and, in many cases, made headway throughout 2022. Here, we focus on their vulnerability management challenges.
Ongoing vulnerability management challenges
Vulnerability management remained a thorn in the side of security teams in 2022. As organizations continued moving to cloud-based operations and grew increasingly dependent on third-party partners, fresh software security holes materialized at a rate that was impossible to match, whether it be zero-day vulnerabilities in Microsoft Exchange or a dangerous cloud isolation vulnerability in Oracle Cloud Infrastructure (OCI).
But security teams were undeterred, investing in more aggressive, proactive vulnerability management strategies, according to a July 2022 survey of 213 security practitioners conducted by CyberRisk Alliance Business Intelligence. The survey showed organizations embracing continuous security assessments and automated remediation processes to stay ahead of newfound flaws and attacker exploits.
“We are more vulnerable due to more of our staff working remotely and accessing our information in different environments,” said one respondent. “This is the main reason why we have changed our vulnerability strategy.”
For security teams, the biggest obstacle to vulnerability management continued to be the sheer number of security holes to track. In one example from October, Microsoft updated the mitigation measures security teams should undertake for recently disclosed Exchange vulnerabilities that could lead to remote code execution after it was reported that previous measures were easily bypassed.
Then there was the revelation in October that a vulnerability in the Citrix Application Delivery Management (ADM) believed to have been patched in June was not sufficient to prevent exploitation.
Meanwhile, in September, IBM Security X-Force reported that amid a sixfold increase in new cloud vulnerabilities over the past six years, 26% of cloud compromises that X-Force responded to were caused by attackers exploiting unpatched vulnerabilities.
Claude Mandy, chief evangelist of data security for Symmetry Systems, said at the time that organizations must prioritize which vulnerabilities get patched first, not only find them.
“Prioritization of vulnerabilities should consider a number of factors including the severity, existence of public exploits, and accessibility of the vulnerability and the business criticality and sensitivity of the asset and data at risk,” Mandy said. “In the cloud, the complexity and scale quickly becomes unmanageable without use of vulnerability prioritization technology."
CRA survey respondents revealed many challenges in implementing and enhancing their vulnerability management programs: budget, endless patching, and proliferation of tools to name a few.

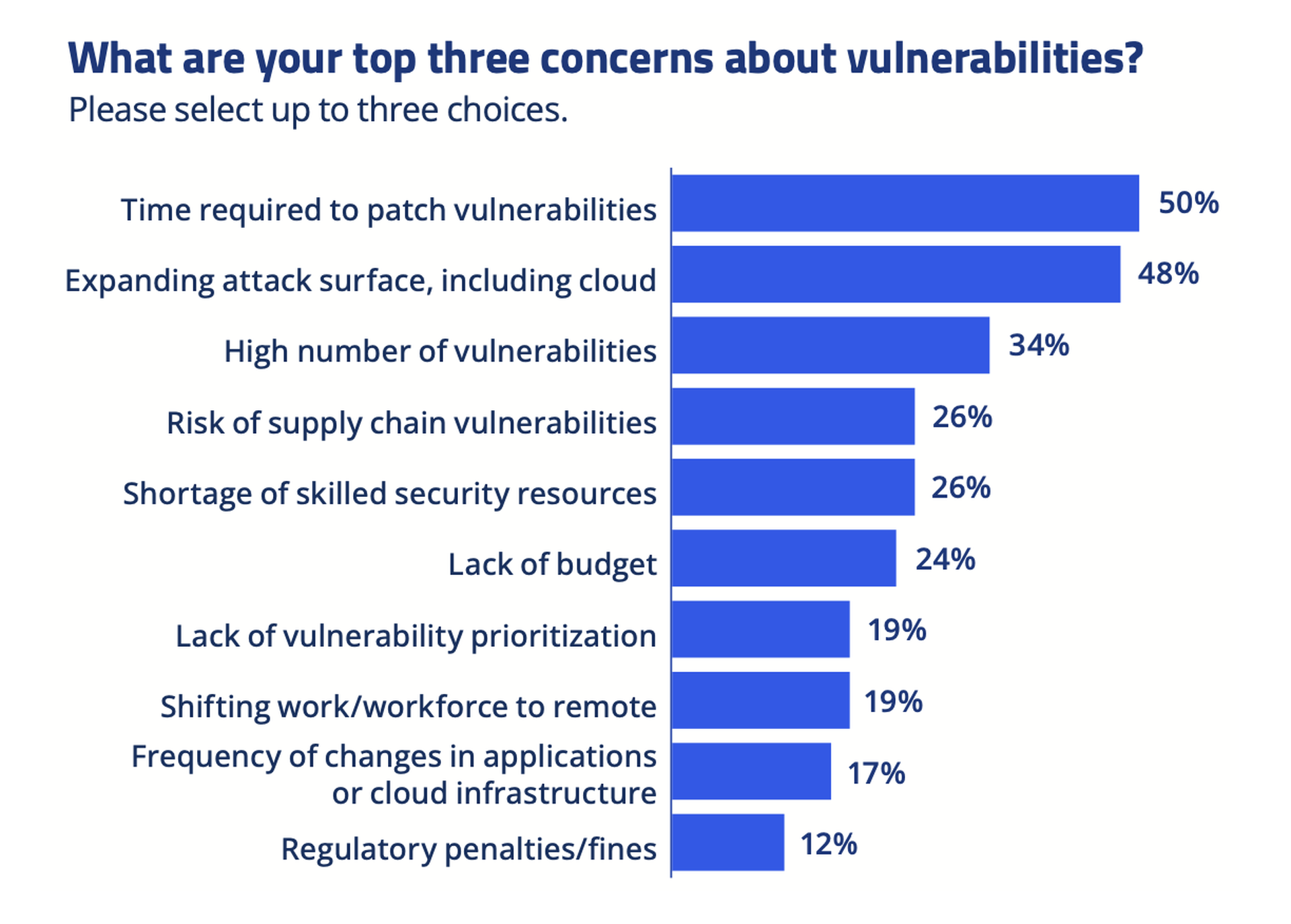
Efforts to turn the vulnerability tide
In the face of those hurdles, security practitioners doubled down on more aggressive vulnerability management strategies in 2022. Those who implemented more robust vulnerability management programs harnessed a combination of enhanced toolsets and automated solutions, increased scanning, expanded coverage of assets, improved patch management, and continuous vulnerability monitoring.
Additionally, some CRA survey respondents underscored their focus on vulnerability prioritization to address the more exploitable vulnerabilities of their higher-value assets. And in many instances, increased budgets, resources, and staff allocations were put in place to bolster security programs. More than two-thirds (69%) of respondents said their budget or spending on vulnerability management would increase in the next 12 months, especially for things like automation:
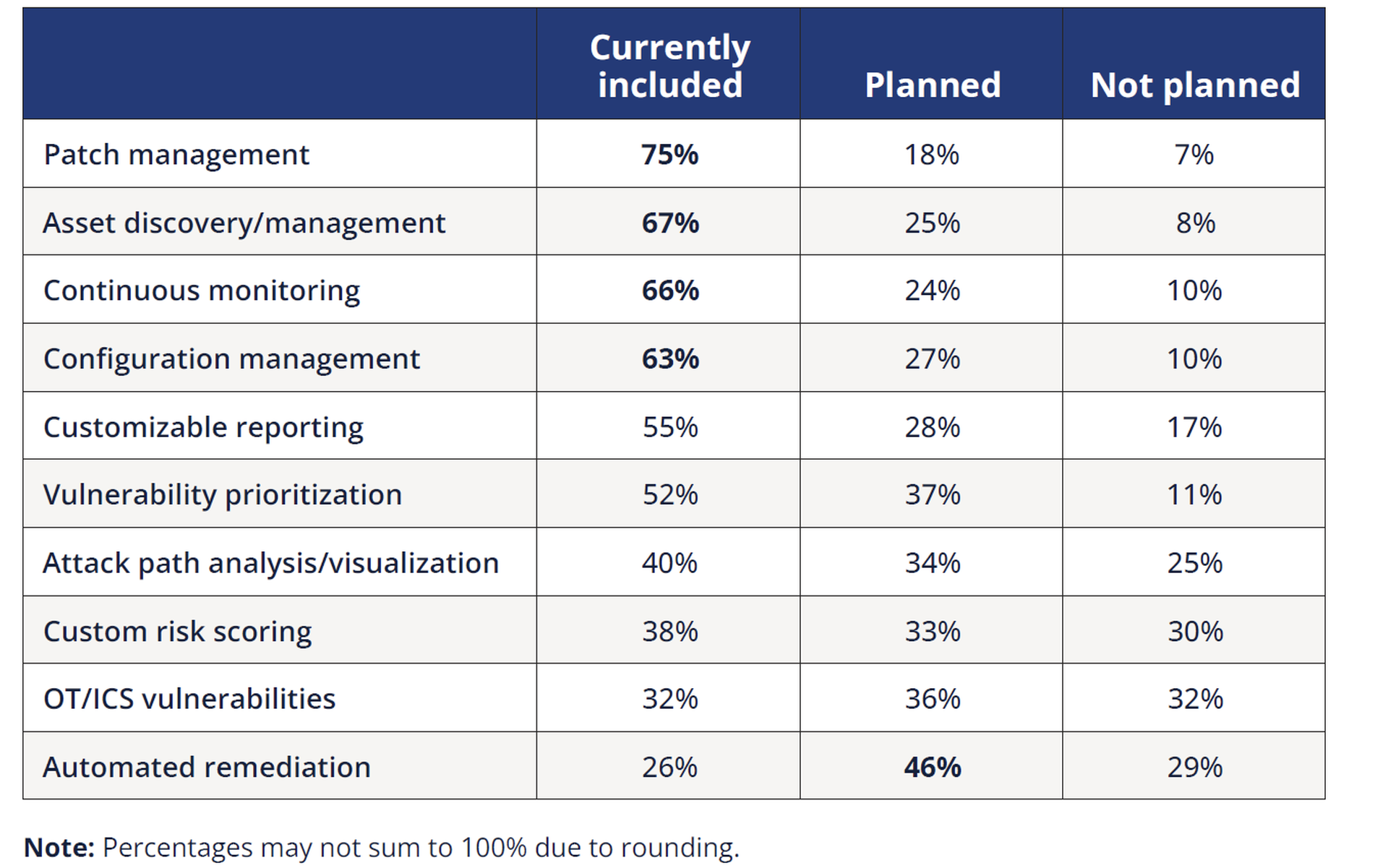
Respondents spoke out on their top vulnerability management challenges and changes they’ve made since 2020, which focused on intration of new tools and technologies nd adaptation of procedures to the evolving threat environment.

Said one respondent: “Since COVID, our budget increased considerably, and new strategies were implemented. The problem now is to keep the budget.”




