In a network that has no perimeter, knowing exactly who and what is on the network and why they are there is essential to maintaining organizational security. That's why a strong identity and access management (IAM) policy is fundamental to successfully deploying zero-trust architecture.
Indeed, zero trust means continually verifying authorized users as they move about the network and granting each user the lowest possible privileges when accessing sensitive areas, documents, or files. And while single sign-on and other authentication techniques can help automate aspects of both employee and customer identity and access management, even authorized users must verify themselves when moving from one segment of the network to another.
While the information security community has widely embraced zero trust as a philosophy, no comprehensive understanding exists for transitioning from zero trust as a concept to a reality. Nor are there universal standards for implementation. Yet, what remains undisputed is the critical role of IAM plays. Often it's step one in an effective zero trust roadmap.
But what is zero trust, really, and where does identity management fit?
To measure how well organizations are doing with zero trust implementation, CRA Business Intelligence conducted a survey of 300 IT and security decision makers in January and February 2022.
"Overall, the risk has decreased once we focused on assigning individuals the least amount of permissions possible to do their jobs," said one survey respondent whose organization had adopted the zero-trust model.
But many organizations are slow to move to a zero-trust model, despite the vast increase in the number of staffers working from home during the COVID-19 pandemic and the growing irrelevance of the perimeter-security model. Only about 35% of respondents to the survey said they were very familiar with zero-trust concepts, and about the same number said they had implemented it.
Company managers may not understand the importance of zero trust, and consequently may not allocate the resources to migrate to the new model. A quarter of the survey respondents who had not implemented the zero-trust model said management lack of support was a major constraint, and another quarter cited a lack of funding.
"Despite zero-trust mandates within the federal agencies, commercial organizations are less familiar with zero trust concepts," said Matt Alderman, executive vice president of CyberRisk Alliance. "These zero-trust research findings show that management support and budgets are the largest obstacles to implementing zero trust, which means adoption will be slow."
Moving to a zero-trust model
At the beginning of the pandemic, thousands of organizations suddenly faced the fact that most or all employees would be working remotely. No longer could these organizations rely on the perimeter security model, in which network access depends more on where you are — i.e., on-premises vs. off-premises — rather than who you are.
Instead, many of these organizations had to switch to an identity-driven security model, which lets a properly authenticated and verified user or device access the network from anywhere. But if you eliminate the perimeter entirely, then you need to tightly monitor and often sharply restrict what each user and device can do on the network — which leads to the zero-trust model.
Simply put, a zero-trust security model assumes a threat can just as easily come from inside the network as from outside it. The perimeter no longer matters. Instead of asking a user to authenticate themselves only at the perimeter, the zero-threat model also asks users to authenticate themselves when moving from one part of the network to another, or when accessing documents or files that require higher levels of security clearance. No user or device is ever fully trusted.
Paradoxically, the zero-trust model offers more flexibility to staffers. The model is based on who users and devices are rather than where they are. A user logging into the company network from home using their own PC is treated no differently from a user logging into the network from a company-provisioned machine on company property. Each device and user must state and prove identity, and that identity will determine the level of access granted.
Importance of identity and access management
That's where the identity and access management (IAM) policy comes in. You cannot have a functional zero-trust architecture without a robust IAM policy. The network administrator — or, more likely, the Active Directory domain controller — needs to know exactly who or what each device granted access to the network is, and exactly what levels of access that person or machine needs to do the job.
Why is that important? Because weak or underenforced IAMs aren't good enough. Verizon Data Breach Incident Reports indicate that most breaches involve stolen or brute-forced user credentials. A March 2022 report by XM Cyber, as cited by SC Magazine, found that "73% of the top attack techniques involve mismanaged or stolen credentials."
Once they're in the network, the intruders move laterally through it, penetrating new areas and new levels of access, evading SIEMs and other detection mechanisms by appearing to be legitimate users. This is exactly the kind of movement that strong IAM policies and zero-trust architectures are designed to prevent.
The attackers don't even have to be outsiders. In April 2022, Block (formerly Square) notified 8.2 million customers of its CashApp subsidiary that their personal information, including full names, account numbers and portfolio information, had been stolen by a former employee who still had access to CashApp's systems. A properly deployed IAM policy might have prevented this breach.
Identity and access management obstacles along the way
Yet implementing a proper IAM policy isn't easy. As the National Institute of Standards and Technology (NIST) noted in a 2020 white paper about zero-trust architecture, network administrators must first identify all the "identities," both human and machine, that need access to the network as part of their jobs.
Every single user, which in the computing sense can be a person, a program or a machine, needs to be named and catalogued with that user's specific access privileges, from the newest intern to the long-standing CEO. As NIST states in its white paper, "often, these accounts are granted too high a level of trust, let alone zero trust."
This can lead to awkward decisions that IT managers may not be empowered to make, because NIST also states that "access levels should be trimmed back to the least privileged necessary for them to perform their tasks."
In other words, an IT staffer may have to tell a C-suite exec that he can no longer access huge areas of the company network — and convince him that doing so is for the greater good of the organization. Greater access can always be granted if necessary.
"There are still occasions where a user isn't granted enough permissions," stated one respondent to the CyberRisk Alliance survey whose organization had fully moved to the zero-trust model. "But it's usually better to grant fewer than required instead of too many because permissions can be changed as needed unless resources have already been breached."
And indeed, the survey found that among the components of zero-trust architecture, implementing such least-privilege principles in IAM was rated of low importance by the average respondent. Implementing multi-factor authentication, a concept that might be easier to explain and justify to management, was granted the highest importance.
"Management support and budget limitations are hindering zero trust adoption, at least in the near term, " said CyberRisk Alliance's report on the zero-trust survey. "Deployment has been slowed by an ongoing struggle to fully comprehend the elements that embody zero trust and how to put all the pieces together. "
How to be a zero-trust champion
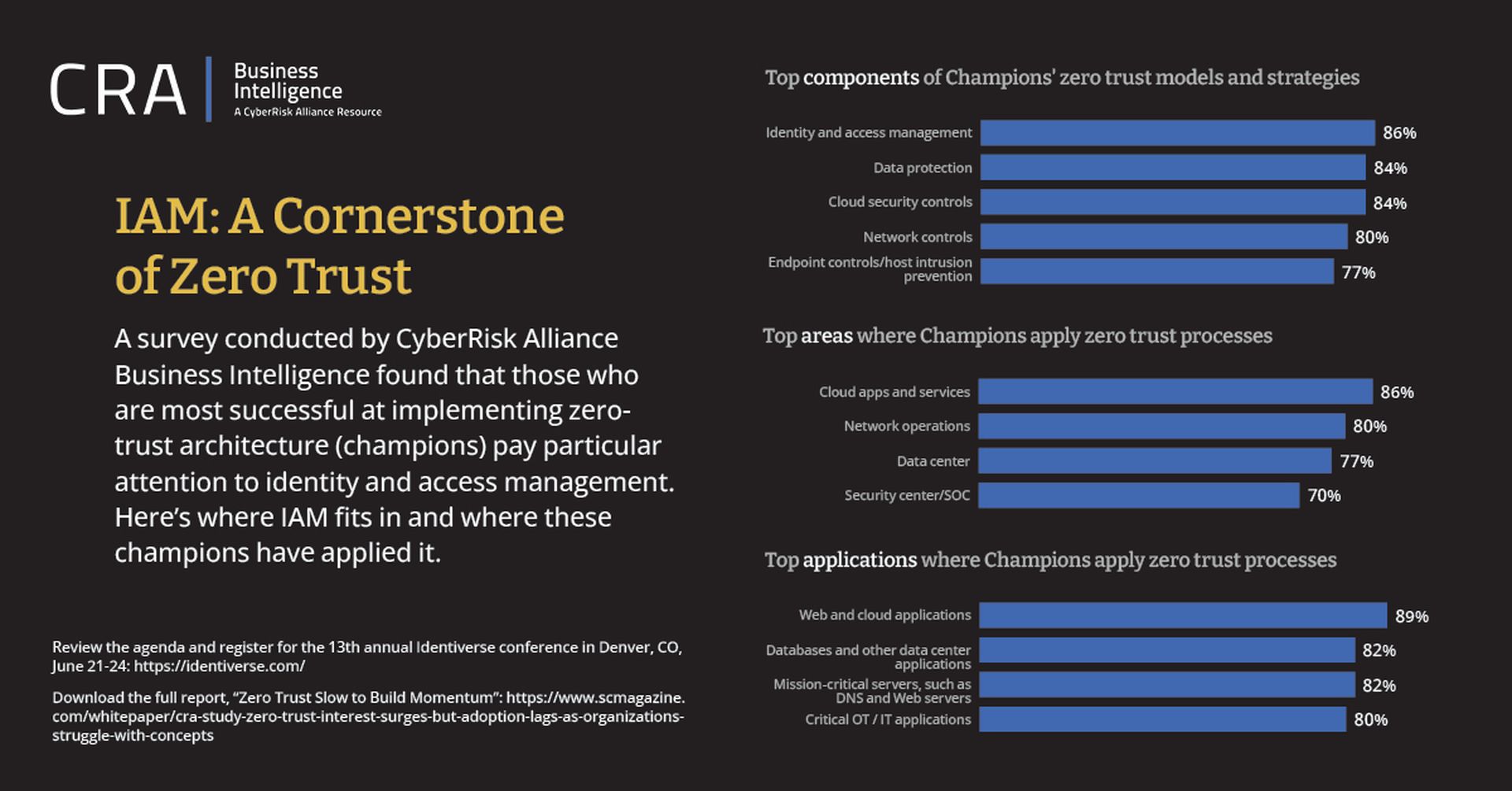
Yet among the survey respondents, the CyberRisk Alliance survey identified 70 "champion" organizations that had successfully implemented the zero-trust model.
These organizations tended to be a bit larger than the average survey respondents, and to be concentrated in manufacturing, health care and technology. Many had regulatory obligations or concerns about complex supply chains that may have spurred the move to zero trust, but 66% also said they wanted to reduce the risks posed by remote workers.
Significantly, these champion organizations not only had the technical know-how to implement a zero-trust architecture, but also upper management support for and understanding of zero trust, with the resulting budget allocations. Most planned to increase zero-trust investments for 2022.
"There has been a slight learning curve and hurdles to implementing zero trust, but the benefits are worth it," said one respondent from a champion organization.
Among these champions, identity and access management was the most frequently implemented component of zero-trust architecture, with 86% reporting its use.
"Any attempt to access the network must be verified," said another champion respondent. "Never trust anything."




