Healthcare organizations rapidly driving technology and digital innovation to enhance patient care and safety will not effectively establish the latter without ensuring that their security program and tools are maturing at the same speed.
“Digital maturity by itself does not equal security maturity,” said Saif Abed, M.D., founding partner and director of cybersecurity advisory services for the AbedGraham Group, during his Tuesday presentation at InfoSec World.
“If [digital maturity] does not equal security maturity, it cannot equal, by itself, the enhancement of patient safety,” he continued.
Grasping this key concept is crucial for making business decisions and for security leaders attempting to engage executive management in understanding where to invest in the security ecosystem. It’s also critical when considering the adoption of any new tools, including those to support the interoperability directive from the Department of Health and Human Services.
The new reality for healthcare is that patient care has fundamentally changed, and with it, the digital ecosystem has evolved. Patients are no longer accepting of only receiving care within the four walls of a hospital and want more flexible options that are clinically effective.
Technology is critical to this care evolution, from field centers to care for patients during the COVID-19 outbreak, or managing chronic care patients within their homes. The pandemic has further fueled this shift, while “accelerating our dependency on digital solutions and infrastructure like never before.”
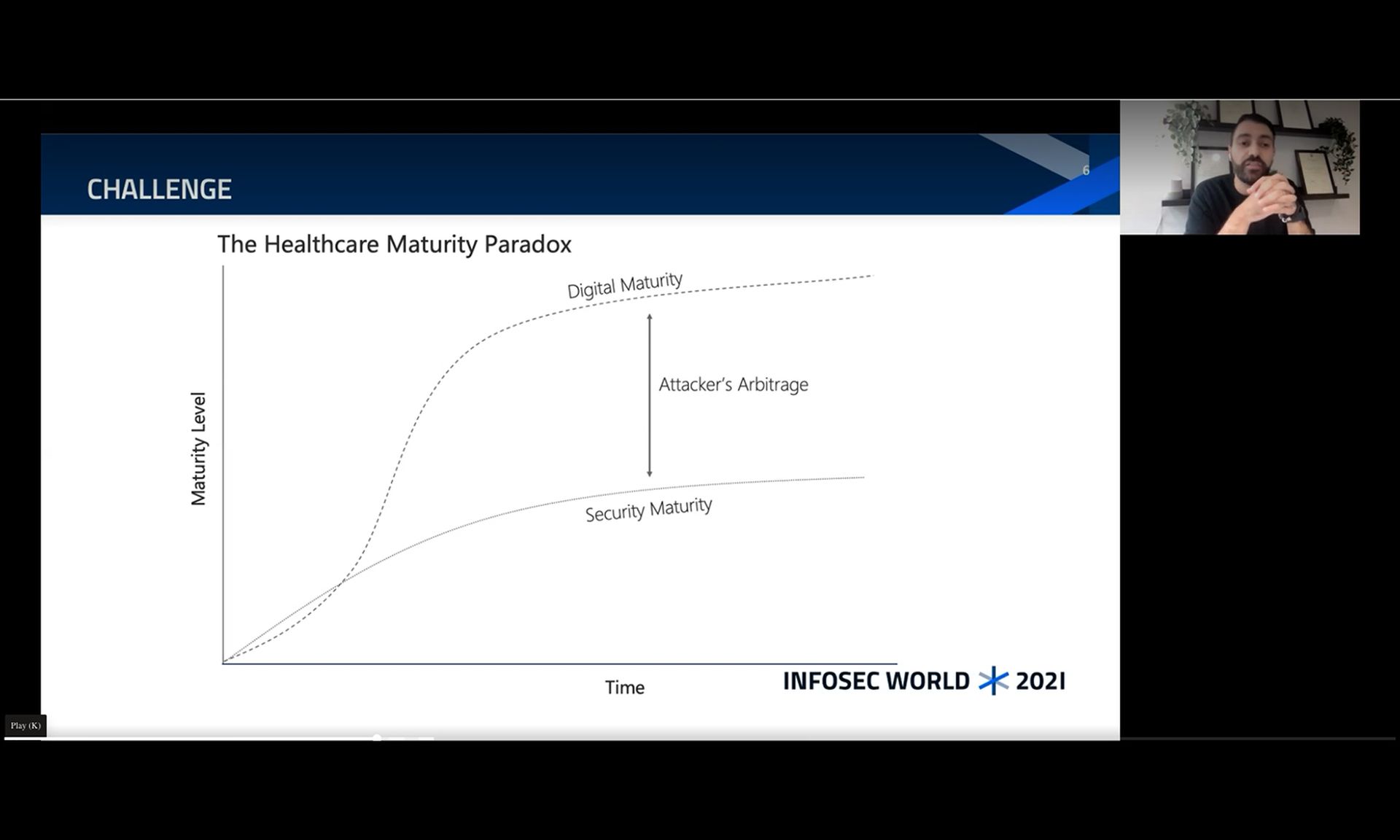
And as the infrastructure becomes more interconnected, it’s increasingly clear that business decision makers, particularly in healthcare, must ensure they’re equally maturing security to ensure the safety of the hospital environment. Abed explained that more than ever, there are serious challenges to security resilience in the sector and from a patient safety perspective.
Digital maturity refers to how much of the organization relies on paper or technology for daily processes, such as writing prescriptions, lab testing, or other care processes. The more heavily an organization relies on digital processes, the more they’re considered mature.
“What digital technology has done is add a level of scalability to risk that we didn't have to deal with before, or certainly not at this level of scale,” said Abed. “The development of digital hospitals, digital clinics, digital care facilities has gone up at an exceptional pace.”
“The digitization of healthcare has moved at a pace whereby the security element, the safety element, has not received the same level of consideration that one would expect,” he added. “In fact, there has been almost a lackadaisical view early on that.”
For example, there’s a common misconception that if legacy technology or paper processes are replaced, then the “modern system will be safer and more secure as a consequence” by default, he explained. But that’s simply not the case when security is not developed in tandem, nor when the risks posed by humans are not considered during the implementation.
Any gaps between digital maturity and security maturity are what threat actors target and subsequently exploit. He explained that if an attacker sees an entity with a high digital dependency but with a low security posture (in terms of resiliency and response), all they need is the right incentive to spark the attack, most likely financial.
What’s at stake? Patient, safety and care quality
Several reports and lawsuits have truly driven home the impact of cyberattacks on patient safety. But for Abed, the true concern for healthcare provider organizations should be the impact on care morbidity: how care services will be delayed and the potential patient impact during a cyber event.
Some of the weakest systems are the most critical in healthcare, such as the Picture Archiving and Communication System used for medical imaging. A single point of failure on the device can disrupt care for multiple patients, as providers won’t be able to order pathology or blood tests, or perform analyses.
“Then you've essentially shut down so much of the ability to deliver healthcare because almost every clinical decision these days in an acute setting is based on pathology test results, and medical imaging,” said Abed. “They are highly beneficial from a workload perspective. But when they fail, they're compromised.”
“A cyberattack can essentially ground almost all clinical workflows to a halt. And as you can imagine, as a security leader, that is a valid use case that you need to be able to explain to non-technical executive management,” he added.
Business leaders can clearly see the impact to services and the need to protect these devices to maintain essential services. Organizations must consider the realities of how delayed clinical decisions, surgeries, appointments, prescriptions, and test results will impact an eventual patient care outcome, he explained.
There is tangible evidence of how these delays can cause reductions in clinical workflows and care quality, as well as a tangible impact on patient safety.
“I always used the example, if someone was suspected of having a stroke, and they were in an ambulance, they have a three to four hour window of opportunity to treat the clock in the brain,” Abed explained. “Any minute of delay, 20 to 30 minutes, could have a significant impact, or be the difference between that person being half-paralyzed or making a full recovery.”
There are also similarities with delays in care in suspected cancer patients. Abed added that there’s a “real tangible impact but not being reported in the media.”
Further, the attack methods have increased in scalability to truly concerning levels of impact, driving the need for an increasingly measurable and fundamental change in the way business leaders of healthcare organizations or technology companies support healthcare.
Does it mean healthcare should stop its digital transformation journey? Of course not, but Abed stressed there’s an overall need for a “parallel track of thought and investment in strategy that looks at the risk side of digital maturity, and that manifests itself in terms of cybersecurity.”
“What we need to understand is the impact and the outcomes. If we’re saying that the attackers have changed, do they understand the levers that would work in their favor?” Abed noted. The pandemic has exacerbated attackers’ understanding of “clinical urgency,” targeting entities that have sensitive patient care on their hands and IT systems used for clinical services.
“An attacker understands that if they can increase clinical urgency and dial it up to its maximum potential in the early moments and hours of an attack, then [the victim] is more likely to pay the ransom. And that is, after all, what the vast majority are looking for,” he continued.




