Unmasking the identities of cybercriminals hiding behind VPN and proxy services is cat and mouse game as old as default passwords.
Now, a team of university researchers from Denmark and India claim to have developed a novel technique capable of unmasking cybercriminals hiding behind VPNs, proxy servers and Tor browsers with up to 70% reliability.

"Our research demonstrated significant effectiveness in detecting concealed IPs, achieving success rates of approximately 65–70% for Tor users, 40–45% for VPN users, and 60–65% for those behind proxy servers,” the authors wrote in technical paper Unmasking the True Identity: Unveiling the Secrets of Virtual Private Networks and Proxies (PDF).
The technique leverages honey pots and Canarytokens used to bait attackers to interact with token-embedded files (Excel, Word, PDF, ZIP) and URLs (QR codes, DNS tokens, HTTP requests). If an attacker falls for the trap the method generates an HTTP request containing metadata such as IP addresses, user-agent strings, timestamps and geographic data.
“When the attacker tries to access or load the honey file, this will cause the payload to start looking for information such as the real IP address and user agent (data tied to the hacker’s browser, operating system, and device),” the authors wrote.
This, in turn, triggers a process in which the incriminating attacker’s data is sent back to a cyber-defender’s server.
A better mouse trap, honey pot
Compared to existing VPN or proxy unmasking methods, such as traffic analysis — which has an average success rate of 42% for connections between Tor clients and entry nodes — the Canarytoken and honeypot approach is far more successful, researchers say. Other unmasking techniques such as protocol fingerprinting, have an accuracy over 85%. However, that success rate is typically limited when used with specific VPN protocols such as OpenVPN.
“When people purposefully use advanced techniques, such as encryption, proxy servers, and VPNs, to hide their online activity, traditional methods, such as log analysis and packet inspection, find it difficult to identify IP addresses,” they wrote.
Why you should care?
Identifying IP addresses is central to thwarting attacks and helping law enforcement put the bad guys out of business and in jail. For example, in the 911 S5 botnet case, criminals used VPN apps (MaskVPN and DewVPN) to hide and execute over $1 billion in pandemic and unemployment fraud. In that case, it took the feds eight years to track down the alleged 911 S5 mastermind, YunHe Wang, and shut down the botnet.
Unmasking an attacker's IP address allows defenders to take swift, decisive and targeted actions to mitigate threats. It allows defenders to use IPs to immediately block malicious traffic via firewalls and update anti-intrusion systems and web applications with blacklisted addresses.
Malicious VPN and proxy misuse is trending the wrong way. SpyCloud's 2025 Identity Exposure Report, found that 91% of organizations experienced identity-related cyber incidents in 2024—nearly doubling from the previous year. Many of these attacks use VPN or proxies for cloaking and for MFA bypass techniques such as machine-in-the-middle.
Outfoxing the fox
The "Unmasking the True Identity" technique developed by the team of researchers is a new spin on existing honey pots and Canarytokens.
Canarytokens are simple tripwires hidden in digital assets that, when triggered, send an alert with basic metadata. Honeypots are decoy computer systems that mimic legitimate networks or resources. They are designed to attract attackers so defenders can learn adversarial tactics, techniques and procedures to build better defenses.
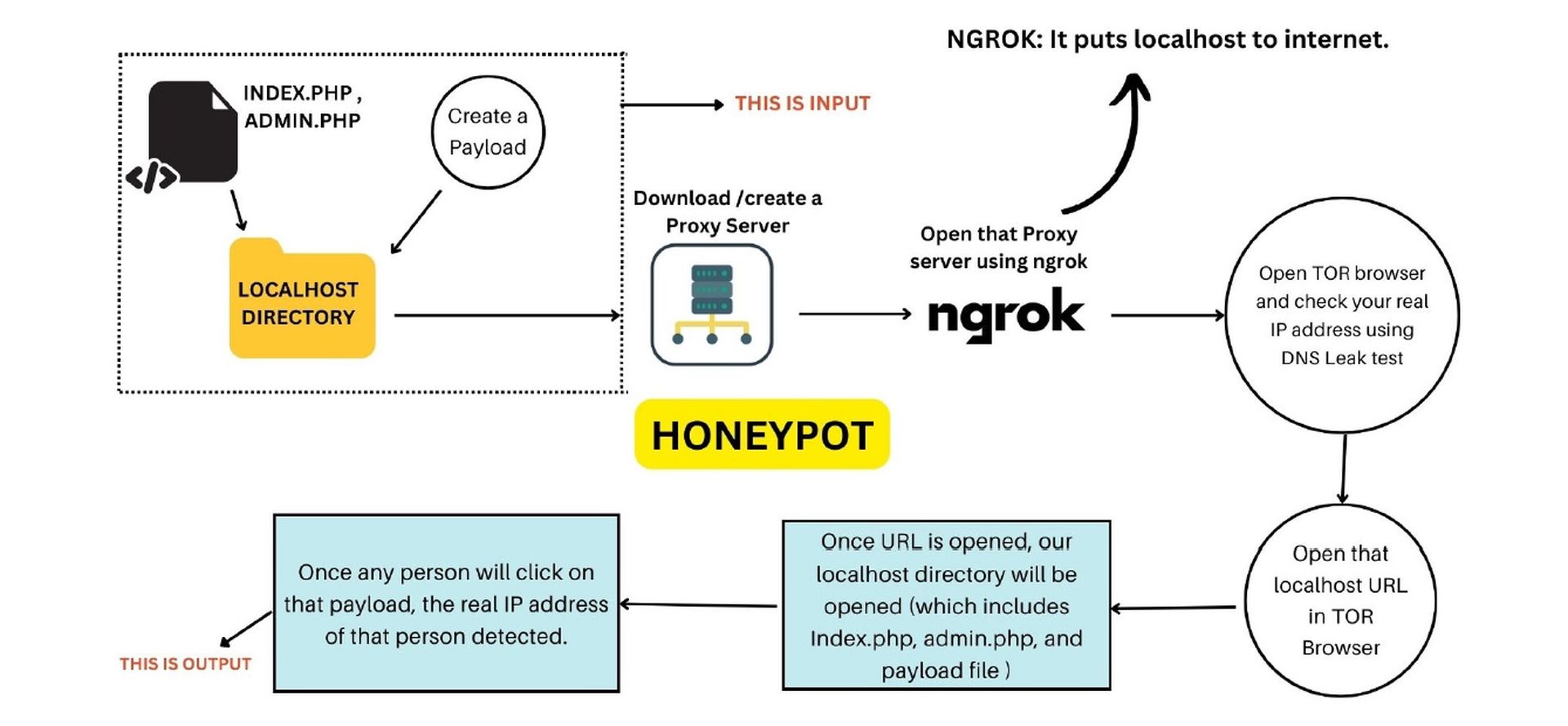
Researchers go beyond the conventional use of honey pots and Canarytokens. For starters, researchers run their honey pots in a localhost environment and use a reverse proxy server (LocalXpose and ngrok) to make them visible to the outside world.
“[The system] acts as a middleman between the user on the internet and the local server, all communications with the login form will be recorded and kept by the proxy server,” authors wrote.
By hosting the honey pot on a localhost rather than a web host, researchers said real-time traffic analysis can weed out false positives and the automation of payload creation for Canarytokens is optimized.
Systems must have robust “computational power required for running the localhost and proxy server, managing payloads, and handling data analysis,” researchers note. “Captured data is processed through a centralized logging system and analyzed using machine learning classifiers, ensuring structured and measurable evaluation.”
Masked and anonymous
Analysis factors included attack obfuscation techniques such as predictability of dynamic IP address changes and masking tools ranging from Tor network, VPN services and proxy servers.
While successful unmasking rates are impressive compared to alternative techniques, researchers were most often challenged by attackers using dynamic IP assignments and those using mobile networks.
“The usage of mobile devices and dynamic IP allocations adds another layer of difficulty, as people connecting to the internet from different places makes it difficult to keep stable connections between users and particular IP addresses,” they wrote. “We determined that the success rate of the dynamic IP was around thirty percent.”
Researchers said their unmasking method will become more effective over time as new machine learning models for attack pattern recognition and new evasion strategies are integrated into AI training classifiers.
“Our research demonstrated significant effectiveness in detecting concealed IPs... contributions strengthen ongoing efforts to improve online security by offering practical insights into detecting and mitigating the risks associated with the misuse of VPNs and proxies.”