Vendor: Fidelis Cybersecurity
Price: $50,000 for 10 VLANs
Contact: www.fidelissecurity.com
Quick Read
What it does: Fidelis Deception delivers complete visibility across all environment architectures and automated threat and data theft detection, threat hunting, and optimized incident and response capabilities.
What we liked: Fidelis built a powerful, agentless tool that offers a deep understanding of all activity occurring within an environment and the automation necessary to respond to this activity effortlessly. We like the high-level view of deception coverage offering during deployment that lets organizations confidently use deception protection.
Security pros will find Fidelis Deception a fully integrated deception product that delivers complete visibility across all environment architectures. It offers automated threat and data theft detection, threat hunting, and optimized incident and response capabilities to combat almost any kind of cybercrime. The unique combination of adaptive intelligent deception, terrain analysis, and security visibility drives efficient threat response and comprehensive protection.
Fidelis offers more than 1,000 OS and emulated decoys, each containing support for more than 200 VLANs per server and covering everything from Active Directory deception to MAC spoofing. Analysts may configure these decoys themselves or let the platform create them automatically. To ensure the quality of automated emulations, Fidelis conducts thorough profiling and classification of an environment, gathering full visibility into all activities. Fidelis may then autogenerate decoys based on this information and craft them so that they mimic real components. The system will continue to adapt the decoys as the network changes to ensure maximum realism.
Manually-created decoys also have full flexibility so security teams may configure them however they prefer. Analysts may upload real files for realistic decoy construction and even control the ways in which adversaries access decoy services. While there’s a steep learning curve with manual deception creation, the process establishes a stronger deception posture in exchange for the added effort. Sophisticated security teams will likely find the work worth the reward.
All interactions with decoys, whether created manually or automatically, are recorded and grouped according to correlations and several forensic elements and conclusions. Since Fidelis runs as an emulation-based tool, it provides all logged activity from the view of an attacker and paints a picture of all adversary activities during engagements, including credential collection activities and file uploads. All files uploaded to decoys are automatically sent to the sandboxing engine for analysis. Security teams may either permit automated responses to address these attacks or choose custom workflows to create attack responses manually. Both automatic and manual responses include attack validation, correlation, and expulsion, so analysts may elect the response type they prefer without sacrificing security.
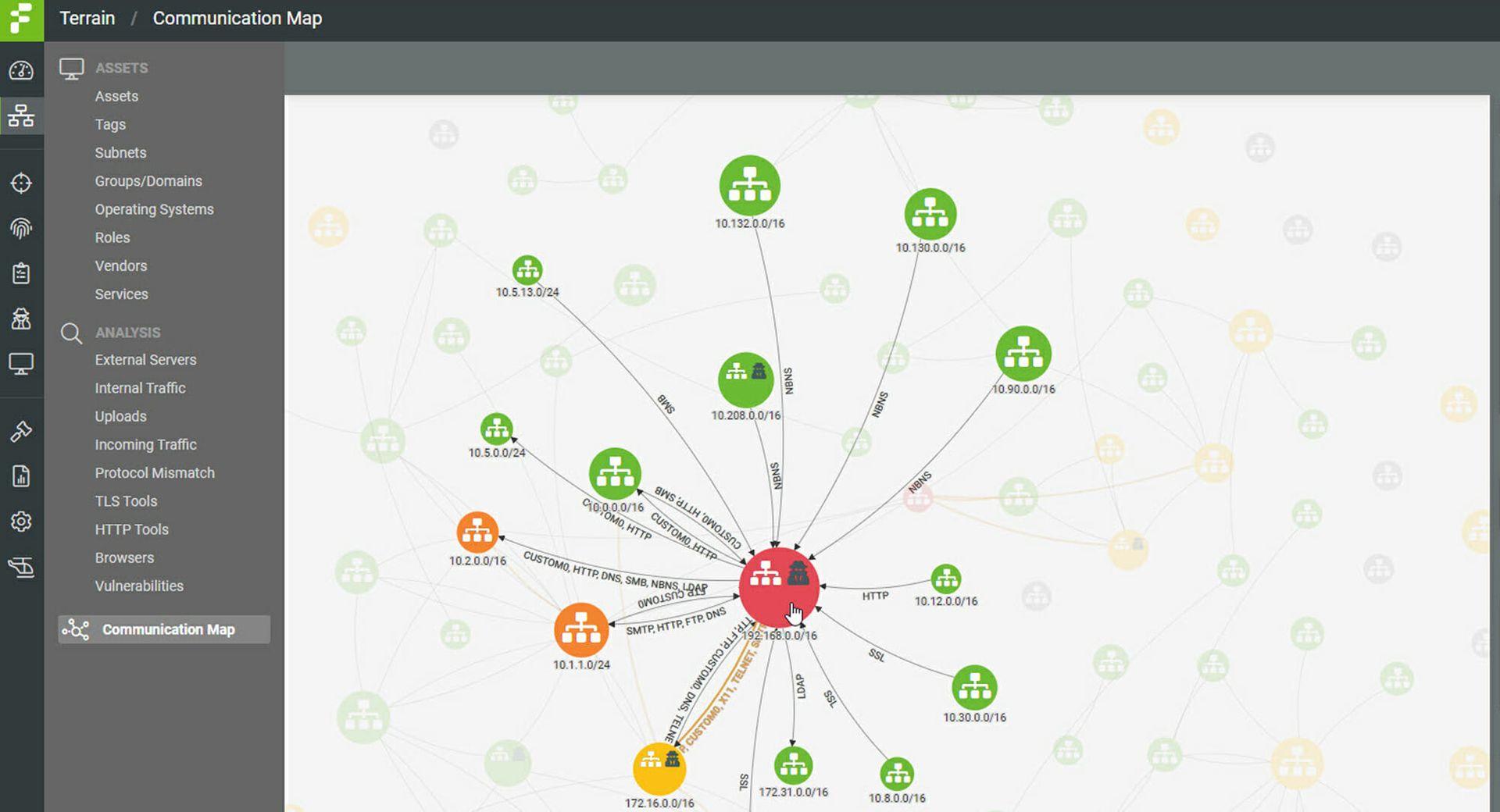
A map shows a high-level view of all the communications within a network and the locations of the breadcrumbs and decoys deployed within an environment. Analysts may drill into each asset or subnet to see various asset risks and risk scores. Security teams may run red team simulations directly from this view to anticipate how attacks may progress. The platform maps all events onto the relevant MITRE ATT&CK framework tactic so that analysts may quickly filter through them and locate those that require their immediate attention.
Overall, security pros will find Fidelis Deception a powerful, agentless tool that offers a deep understanding of all activity occurring within an environment and the automation necessary to respond to this activity effortlessly. Fidelis Deception gives a high-level view during deployment so that organizations can use deception protection with confidence. Several reporting options reveal different views and levels of granularity, making them digestible for all team members and not just security experts. Because of its many enterprise-related capabilities, security teams will find this adaptable product a solid investment.
Pricing for the VLAN model starts at $50,000 for 10 VLANs and increases $1,000 for each VLAN thereafter. Tiered pricing starts at $19 per user. Technical Account Managers are available to help operationalize the solution and ensure customer success.



