SC Labs revisited endpoint security tools this month, an area that’s become increasingly more relevant as the bad guys run phishing attacks via email. These cloud-based management systems have taken endpoint security to the next level with proactive attack prevention, accurate detection and effective remediation.
The comprehensive visibility these tools offer uncover visibility gaps at an enterprise level. Security pros need visibility to maintain good IT hygiene and hardening security posture. These products also help security teams and administrators ensure other security investments are configured to maximize efficiency, rightfully demanding more from existing tools.
We continue to see a convergence of endpoint protection with endpoint detection and response functionality. This makes sense because the full attack chain now gets covered from prevention to detection and response all the way through to rollback and patch remediations. The plain English explanations guide junior analysts in the right direction and offer seasoned analysts with rich, at-a-glance information to quickly understand what occurred during an event. Deploying one of these tools will shore up an organization’s security posture, maximize the effectiveness of its security team and ensure it’s getting the most from existing security investments.
Product Group Opener
SC Labs revisited endpoint security and we’re pleasantly surprised with the transformation and development familiar players in this market have undergone since last year. We noted that the industry has moved on from on-premises tools, and that's why we only assessed cloud-based management systems. With this welcome change comes a dramatic improvement in seamless third-party integrations and comprehensive, enterprise threat detection and device control. The move to the cloud drives accurate detection and a comprehensive picture of an attack through detailed process chains that offer analysts intelligent prioritizations and remediation suggestions. The centralized management consoles streamline the day-to-day operations for administrators and alleviate some of the tiresome workloads.
As the digital state expands exponentially today so do the threats organizations face. Advanced persistent threats are the new normal and continue to grow more sophisticated and complex. Security pros continue to demand more coverage and protection from security tools while they struggle to effectively assess and maintain good cyber hygiene.
Although the prevention and detection capabilities of these tools continue to grow more effective, the response component of EDR often bogs down security teams. What happens when a malicious file gets through the prevention layer? Great that we detected it within the environment, but now what? This starts a high stakes race against the clock. The tools we assessed this month unilaterally leverage machine learning engines to automatically assess where a breach occurred and exactly what happened after that. The attack process information gets pulled into an enriched, often plain English rundown, outlining which systems were impacted and the extent of the damage. This explicitly clear, big picture view of a malicious event lets an analyst cut through any guesswork and quickly determine next steps to act, reducing the notoriously lengthy dwell time between detection and response. Rollback features that cleanse files and revert all changes a malicious process enacted on a system and one-click isolations hack the response delay even further. This empowers analysts to keep pace with threats and effectively batten down the hatches of their organization.
Security teams struggle to keep up with workload demands that result from the persistent and devastating threats the bad guys throw at digital perimeters every day. The ever-increasing number of security tools available on the market, although well-intentioned, are adding to the difficulty of maintaining a good security posture. Administrators and executives are at odds struggling to decide which tools to invest in, while security teams buckle under the weight of monitoring for threats while continuously fine-tuning configurations to get the most out of security investments. Features like the attack trees and threat information enriched with valuable event context take the guesswork out of the detection and prevention processes and further expedite response time with machine learning-backed auto remediations. The endpoint security tools we assessed this month help junior and senior-level analysts alike to quickly understand what occurred as the result of a malicious event and efficiently hunt at an enterprise level for related incidents.
Pick of the Litter
Cybereason Defense Platform operates as a solid, low footprint endpoint security option that issues alerts immediately without interrupting normal internal system processes. The cross-machine correlation delivers thorough, enterprise visibility and event correlation, presenting analysts with actionable information and one-click remediation options. The robust endpoint security features and the regularly-updated support materials to ensure customer success make this product an SC Labs Best Buy.
CrowdStrike Falcon combines comprehensive threat intelligence from the Falcon OverWatch team with next generation antivirus capabilities, endpoint detection and response, and managed hunting, going beyond alert triage into the realm of proactive threat hunting. Overall, we consider CrowdStrike Falcon a superb solution that does a great job identifying suspicious behavior and delivering robust contextual event information, making this our SC Labs Recommended product for this month.
July Reviews
Cybereason Defense Platform 20.1
F-Secure Protection Service for Business, Computer Protection Premium 20.1
FireEye Endpoint Security v.4.9
McAfee MVISION Protect Plus EDR 10.7, 3.0
Microsoft Defender Advanced Threat Protection
SentinelOne EPP Jamaica#38/Agent 4.0
Sophos Intercept X Advanced with EDR
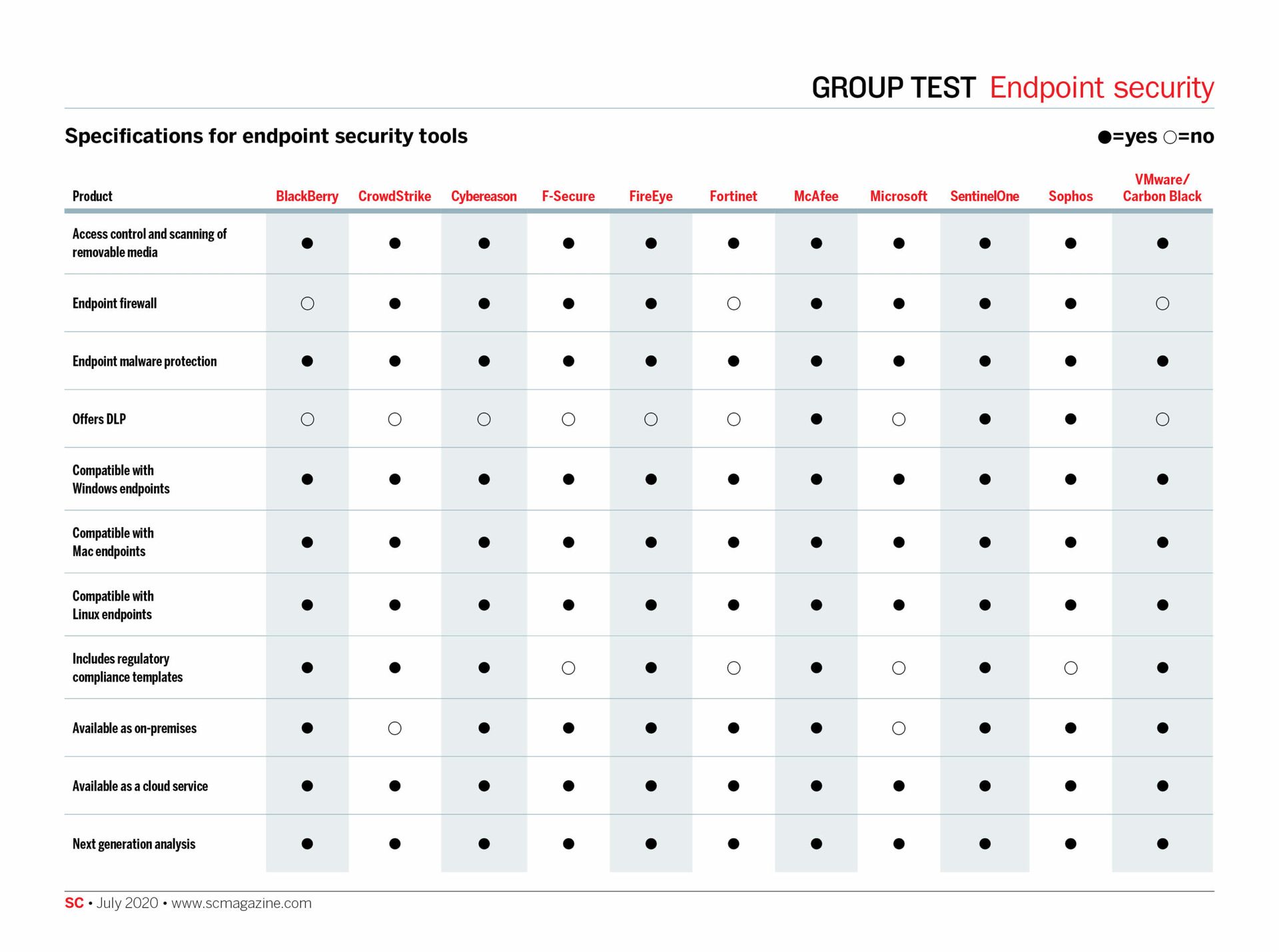
Click on the chart below for the full-size version