A well-run vulnerability management program removes the guesswork, says Katelyn Dunn.
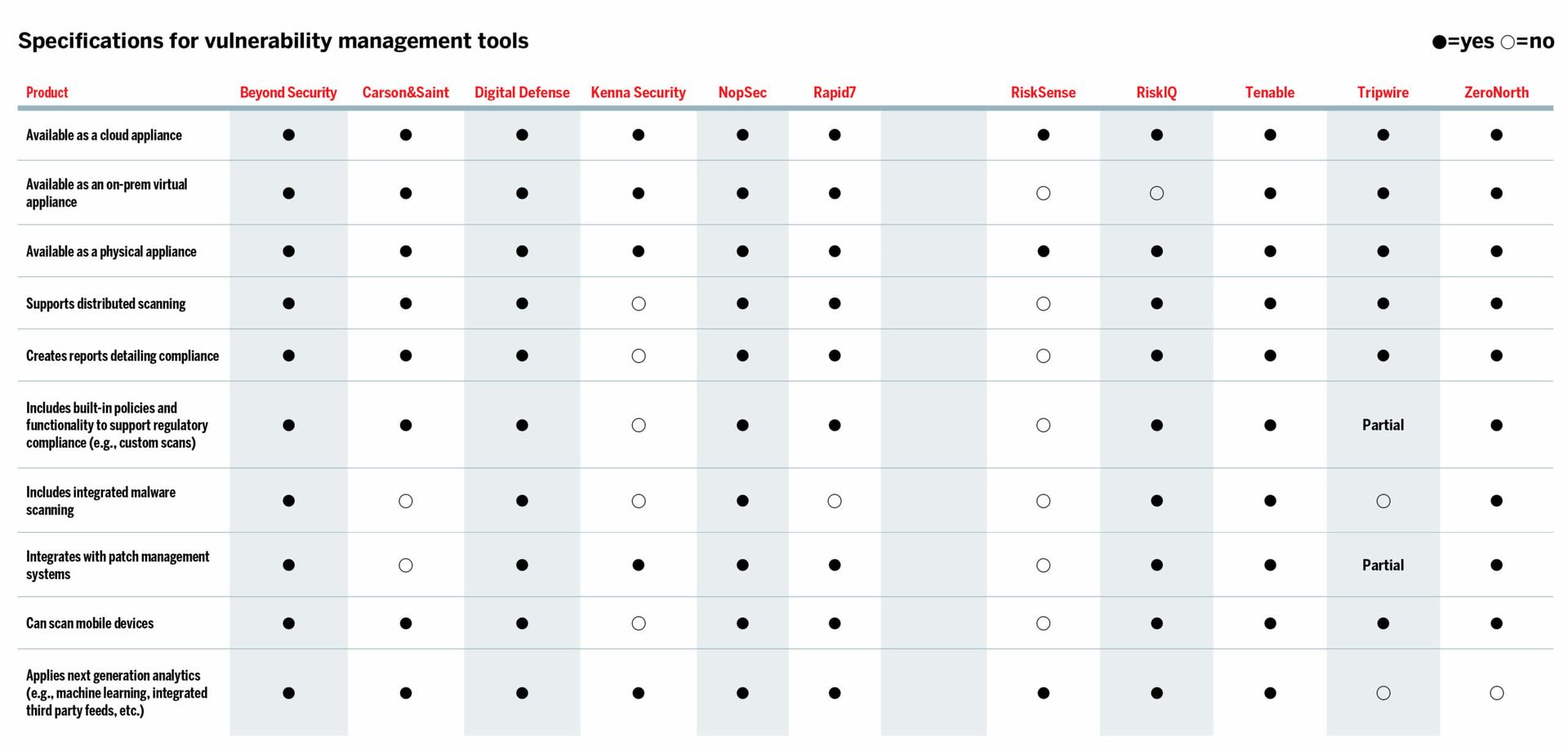
his month, we revisited a mixture of familiar and new faces. Vulnerability management is such a basic security element that occasionally it gets overlooked. However, these tools should be a staple in every security arsenal by now. In some cases, organizations may deploy more than one of these solutions in their environments, as vulnerability management solutions often complement each other.
The first step to achieving and maintaining a sound security posture is to have full visibility of environmental assets. After all, organizations can’t protect what they can’t see, nor can they understand the full impact of vulnerability exploitations if they do not first know that these vulnerabilities exist. Several of the vulnerability management solutions here have scanning abilities that enable asset discovery to provide a comprehensive view of an environment. As a result, the scans point at all assets, which is crucial because vulnerability management programs cannot succeed without quality data.
A well-run vulnerability management program takes the guesswork out of the process, brings vulnerabilities to light before it is too late and demonstrates where remediations would have the most impact. This effective approach ensures that security teams focus on the right issues, stay on top of their workloads and keep organizational security postures in check.
These tools have kept pace with the changing threat landscape over the years, and their features and capabilities continue to evolve. They include compliance-based reporting, predictive machine learning algorithms, zero-day protection and ticketing systems, which address risk exposure.
As exploits continue to grow in sophistication, security tools must mirror that growth to stay ahead of threats. As with many other cybersecurity solutions, vulnerability management tools increasingly incorporate more artificial intelligence and machine learning capabilities. CVSS-based scoring is limited in prioritizing vulnerabilities. Many vulnerabilities that score high with CVSS do not even have any known exploits. It is best to prioritize exploitable vulnerabilities first, followed by mission-critical workstations, then vulnerabilities with high CVSS scores. The machine learning-based algorithms make configurable, weighted asset scores possible, and therefore can provide accurate vulnerability prioritization tailored to business-specific practices and ensure environment scalability.
Overall, these tools have kept pace with the advancements we expected to see. They will certainly bolster security postures and offer valuable features like scheduled and automated scans, machine learning-based business context and effective reporting with compliance support. In some cases, these solutions include step-by-step remediation guidance. The robust API offerings seamlessly integrate with other security tools, enrich existing security investments, ensure efficacy, remediate vulnerabilities as quickly as possible and yield a welcome ROI. Do you know where your vulnerabilities are?
Pick of the litter
Kenna Security Kenna.VM offers undisputed evidence-based, real-time threat intelligence and risk scoring focused on active exploits. This solution is backed by comprehensive, proprietary data science that efficiently aggregates and analyzes scan data to provide role-based visibility and personalized remediation guidance. Even the most demanding company can confidently move forward with Kenna.VM to align its business and security needs, making this an SC Labs Best Buy.
Rapid7 InsightVM leverages impressive threat intelligence that provides the visibility necessary to detect, prioritize and remediate vulnerabilities. The platform has automated remediation capabilities that drastically reduce the time to remediation, yet still leaves room for human decision-making prior to patch deployment. The ingestion capability, remediation assistance and scanning ability make Rapid7 InsightVM our SC Labs Recommended product for this month’s round of reviews.
Check out all of May's reviews...
Beyond Security beSECURE 20.3
Carson & SAINT SAINT Security Suite 9.7
Digital Defense Frontline Vulnerability Manager
Kenna Security Kenna.VM
NopSec Unified VRM 5
Rapid7 InsightVM 6.6.1
RiskIQ Digital Footprint
RiskSense RBVM 8.15
Tenable.io and Tenable Lumin
Tripwire IP360 9.1.1
ZeroNorth The ZeroNorth Platform