Video games, quiz show competitions and undercover “mole” operations are among the more inventive ways companies are trying to spice up their security awareness training.
And they should: a new study of 1,000 U.S. employees by Osterman Research demonstrated just how counterproductive boring security awareness training can be: Surveyed employees who found training to be very interesting were 13 times more likely to say that it fundamentally changed how they think about security than those who felt the training was boring.
So how can organizations make lessons more memorable, engaging and enticing, such that employees feel rewarded for participating, but also retain the lessons and apply them in real life?
This is the fundamental principle behind gamificaton – a technique designed to improve trainees’ sentiments toward security awareness while also boosting engagement and, hopefully, retention. Several top experts in security training shared with SC Media some prime examples of this gamification in action, and the psychological principles behind why this technique can be effective.
Defining gamification
First, it should be noted that not everyone has the same definition of gamification. For some, the concept is broadly considered to be the delivery of creative and interactive lesson content.
“Interactivity is critical for fostering engagement,” said Bradley Hayes, chief technology officer at Circadence. “Any kind of material that doesn't include an active participatory element is at risk of resulting in low engagement, low recall and a perception of low value or a waste of time. Especially with remote instruction and remote training being the new norm, it's essential that exercises and lessons be designed with interactivity and maximizing engagement as a priority.”
Indeed, a report presented at the USENIX SOUPS security conference last August revealed that training measures leveraging videos and interactivity were more effective than traditional training, with employee lesson retention lasting at least six months longer.
But others have a narrower definition of gamification that focuses on having some kind of reward-based component that incentivizes trainees to complete training exercises.
“People think that if they embed a game within their training or their videos they made it gamified. That's not gamification; that's still providing awareness training, but in a more creative way,” said Ira Winkler, president of Secure Mentem. “Gamification is essentially a reward structure.” He pointed to other professions to offer examples: sell more in sales, and get a free trip; fly more with a particular airline, get free upgrades or drink certificates.

“What you're doing in gamification is creating a structure to reward people for demonstrating the desired behaviors that you want.” In training, participants may earn a prize for successful completion of a program, or the reporting of phishing messages to the security team.
Winkler says there’s an applied behavioral science behind this strategy: Most employees will choose to continue unsafe practices such as reusing passwords, unless one of two things happens: they conclude that acting responsibly will result in a measurably more positive outcome for them, or their neglect of security practices results in a negative outcome.
Until that negative event happens, “the consequence for ignoring the behavior is positive, because you have one less password to acknowledge or remember," Winkler said. Furthermore, he added, awareness has only a 20 percent impact, even if delivered through a game, while consequences have an 80 percent impact or more.
Michael Osterman, president of Osterman Research, offered up his own take. “The simplest form of gamification is immediate feedback when you answer some prompt: Get it right, and you get a star or a point or a badge. Akin to getting likes on a social media, this kind of immediate feedback answers the very simple but powerful human need for validation."
More ambitious is an approach where participants can accumulate points from across different activities, perhaps arranged into a story or journey, competing against others inside or outside their company.
But that is not easy to execute.
“The complex interconnectedness of such an approach means it is hard to customize and sometimes hard to integrate into a company’s existing [systems],” said Osterman. “I’ve seen rich gaming deployed well with small teams and in concentrated deliveries, but not yet as a full-on awareness program tool."
Putting the fun in security fundamentals
For all the complexity of an immersive experience, Circadence’s gamifed cybersecurity training platform, Project Ares, offers end users fully interactive “missions” and “battle rooms” featuring minigames designed to reinforce key cybersecurity concepts and skills among users.
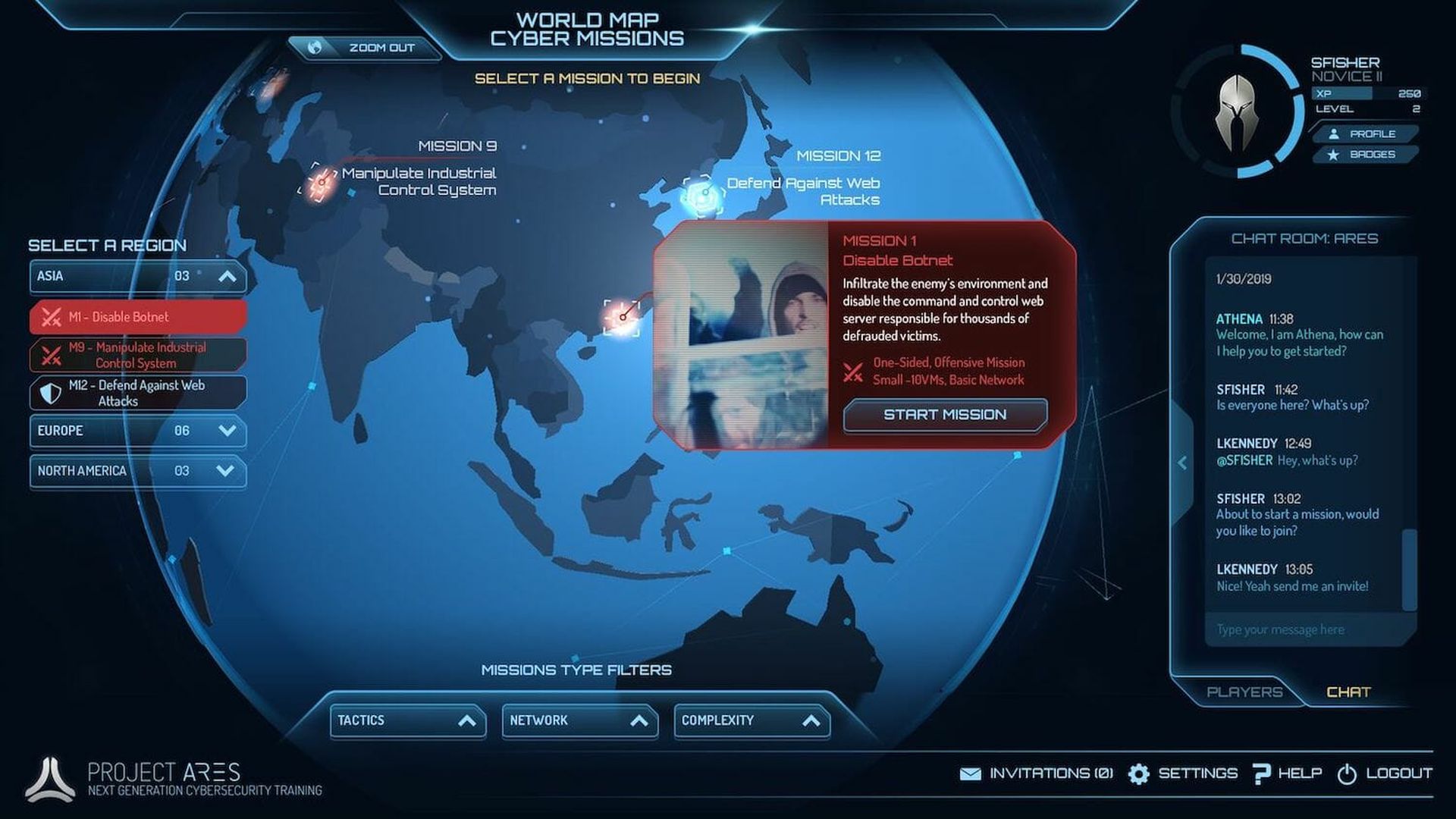
“These scenarios incorporate gamification elements including backstory, leaderboards, hints, non-player character opponents and an intelligent virtual agent assistant, all of which contribute toward engagement by adding a fun component and an exciting backdrop against which the content is being delivered,” said Hayes.
In one mission, players assume the role of a cyber pro at a financial services company who must disable a botnet launching DDoS attacks. “Through the mission, player engagement and performance are tracked and analyzed, made available in the form of after-action reports viewable by the trainee and their organization that can be analyzed later or compiled together as part of summary statistics for the entire workforce undergoing the training,” Hayes explained.
Another exercise, called RegExile, behaves like a video game in which trainees are required to quickly type in “regular expressions” (i.e. code strings used to detect patterns in data and block malware) in order to blow up attacking “codebots” before they inflict damage on your assets.
Minneapolis for-profit online education company Capella University uses Project Ares to train students in its adult learning program.
“Adult learners consistently state they want courses to teach them skills that they can apply to their real-world jobs,” said Dr. James Barker with Capella University’s School of Business and Technology. “Project Ares provided us with a platform to execute cyber missions, that have a very real-world feel to them.”
The missions often promote teamwork – an important attribute among security teams – and provide an opportunity to analyze various hypothetical attack scenarios, identify the vulnerabilities that allowed them in, and recommend how to prevent attacks in the future, Barker said.
But what are the key ingredients that make gamified security lesson plans like these work?
“Making security and privacy issues engaging and entertaining is a matter of finding the human drama or the mystery in them, and I really do think it’s possible with any content,” said Tom Pendergast, chief learning officer at MediaPRO, which sponsored the Osterman Research study. “Case in point: an exploratory interaction that asks you to figure out how to classify different data types, set against a surf background because it’s part of the California Consumer Privacy Act. It takes data classification and makes it fun. Or a block-the-hacker game where you race the hacker to your building by answering questions correctly along the way.”
“Stories, real-life examples, rewards, beautiful pictures – these are the tricks the designer uses to enliven any content,” Pendergast continued. On the other hand, “Fear, big blocks of content, dull graphics – this can make any content boring.”
Osterman cited PwC’s simulation program “Game of Threats” as a good example of effective gamification that allows users to “role play being a defender and an attacker” during a data breach. He also cited “Security Feud,” a training game from Living Security based on the quiz show “Family Feud.” A game such as this “taps into humans’ natural desire to compete and win,” he said.
And there are many ways to potentially stoke the fires of healthy competition: “For example, awarding points for correctly identifying a phishing attempt will entice users to keep competing so that they can top a leaderboard, discuss how well they did around the water cooler, and so forth,” said Osterman. “This is particularly true if there is some clearly stated goal that users can attain by reaching a milestone.”
This concept again leverages the principles behind positive reinforcement. “Consider if the TV game show 'Jeopardy!' did not award or subtract points for right or wrong answers, respectively, but contestants merely answered questions,” said Osterman. “It simply wouldn’t be entertaining.”
Masha Sedova, co-founder of Elevate Security, said that one of her favorite gamification rewards is making contributions to a charity for every employee that completes the security training program before a specified deadline.
The best games, she said, don’t reward participation as much as they reward the outcome like when the training program is completed and/or certain observable results are achieved. Participation alone isn’t enough. Put simply: “We’re trying to get people to not mute it and skip to the end,” said Sedova of online training courses.
Games can even be successfully incorporated into real-world security practices, not just hypothetical or simulated situations. Case in point: Sedova knows a company that created a unique physical security exercise designed to stop tailgating, an act whereby an unauthorized person manages to enter a locked or secured area by closely following behind one or more authorized individuals.
The game: One person in the office is secretly designated as a mole who must walk in without a badge, repeating that infraction each day until somebody notices and escorts him or her back to reception. The person who successfully catches the mole receives a stuffed animal mole for their desk.
“And it was this roaming trophy for having been the most recent mole catcher,” said Sedova, noting that winners would go on to accessorize the mole with little hats and bows. “At any given point it was teaching employees vigilance, because you knew that there was a chance to succeed at this, but someone was testing you.”
But here’s the kicker: while competing in this daily game, company employees caught actual, non-approved tailgaiters entering their workspace.
Band-Aid to a larger problem?
While Sedova said gamification is a useful tool, she said it often masks a larger issue: the inability to make training relevant to the user in the first place so that bells and whistles aren’t necessarily needed to make training less boring.
“We try to add games and widgets because we do not spend the time on making sure that the person understands what they need and why they need it, and are motivated to take the training,” she said.
Most training is one-size-fits-all, because it’s easier for security to implement that way. But what makes something interesting is relevance to the individual.
"Current awareness training is basically the equivalent of a billboard that has no idea who I am, what I'm good, at what I'm bad at, and frankly doesn't care about my intelligence level," she said. "It's boring because it doesn't meet me where I'm at."
When a security exercise is relevant to fixing your own deficiencies, that's when it becomes impactful, she said. By explaining to users that they need help in a particular area – for instance, they're good at detecting simulated phishing emails, but are less proficient at reporting these scams compared to their peers – then they become driven to make improvements, especially through training customized toward those goals.
Once companies make training more relevant, Sedova continued, then they can add gamification elements as a secondary measure to improve engagement. As a byproduct, these games may even deliver a bonus benefit: improving employees' perceptions of the IT and security department.
“Security teams are always seen as the department of 'no,' and having an engaging and a fun experience helps put the security team into a positive light," said Sedova. "Because in moments of vulnerability or failure, you want an employee to say, 'hey, I need your help.'"



