Several menacing new ransomware threats have been sprouting up like weeds this summer, tormenting victims with both traditional file encryption and the publishing of stolen data on leak sites. Ransomwares like Avaddon, DarkSide and Conti have joined an already crowded field that includes prominent human-operated ransomwares such as Sodinokibi (aka REvil), Maze and others.
And when these new threats do strike, victims may be at an even greater disadvantage than usual because of the lack of intelligence to create useful threat profiles. Indeed, "new variants of ransomware present both technical and logistical challenges to victims and service providers,” said Bill Siegel, CEO and co-founder of Coveware.
The emergence of possible new threat groups plotting out and executing these ransomware attacks also adds a sense of mystery, although it remains unclear if some of these actors have previous malware affiliations that could offer clues as to how they operate. Based on publicly available reports, DarkSide and Avaddon remain largely unknown quantities -- although Siegel told SC Media that both ransomwares are operated by actors who behave as if they’ve done this before. Conti, on the other hand, has been officially linked to the operators of Ryuk ransomware.
Whenever a new ransomware surfaces, the technical challenges for the security community revolve around analysts’ ability to know precisely what they’re dealing with. This means gauging what data has been encrypted, if the malware can spread further, and if anything is salvageable.
“With a new variant, a technical review is often a priority to ensure the encryption is clean,” meaning whether it can be decrypted at all or if everything is permanently corrupted, explained Siegel. “From there, trying to link attribution of the group is the next priority, as most new variants are spun up by existing actors that are moving on to new malware kits.”
Jen Miller-Osborn, deputy director of threat intelligence for Unit 42 at Palo Alto Networks, agreed: “With any new attackers, especially involving ransomware, it's important to establish whether or not the files can actually be decrypted,” she said. “There have been multiple cases where misconfigurations or other coding mistakes in the ransomware meant that once files were encrypted, there was no way to decrypt them.”
But it’s not always easy getting your hands on a sample to perform such analysis, said Tarik Saleh, senior security engineer and malware researcher of DomainTools, who agrees the threat intelligence community often finds itself “playing catchup with the data” when a new ransomware emerges in the wild.
“We have to generally wait until ransomware samples are made available either publicly or in certain CTI [Cyber Threat Intelligence] communities. Until then, we have to rely on the intelligence of those who have interacted with the ransomware.”
In the case of ransomware-as-a-service (RaaS), threat hunters can patrol the dark net forums where ransomware developers offer their tools to prospective affiliates who are willing to share a percentage of their ill-gotten extortion profits. But even then, said Saleh, “we generally can’t purchase them.”
Which means, in many cases, some poor victim has to be the guinea pig. “You need a patient zero. Before you can get any intel on an actor somebody has to have had a bad day already,” said James Shank, chief architect of community services at Team Cymru.
Even upon receiving a sample, learning how a new ransomware works is a laborious task. Unfortunately the first victims of a new malware, the clock keeps ticking and the pressure keeps mounting – especially when the extortion price goes up the longer the attack goes on.
“While ransomware is usually fairly simple from a technical standpoint, reversing engineering new malware always takes time,” said Miller-Osborn. “In some cases, threat researchers have… been able to figure out how to decrypt the files, ensuring a ransom won't have to be paid. The fact that this often needs to be done quickly during an ongoing incident can mean long hours.”
Another obstacle when confronting new ransomware is understanding how to best interact and dialogue with unknown attackers. Without any past precedent, it’s hard to establish if adversaries will keep their word, if they will reasonably negotiate, or if they’re amateurs or professional crooks.
“If you have a large data set of behavioral experiences, it is relatively straightforward to design a negotiation strategy based on internal attribution,” said Siegel. “Truly new actors, using new kits, are much more challenging, as there is no direct prior behavior to match.”
Saleh ultimately discourages organizations from negotiating or paying at all, regardless of who the actor is.
“While I think, on paper, it’s easier to trust someone who you know some information about, it ultimately doesn’t matter when it comes to ransomware,” said Saleh. “Unfortunately, the trust model has been broken by the threat group attacking you in the first place. I completely empathize with businesses that have paid the ransom, but disagree with it. Ransomware operators will continue their attack campaigns if they are able to be successful. Once again, we shouldn’t trust any threat actor despite how much data we have on them...”
The Latest Ransomware Threats
Since emerging in June, Avaddon has been a subject of a series of analysis reports from companies such as Cofense, DomainTools, Proofpoint and TrendMicro.
Avaddon was first spotted being delivered to a wide range of targets via the Trik or Phorpiex botnet, “signaling threat actors’ willingness to cast a wider net in search of ransom payments,” according to Cofense's report.
Written in C++, the malware has been found available for sale on Russian language dark web forums as a RaaS offering, and is designed to target Windows 7 or Windows 10 systems “running Internet Explorer that might not have ATP/Defender enabled,” the DomainTools report said. As of Aug. 13, the U.S. is home to the largest percent of victims – 25 percent – but the ransom note supports nine different languages. Russian is notably not among them, and the malware comes with features or end-user license agreements that prohibit attacks on CIS countries – suggesting the malware has Russian origins.
On Aug. 8, the Avaddon actors launched their own data leak site to pressure victims into paying a ransom before their exfiltrated data is published for the world to see. The malware itself doesn’t have a data exfiltration component built in, so its distributors have coupled it with the RaccoonStealer info-stealer, Cofense said.
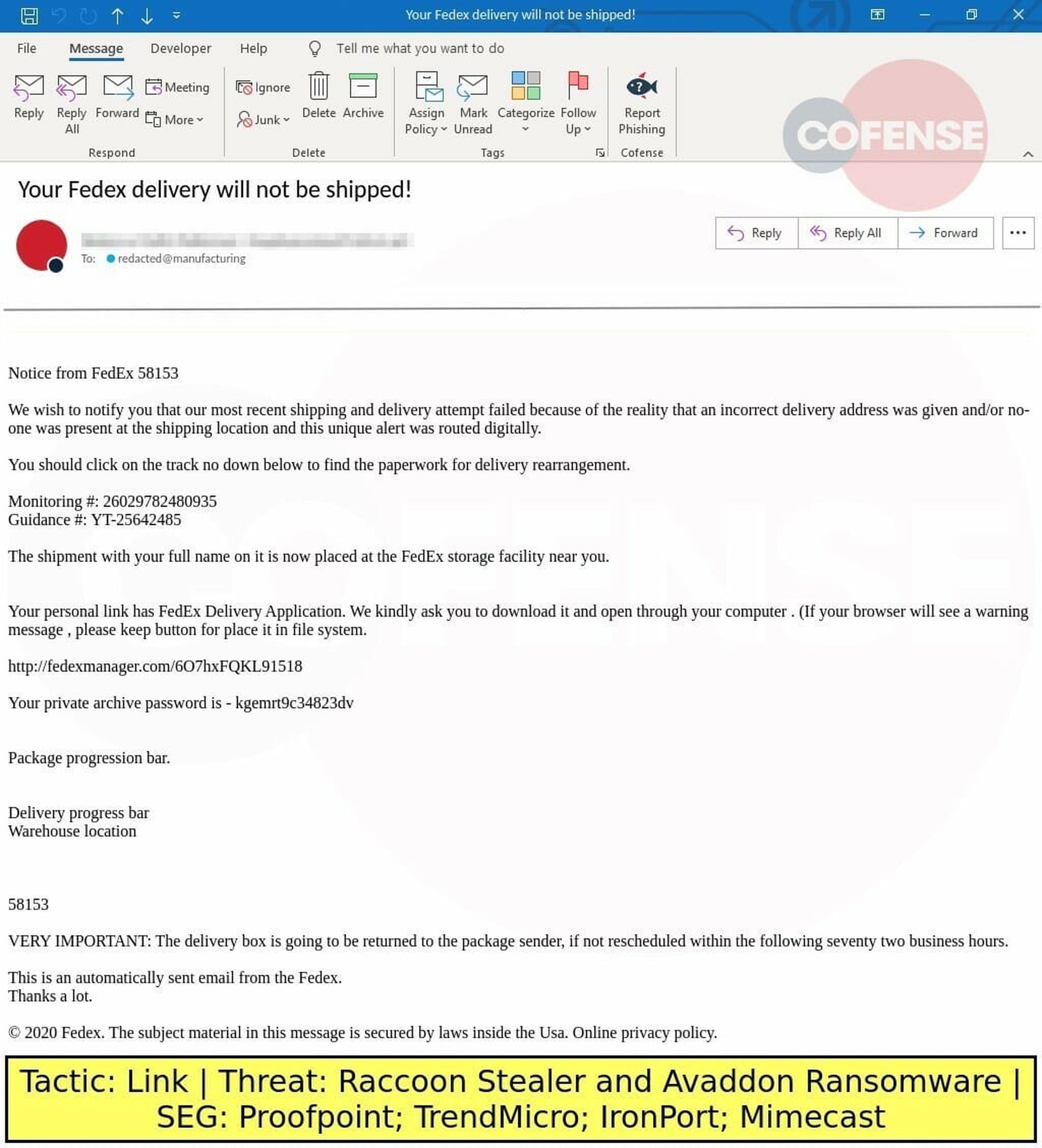
In recent weeks, Cofense has reported on an email-based phishing campaign that impersonated FedEx and delivered Avaddon via SmokeLoader, and TrendMicro and Proofpoint both detailed a campaign that distributed Avaddon through phishing emails with evocative subject lines encouraging readers to check out an attached photo. If the attachment was opened, the malware reportedly would use PowerShell and the BITSAdmin command-line tool to download and run the main payload.
The actor behind the human-operated DarkSide ransomware, meanwhile, is going after especially large paydays.
This particular group hit the scene on Aug. 10 and targets businesses with deep pockets, seeking ransoms ranging anywhere from $200,000 to $2 million, BleepingComputer recently reported. The group has claimed it won’t attack non-profits, governments, or businesses in fields of medicine or education – although that remains to be seen.
Among the first prominent victims to be attacked was U.S. and Canadian land developer and home builder Brookfield Residential, a division of the $56 billion company Brookfield Asset Management.
Members of this DarkSide gang reportedly claim to be experienced, former ransomware affiliates who formed their own operation because they could never find the “perfect product.” The ransomware creates a customized executable and file extension for each victim, encrypts files using SALSA20 andRSA-1024, and exfiltrates data that later may be posted to a leak site, BleepingComputer reported, crediting malware analysis to researchers Vitali Kremez and Michael Gillespie. The ransomware also uses an embedded UAC bypass feature that can encrypt a computer even when running as a low integrity user, Minerva Labs reported on Wednesday.
Further analysis reportedly uncovered certain similarities with Sodinokibi/REvil ransomware, including the same ransom note template, the use of a PowerShell command to delete Shadow Volume Copies, and the avoidance of targeting companies based in CIS countries.
This week it was also reported that the operators behind Conti – the confirmed successor to Ryuk ransomware – have also created their own data leak site for extortion purposes.
Conti has been affiliated with the TrickBot modular banking or trojan, BleepingComputer stated. It’s a human-powered, RaaS offering for experienced hackers as affiliates who receive a large share of ransom payments. The malware sabotages files using AES-256 encryption and delete Windows Volume Shadow Copies to prevent recovery.
Conti is considered relatively unique due to several of its features and behaviors, Carbon Black recently reported: it uses multitudes of independent threats to execute as many as 32 encryption operations concurrently; it uses command line options for controlling how to scan for encrypt able data, which enables the skipping of local files while specifically targeting networked SMB shares; it leverages Windows Restart Manager to close applications and make sure they are encrypted; and it possesses various anti-analysis features.