What is DAST and what is SAST?
To get the definitions out of the way, dynamic application security testing (DAST) is a black-box testing methodology where a running application is tested from the outside. A DAST tool crawls the application and probes it for runtime vulnerabilities just like an attacker would. On the other hand, static application security testing (SAST) is a white-box security testing method that inspects the application source code to identify potential security vulnerabilities.
So, in a nutshell, DAST checks a running web application while SAST checks its static code.
What is IAST, then?
Interactive application security testing (IAST), sometimes called gray-box testing, occupies the middle ground between dynamic analysis (black-box testing) and static analysis (white-box testing). Depending on the vendor, IAST can be a standalone security testing tool that adds some dynamic testing capability to SAST or a way to add source code insights to dynamic testing. For Invicti specifically, IAST is implemented as a server-side agent that constantly communicates with the core vulnerability scanner to find more than DAST alone could (more on that later).
SAST vs. DAST coverage in web application security testing
Coverage is a fundamental attribute of security testing, both within a specific app and across your entire web application environment. To accurately assess the security of an application, your security testing solution needs to know what to test and how to interpret the things it finds in your application.
SAST works on the application source code, so you need to have that code along with tools that support a specific programming language and web application framework. For multiple different technology stacks, that may mean multiple SAST tools. In a wider context, SAST coverage is generally limited to apps that are in active internal development since you need both the code and the right testing toolchains. So while you may hear opinions that only SAST provides full test coverage because it tests all code, this is only true for the codebase of a specific application and the limited subset of security risks that can be detected statically.
DAST tools such as vulnerability scanners, on the other hand, are technology-agnostic because they test applications from the outside and examine their behavior, not their source code. This allows DAST to cover any number of applications, regardless of tech stack, development status, or source code availability, testing everything that is externally accessible to a visiting browser. Leading dynamic scanners can identify a wide range of vulnerabilities, including misconfigurations and other runtime issues. They also support modern authentication schemes to access site sections and functionality available only to authenticated users.
Get the Invicti white paper on API security testing to learn why this is a crucial part of web security.
Security testing accuracy and efficiency with SAST vs DAST
False positives are always a hot topic in application security testing, understood both as erroneous results and valid but non-actionable findings. SAST tools, in particular, have a reputation for flooding developers with security issues that, while technically accurate, are irrelevant in a specific context. This requires tedious fine-tuning to prevent developers from being flooded with false positive reports that consume their time for no security benefit and, in effect, are routinely ignored.
The big advantage of DAST is the potential to identify actual exploitable vulnerabilities rather than merely signaling potentially insecure code constructs. While some early DAST tools struggled to deliver on that promise, industry-leading modern DAST solutions rely on proof, not suspicions, and some can even automatically confirm exploitability to flag high-priority issues. This makes DAST the ideal approach for time-strapped development teams, allowing them to focus remediation on vulnerabilities that really matter.
Finding vulnerabilities with DAST and SAST
To give a specific example, let’s say an application fetches data from an SQL database based on user input from a web form. A SAST tool might identify the source code fragment that does this and warn the developer that the SQL query in a specific line of code is assembled in an insecure way and could potentially lead to an SQL injection (but might not). A DAST tool will find the web form on a page and run security checks to simulate actual SQL injection attacks. If any of the test attacks succeed, the scanner will report that the application has an SQL injection vulnerability on that specific page:
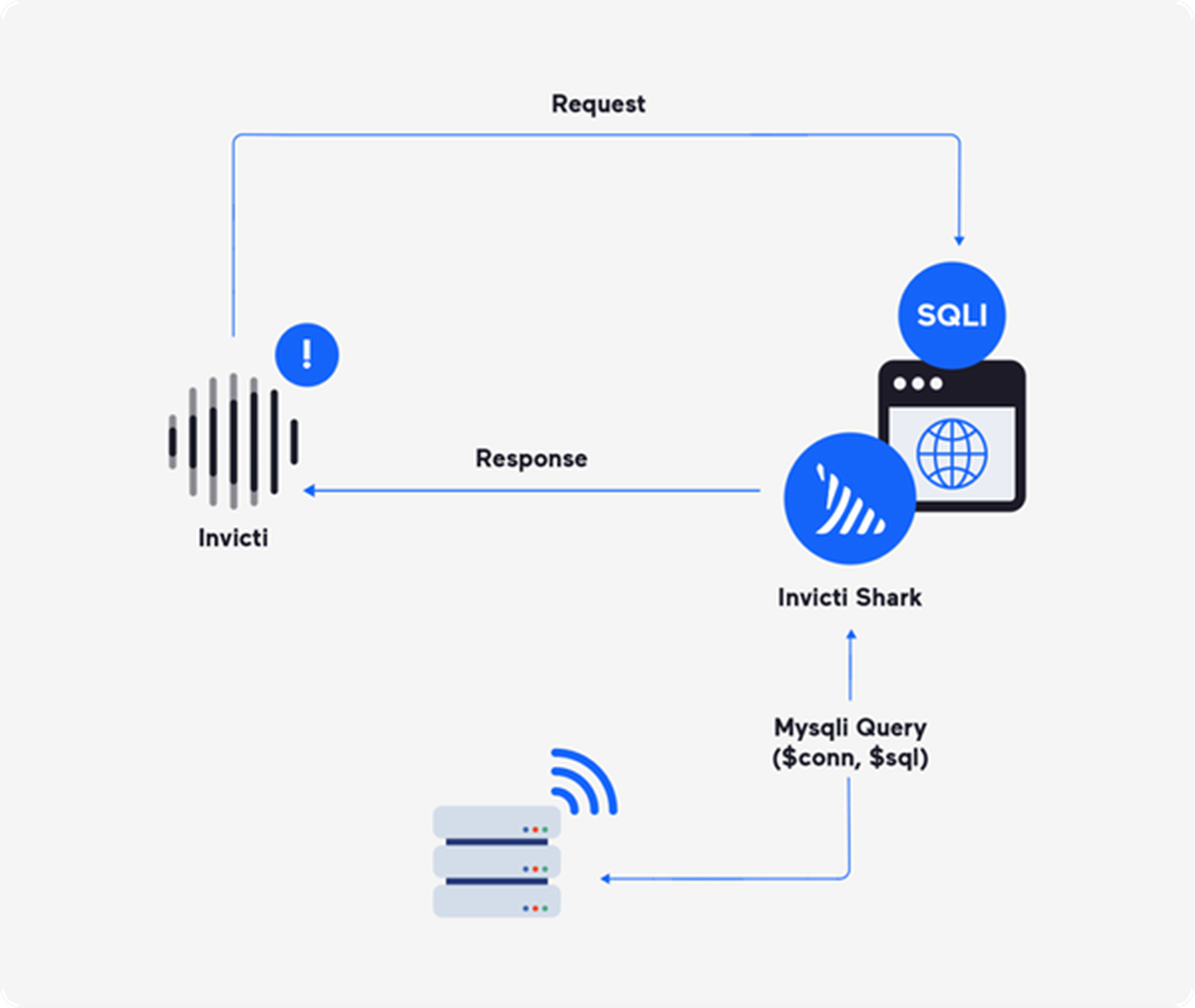
So the difference between SAST and DAST results is the difference between “we should probably look at this” and “we need to fix this now” – especially important for weaknesses such as cross-site scripting (XSS), where many suspicious code constructs will never lead to an actual exploitable vulnerability.
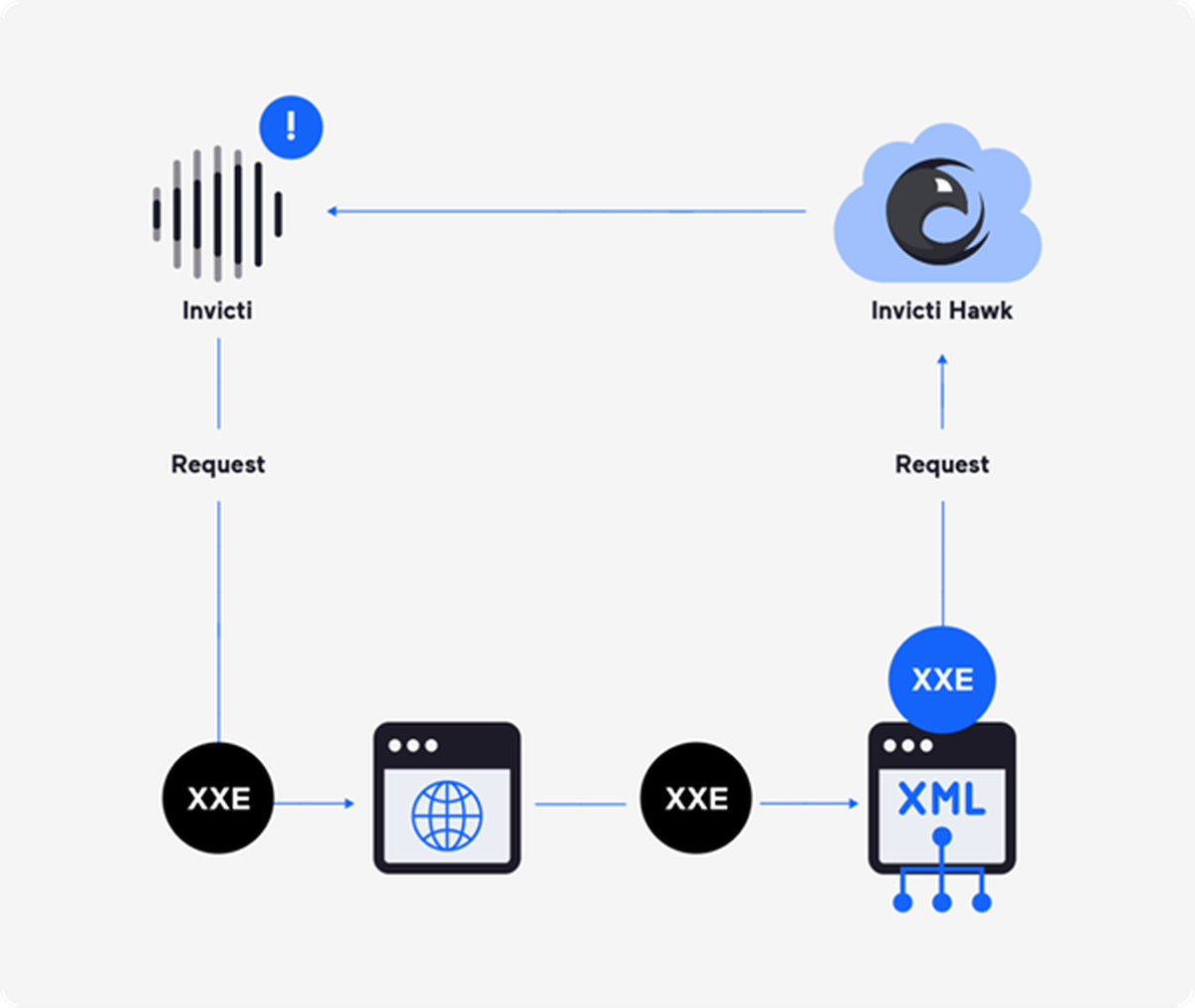
The quality of DAST tools varies widely, but any decent DAST should also identify out-of-band vulnerabilities – security weaknesses that don’t yield immediate reactions to security checks. Invicti uses its integral Hawk component to listen for traffic that signals out-of-band and second-order vulnerabilities such as XXE:
Building SAST and DAST into your SDLC
Security testing from the early stages of your software development lifecycle (SDLC) is crucial to find and remediate vulnerabilities before they make it into later phases or even into production. Source code analysis is the most natural way to find and eliminate security defects already during early development. SAST is typically easy to integrate with development environments and workflows, whether as an IDE checker or standalone analysis process. However, because SAST cannot identify runtime vulnerabilities and misconfigurations, some form of dynamic testing is still needed in the SDLC.
Regardless of some long-standing misconceptions, DAST tools also can (and should) be integrated into the SDLC. While it’s true that DAST can only be done on a deployed application, most modern web frameworks can autogenerate code for prototyping at any stage of development to make this less of a hindrance. The big advantage is that DAST can run at multiple stages of the SDLC, from partial testing in development to full-scope tests in staging and even production testing by security teams. Because DAST checks the entire application for vulnerable behaviors and responses regardless of the implementation details, it’s the recommended starting point for adding security testing into the SDLC.
The Invicti way: DevSecOps with DAST+IAST+SCA
With all the acronyms in AppSec, it’s easy to get drawn into choosing one AST approach over another or (worse still) ticking boxes to make sure you get all the acronyms, preferably in a bundle. The ultimate goal, though, isn’t to complete a shopping list but to find a way to get your web applications secure and keep them secure. The way to get there is different for each organization and rarely quick or easy. At Invicti, we’ve come up with one fast-track approach that builds on the truly unique capabilities and feature combinations of our products.
The Invicti solution is built around the industry’s most mature DAST platform and uses Proof-Based Scanning to automatically confirm the vast majority of exploitable high-impact vulnerabilities with no risk of false positives. These confirmed results can be sent directly to developers via out-of-the-box integrations with issue trackers and CI/CD pipelines to make sure that application security can keep up with the extensive automation of DevOps development processes. Each vulnerability report includes detailed remediation guidance, and each fix can be automatically retested, enabling organizations to set up a hands-off AppSec process that doesn’t interfere with development and leads to more secure code in the long run.
The core DAST engine can be complemented by an IAST tool with additional software composition analysis (SCA) capabilities. With an Invicti IAST agent installed on the web or application server, you can get more detailed crawl and scan results, more vulnerability confirmations, and SCA checks to detect vulnerable open source dependencies. IAST agents are currently available for PHP, .NET, Java, and Node.js, with more in development.