A plan of action makes all the difference during a cyber-attack. Without such a plan, a full-blown data
breach is likely. But with a specific set of guidelines to govern who does what in the early stages of an
attack, the damage can be kept to a minimum or avoided altogether.
“After experiencing a breach, organizations often realize they could have avoided a lot of cost, pain, and
disruption if only they’d had an effective incident response plan in place,” Sophos says in its recently
released incident response guide.
The guide was developed to help security teams define the framework for incident response planning.
The recommendations are based on the real-world experiences of Sophos’ Managed Threat and Rapid
Response teams.
What follows is a synopsis of the guide.
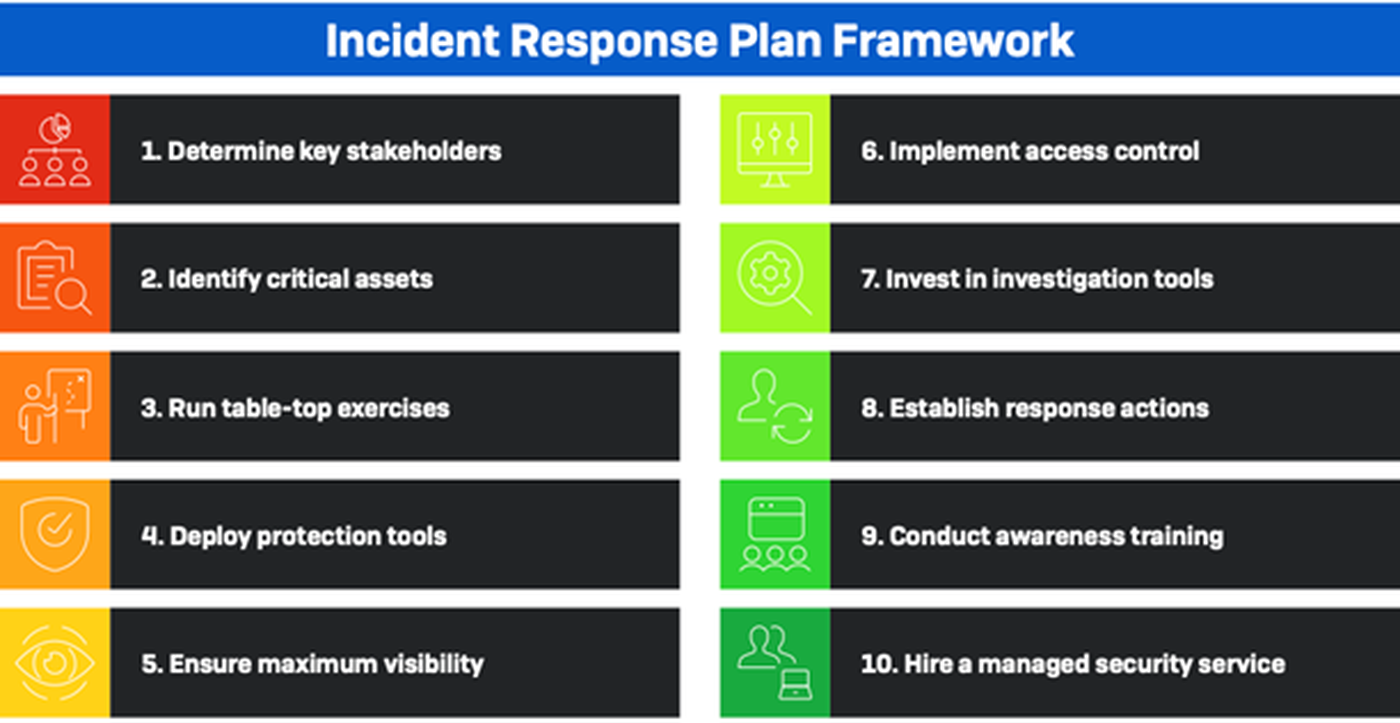
Ten steps to preparedness
The guide outlines 10 key steps any effective response plan should have:
Step 1 is about properly planning for a potential incident in a way that doesn’t place all the responsibility
on one team. An incident will likely impact almost every department in your organization, especially if
the incident turns into a full-scale breach. An incident response plan must include action items for all
departments.
Step 2 is about knowing what your organization’s most critical assets are, where they are located and
how to quickly determine if they have been compromised.
Step 3 is about constantly testing an organization’s response plan to ensure it will work during a real
attack. Tabletop exercises should test your organizational responses to a variety of potential scenarios.
Each scenario might also include stakeholders beyond the immediate technical team. Your organization
should determine in advance who needs to be informed when an attack is detected, even if the
company’s defenses held up to scrutiny.
Step 4 covers how to ensure your protection tools are properly deployed.
Step 5 is about achieving maximum visibility by collecting log data with a focus on endpoint and network
data.
Step 6 covers how to properly implement full access control.
Step 7 covers the types of investigative tools an organization needs, such as endpoint detection and
response (EDR) or extended detection and response (XDR).
Step 8 details the response actions that must be established, from isolating infected hosts to closing
exposed entry points.
Step 9 covers the key ingredients of employee awareness training.
Step 10 stresses the importance of considering a partnership with an outside managed security service
when your organization lacks the capability to handle a full incident response on its own.
The full guide is available for download here.



