Your enterprise can deploy Ping solutions in multiple ways, choosing the best option based on your unique needs. PingOne Advanced Services can greatly simplify deployment and maintenance by taking care of these efforts for you, giving your enterprise the ability to consume advanced IAM capabilities from the cloud.
As a Ping customer, the first step is migrating from an on-premises or public cloud environment. Below is a high level overview of the migration process.
Migration Steps
Ping’s professional services team can migrate your existing infrastructure to Ping’s cloud in as few as four weeks. The express migration consists of only six steps.
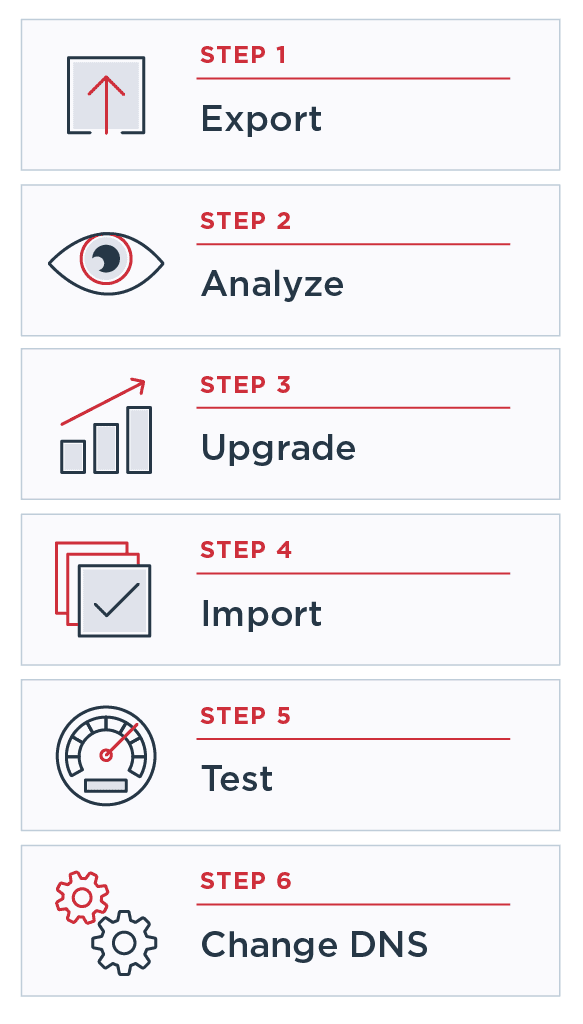
Step 1: Export
Export your existing configuration as a data.zip.
Step 2: Analyze
Analyze the configuration. Look for integration kits, virtual hosts, data sources, etc.
Step 3: Upgrade
Upgrade to match the version in PingOne Advanced Services. Upgrade integration kits where required or possible.
Step 4: Import
Import the upgraded data.zip file and deploy upgraded integration kits.
Step 5: Test
Change your host file and test. Make sure we’ve hit the mark on the migration before your users gain access.
Step 6: Change DNS
Use a CNAME to point your existing DNS record to your PingOne Advanced Services customer safe DNS name.WATCH THE WEBINAR REPLAY
Stop Maintaining Your IAM Infrastructure
When deploying software, an organization is responsible for all of the activities associated with product and infrastructure operations. Below is a sampling of the responsibilities Ping takes care of on behalf of your organization through PingOne Advanced Services.
Product Operation
The set of activities for installing and maintaining a product to meet an organization’s requirements.
- Promotion Pipeline - a structured path for delivering new code and features into production. It begins with development, progresses into testing and staging, and finishes with production.
- Custom Integrations - custom software solutions built for specific use cases. They often enable two or more products to effectively exchange information with one another.
- Base Configurations - the agreed descriptions of the attributes of a product, at a point in time, that serve as a basis for defining change down the road.
- Install / Upgrade - the process for running the latest product version, which allows organizations to take advantage of new features and security enhancements. It often delivers code that runs more effectively, which can save IT resources.
Infrastructure Operation
An enterprise's entire collection of hardware, software, networks, data centers, related equipment and processes used to develop, manage and support information technology services within an organization.
- Disaster Recovery / Backup - a set of tools and procedures that enables the recovery and continuation of vital technology infrastructure and systems during or after a natural or human-induced disaster.
- Scaling - the ability to dynamically autoscale when demand for IT resources increases during peak times or decreases during slower times, for IT resource optimization.
- Monitoring - a system that tracks IT infrastructure performance and health, and notifies administrators where potential issues may occur.
- Networking - a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data, using both software and hardware technologies.
PingOne Advanced Services can be deployed 70% faster than traditional on-premises software and can save about 50% in total cost of ownership over three years. PingOne Advanced Services ensures that you are set up to run smoothly, enabling you to focus on running identity and access management solutions for your enterprise without worrying about infrastructure maintenance. Begin your migration today!





