With all the hype surrounding zero trust over the past few years, those in the industry might reasonably expect that most organizations would have implemented it by now, or at least be in the advanced stages of doing so -- given its touted benefits as a way to reduce the risk of ransomware and other types of attack.
But many security pros still find zero trust a vague concept, according to a study conducted earlier this year by CyberRisk Alliance Business Intelligence. The survey of 300 IT and security decision-makers and influencers found that only 35% of respondents considered themselves very familiar with zero trust frameworks and controls. The remaining two-thirds said they had just a modest understanding of zero trust. Only 36% had implemented zero trust, but another 47% planned to adopt it in the next 12 months.
Those in the latter camp are driven in part by the need to close off excess access points that ransomware gangs can exploit, and to move beyond VPNs for secure remote access as the trend toward more remote work pushes that technology to its limits. Specifically, many organizations are interested in zero trust network access (ZTNA)
That’s because with remote access VPN, users are implicitly trusted with broad access to resources, which can create serious security risks. ZTNA, on the other hand, treats each user and device individually so that only the resources that user and device are allowed to access are made available. Instead of granting users complete freedom of movement on the network, individual tunnels are established between the user and the specific gateway for the application they’re authorized to access – and nothing more.
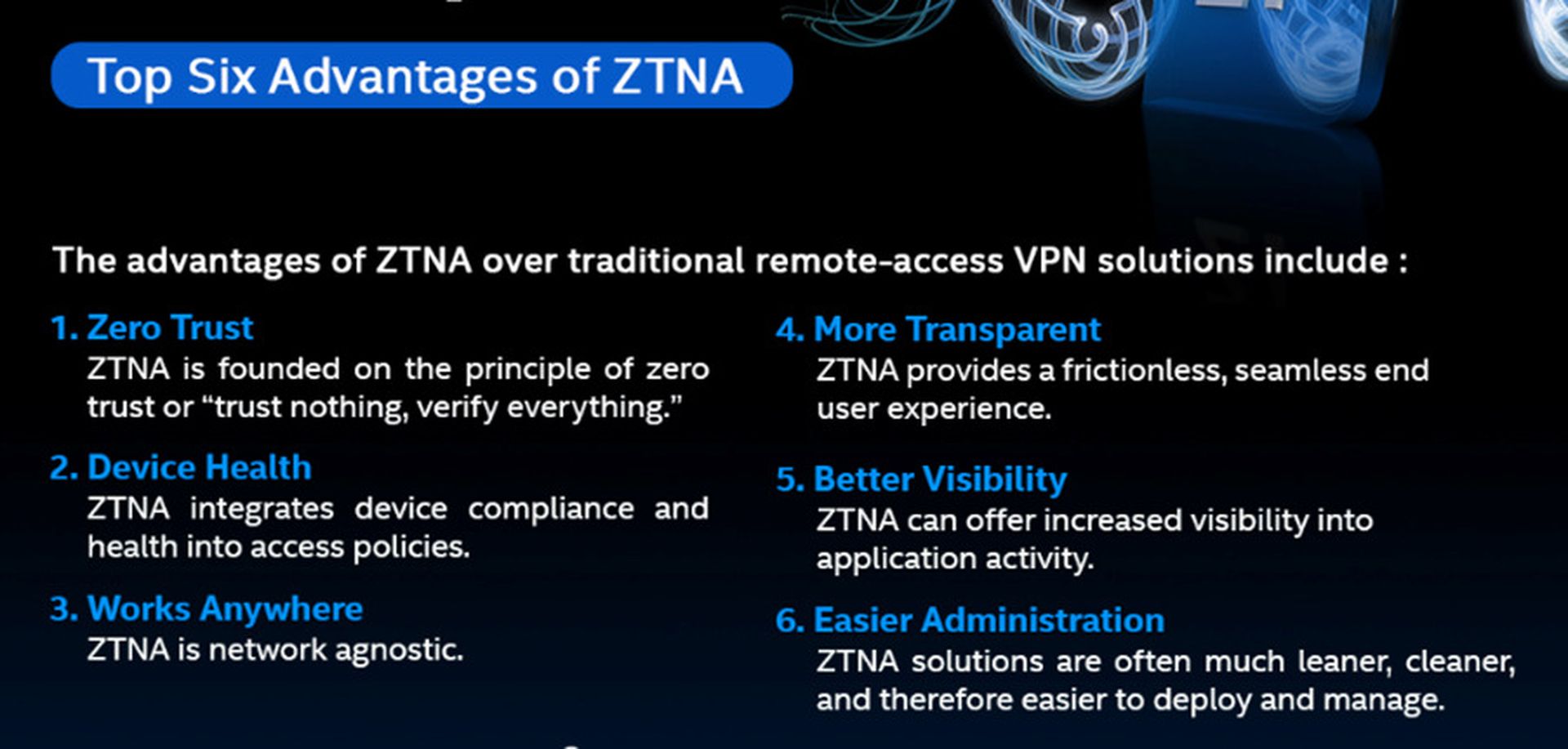
Security vendors are increasingly offering zero trust solutions as a way to combat ransomware, including Sophos, which published a report capturing six specific advantages to ZTNA. The following infographic captures the highlighted benefits: