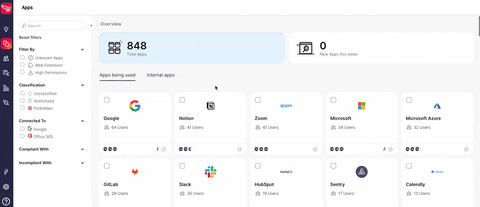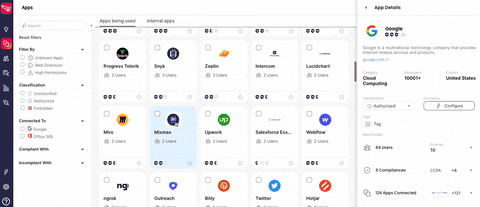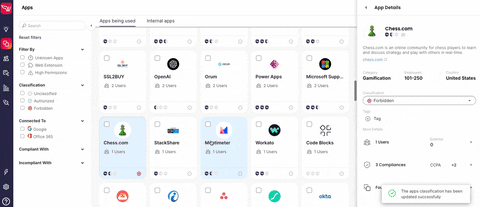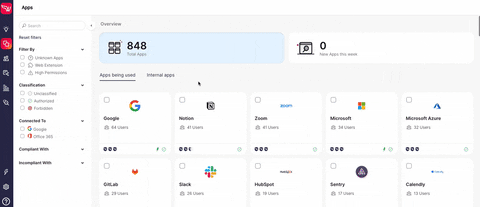
This past January, the SaaS Security Posture Management (SSPM) company Wing Security (Wing) announced its Free SaaS-Shadow IT discovery solution. Organizations can now gain insight into their employees' SaaS usage through a non-intrusive, self-service product that operates on a "freemium" model.
"Today's security buyers are far more careful in their purchasing decisions and rightfully so. We believe that you cannot secure what you do not know, so knowing should be a basic commodity. Once you understand the magnitude of your SaaS usage and the resulting attack surface, you can make an educated decision as to how you are going to solve it" - Galit Lubetzky Sharon, Wing's CEO.
The company reports that in Q1 alone, over 550 companies signed up for their self-service free discovery tool, adding to the company's existing customer base. They recently released a short report on the findings that were gathered from hundreds of SaaS-using companies, and the numbers are unsettling.
Quantifying the risks of decentralized SaaS Usage
In 84% of companies, employees use an average of 3.5 SaaS applications that have experienced data breaches in the past three months. On average, 55% of SaaS applications are utilized by a single employee. These data points form the basis for understanding the challenge of SaaS Shadow IT and raise important questions: Do employees truly need to grant access to all these applications? Are these applications, which have varying levels of permissions to company data, truly necessary?
The challenge arises from the decentralized and difficult-to-govern nature of SaaS, where its advantages can also introduce security risks when left unmanaged. While IAM/IM systems aid organizations in regaining control over a portion of their employees' SaaS usage, such control is typically limited to sanctioned SaaS applications. Often, SaaS applications are onboarded without involvement from IT or security teams, this is particularly true for those that don't require credit card details or offer free versions.
The Top Three SaaS-related risks
Maintaining a clean SaaS environment involves managing applications, users, and the information stored within and between them:
- Risky SaaS applications: These include applications that are more likely to be vulnerable. They may have been recently compromised, putting the organization's data at immediate risk. Or they may have low security standards, little or no compliances and no online credibility.
- Users related issues: The human factor is significant as employees often onboard SaaS applications themselves. They grant permissions without always understanding their implications.
- Data related risks: Data security risks in SaaS applications range from sensitive files shared on inappropriate platforms to secrets shared in public channels. Employees may also unknowingly leave external connections open by sharing files externally and forgetting about them.
Wing Security's free SaaS-Shadow IT discovery solution addresses the challenges posed by decentralized SaaS usage and provides cloud-based companies with valuable insights into their SaaS landscape. In 2023 companies no longer need to pay for SaaS-Shadow IT discovery, they can proactively mitigate risks and ensure a secure and compliant SaaS ecosystem, for free.