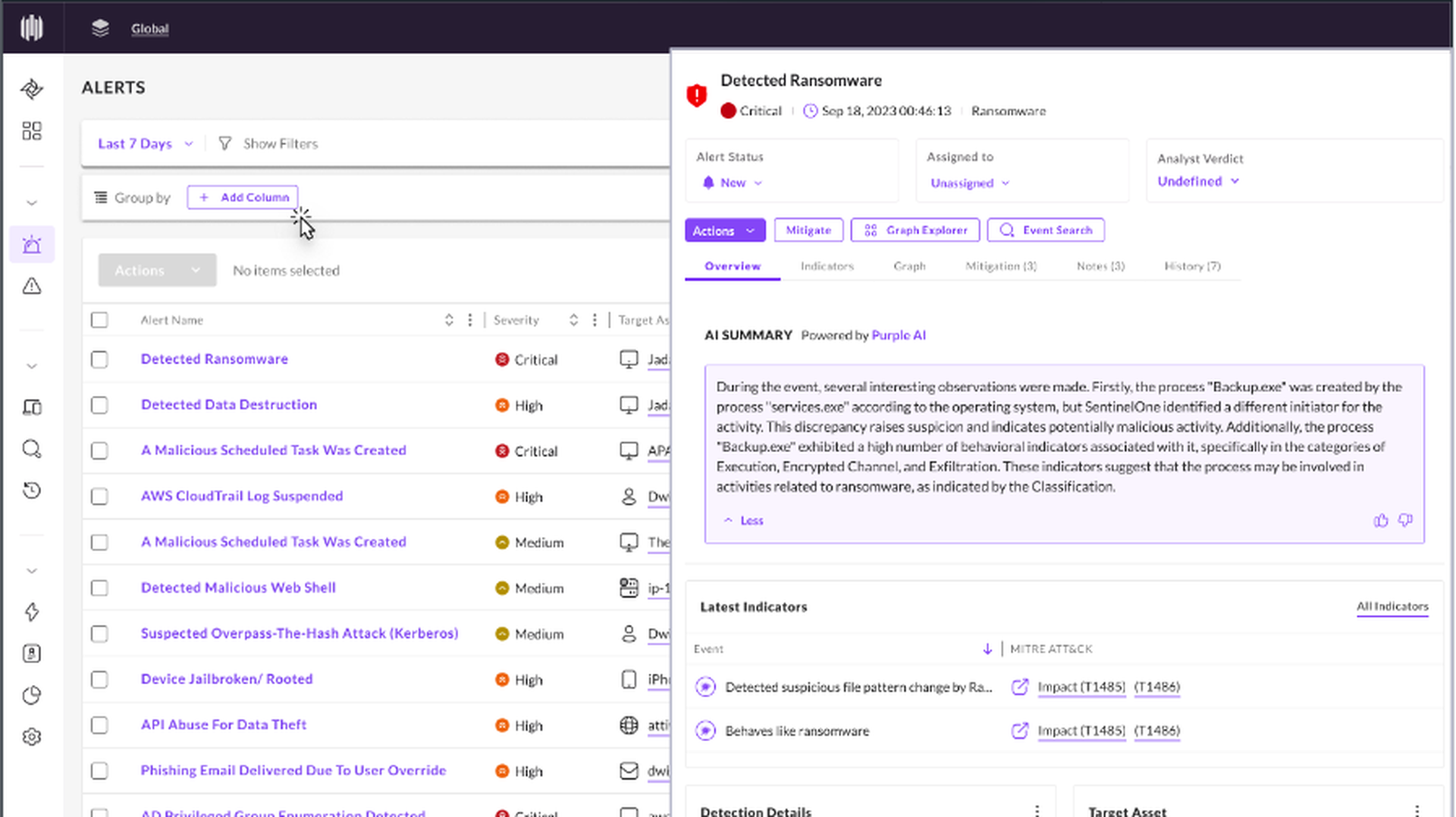
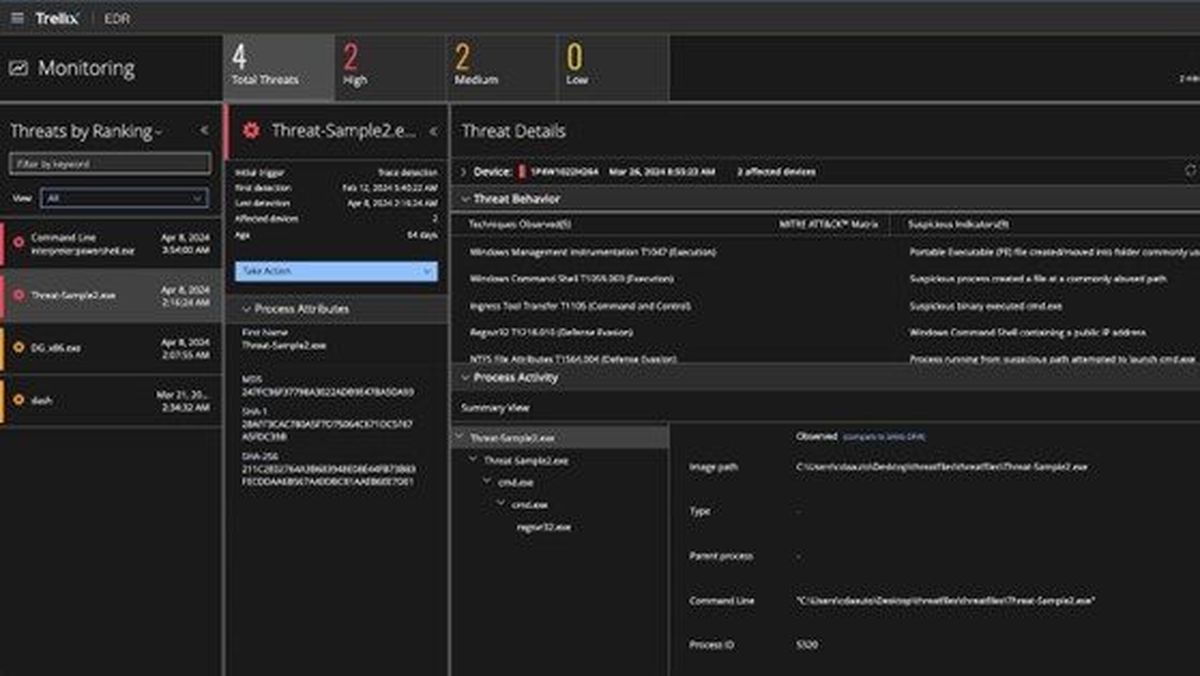
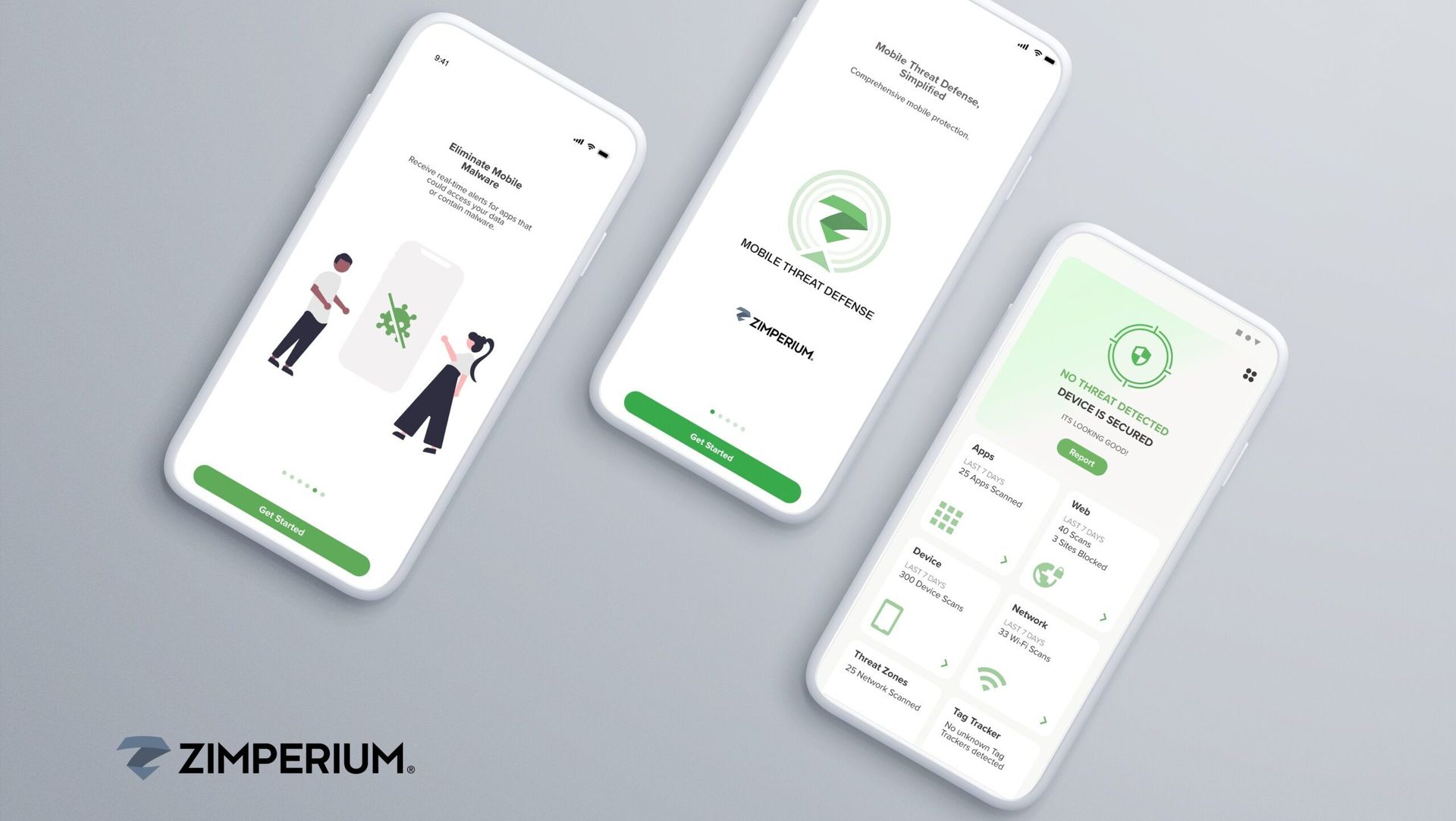
Endpoint devices with applications are increasingly exchanging data on corporate networks. Examples for this broad category include employee laptops, handsets, tablets and also IoT devices such as security systems, cameras, and virtual machines. Products named here focus on the collapsing network perimeter and those devices that have direct or indirect access to corporate resources. Each of these devices require strong endpoint security and point-to-point encryption. Security can be for data-at-rest in the device itself, secure access to data in the enterprise, and encryption for data-in-motion between the enterprise and the device. It also includes anything from hard disk encryption and tools that track lost mobile devices to USB/thumb drive security products.
Related Terms
Anti-MalwareAntivirus SoftwareBring Your Own Device (BYOD)Ephemeral PortExtranetEndpoint SecurityFirmwareKeyloggerRegistryGet daily email updates
SC Media's daily must-read of the most current and pressing daily news