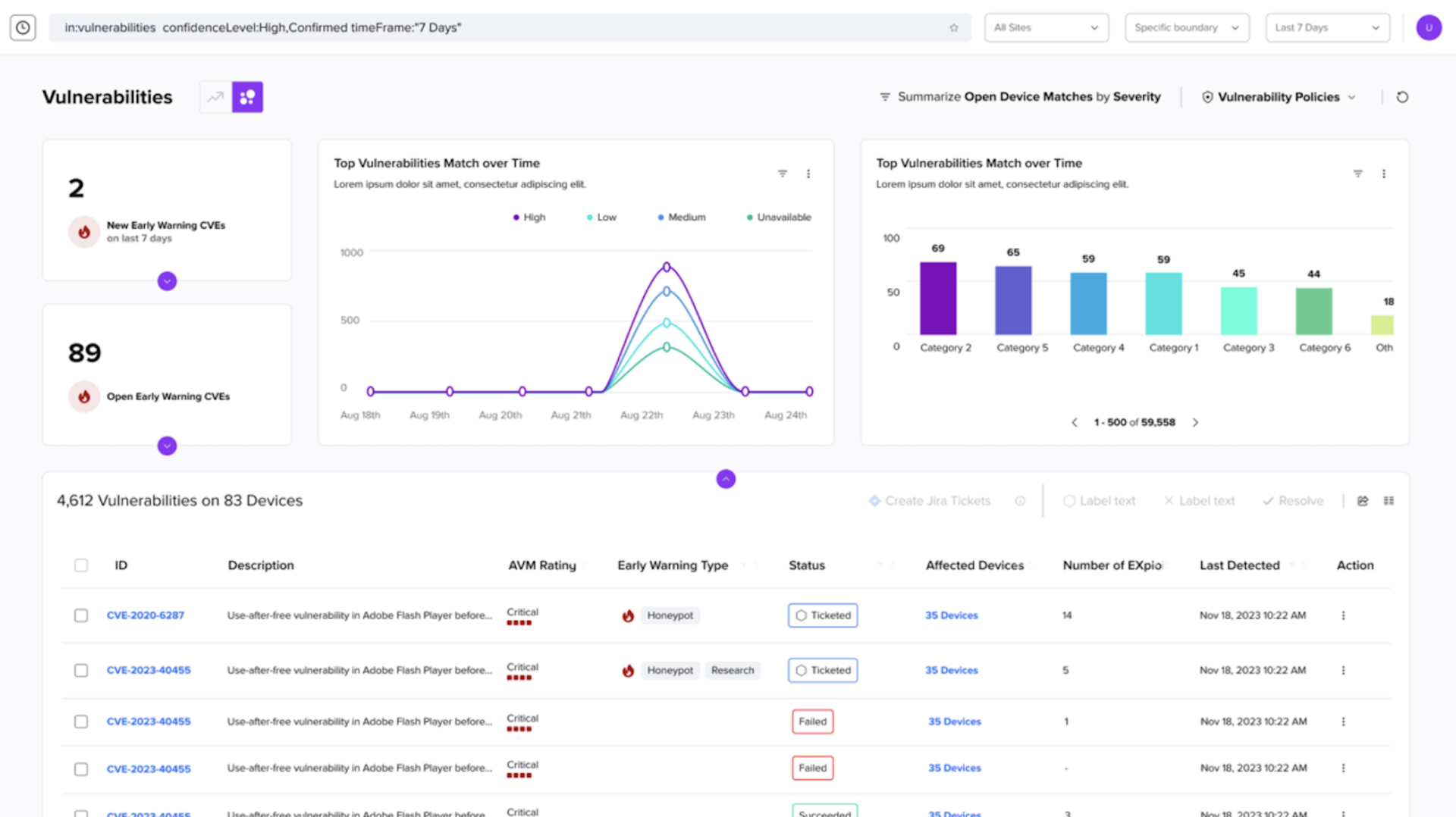
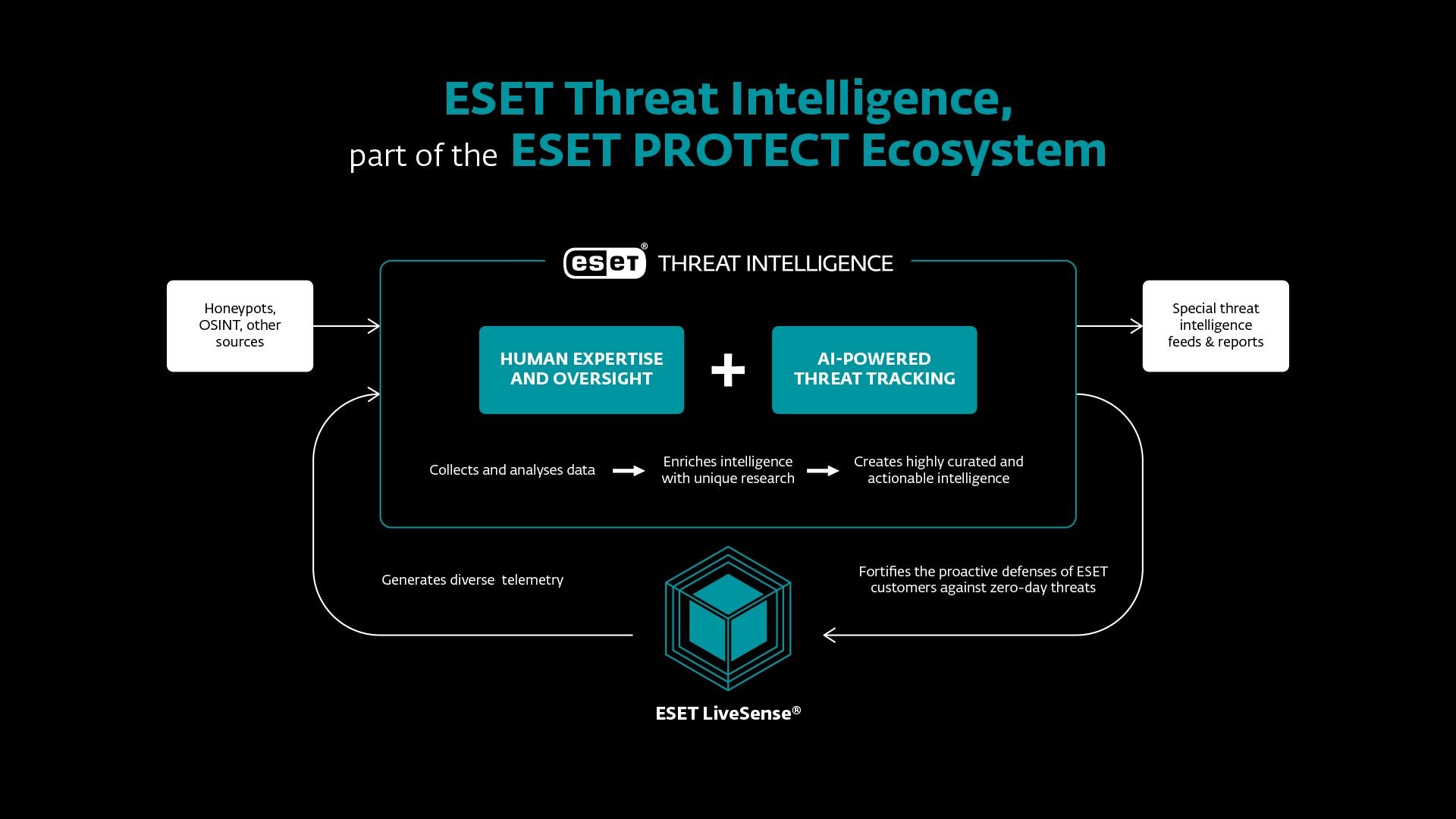
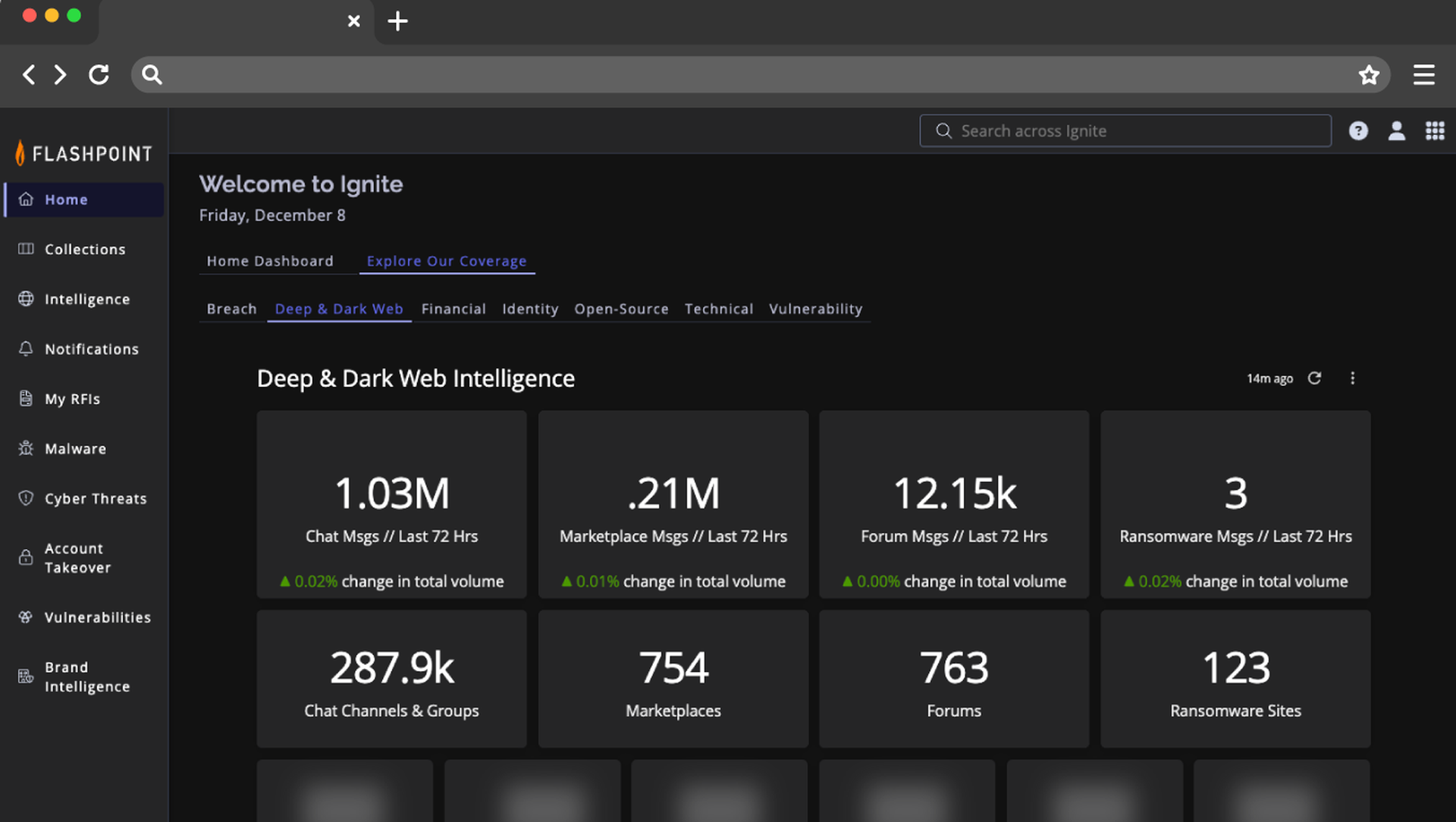
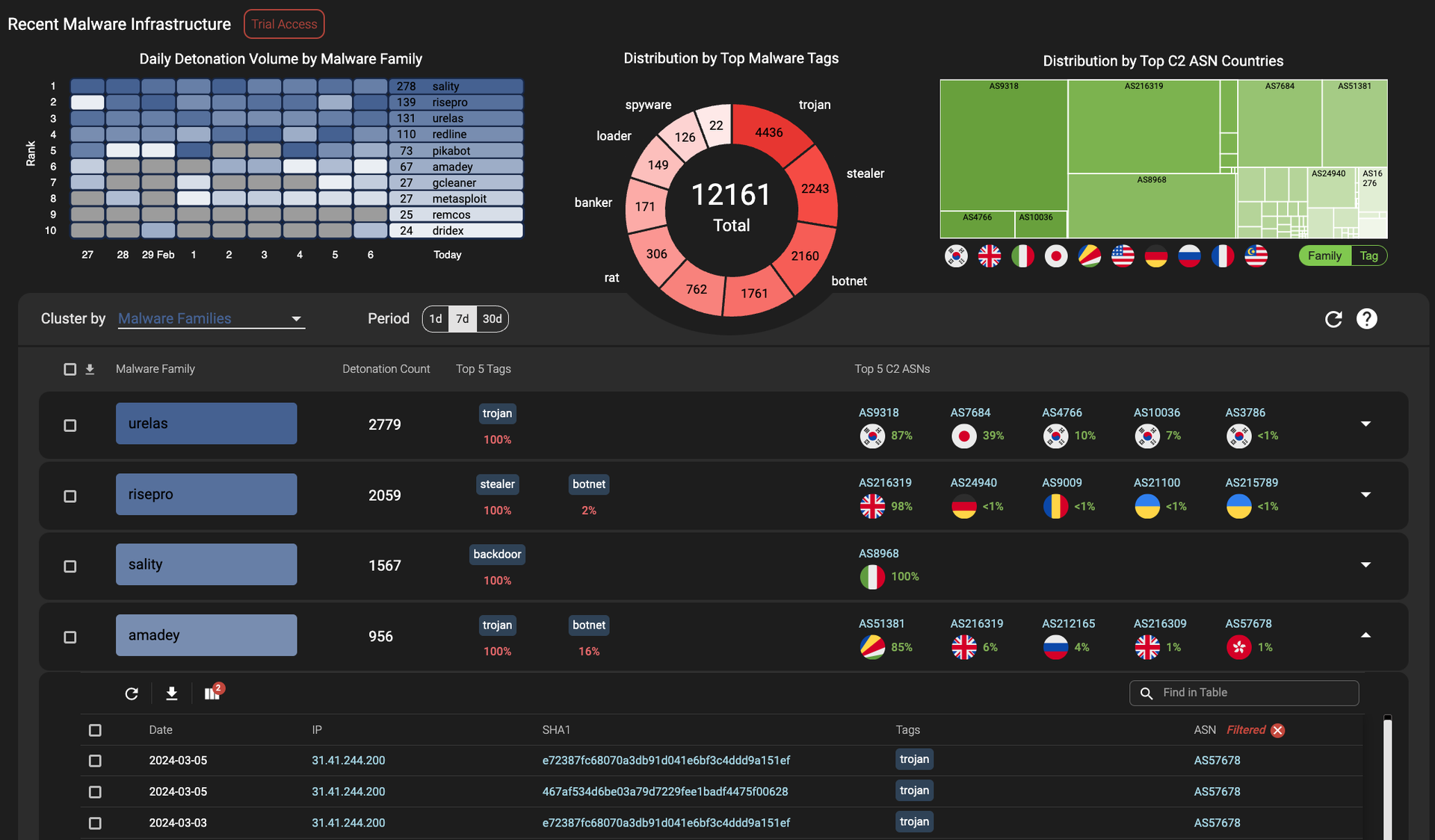
Products named in this category help cybersecurity teams research and analyze cybercrime and other threat trends and any technical developments made by those engaging in cyber-criminal activity against both private and public entities. These technologies facilitate the understanding and contextual relevance of various types of data, often an overwhelming amount, collected from internal network devices, as well as from external sources, such as open source tools, social media platforms, and the dark web. Armed with these more digestible analyses on risks and cyberthreats, cybersecurity teams use these tools to enhance their tactical plans preparing for and reacting to an infrastructure intrusion prior to, during and after an attack, ultimately improving their overall security posture so the long-term security strategy is more predictive rather than simply reactive.
Related Events
Related Terms
BotnetCovert ChannelsDNS SpoofingData MiningDeauthentication AttackDeepfakeDictionary AttackDisruptionDistributed ScansDrive-by DownloadGet daily email updates
SC Media's daily must-read of the most current and pressing daily news