Business email compromise or impersonation attacks overall rose during the second quarter of 2019 by 25 percent with some types of attacks becoming more common and better executed.
During this period FireEye has noted attackers are increasingly impersonating executives and attempting to involve a company’s supply chain vendors as part of the attack to make it appear as if the malicious email is a legitimate request. These tactics have been honed to a point where they are easily convincing employees to take the bait.
Some of the steps being taken have been used in the past, such as spoofing the return address, but FireEye found the attackers are doing more research on their victim to better tailor the attack.
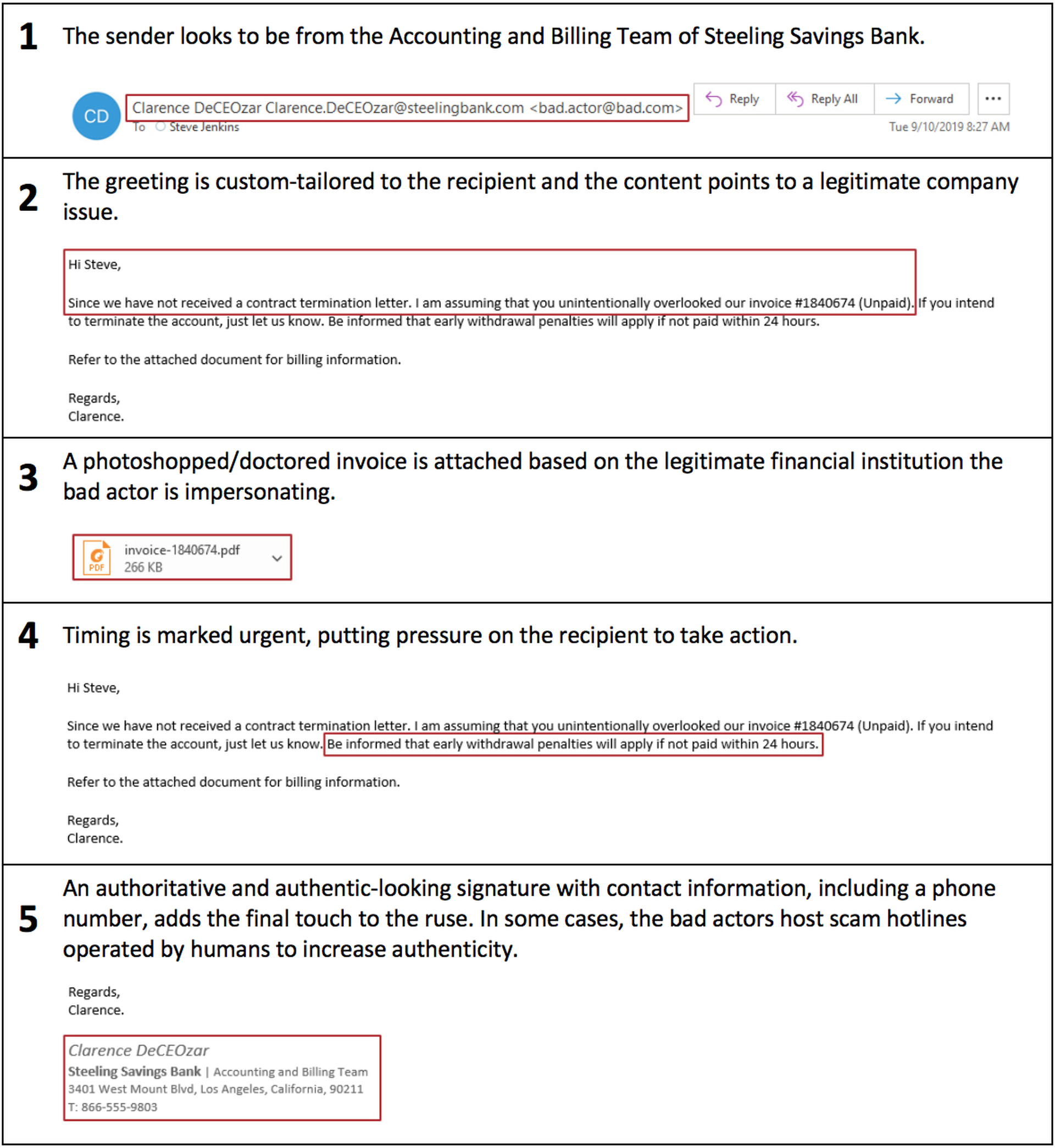
This includes creating a greeting aimed at a specific recipient at the targeted company and using a doctored version of a real company invoice that is then attached to the email. To place more pressure on the employee the email is marked urgent and to cap it off the signature, purportedly from the company exec, is added that includes name, phone number, email and address all of which are real.
Despite the increased believability being built into these scams, there are methods making them detectable. Worker education remains the first line of defense with employees being taught to double check with the person supposedly asking for the payment before completing the transaction. Implementing social graph impersonation filtering and improved identification of suspicious email activity can also be used with a high level of success.



