The U.S. Cybersecurity & Infrastructure Security Agency (CISA) released a free and open-source tool to help defenders map adversary behavior to the MITRE ATT&CK framework.
The tool, named Decider, simplifies the mapping process by asking users guided questions about adversary activity using minimal technical language and helping them determine the correct tactics, techniques or subtechnique.
The ATT&CK framework is a globally accessible knowledge base and model documenting attacker tactics and techniques based on real-world observations. It categorizes different adversary tactics and details them for defenders to develop effective detection and mitigation strategies accordingly.
While ATT&CK is increasingly used for enterprise cybersecurity, CISA found mapping ATT&CK involves many intricacies that “are important to get right and easy to get wrong.”
“Many stakeholders communicated that they either did not know how to start mapping to ATT&CK, or they were unsure if they were accurately mapping adversary behavior,” said CISA.
CISA developed Decider to help defenders with the process.
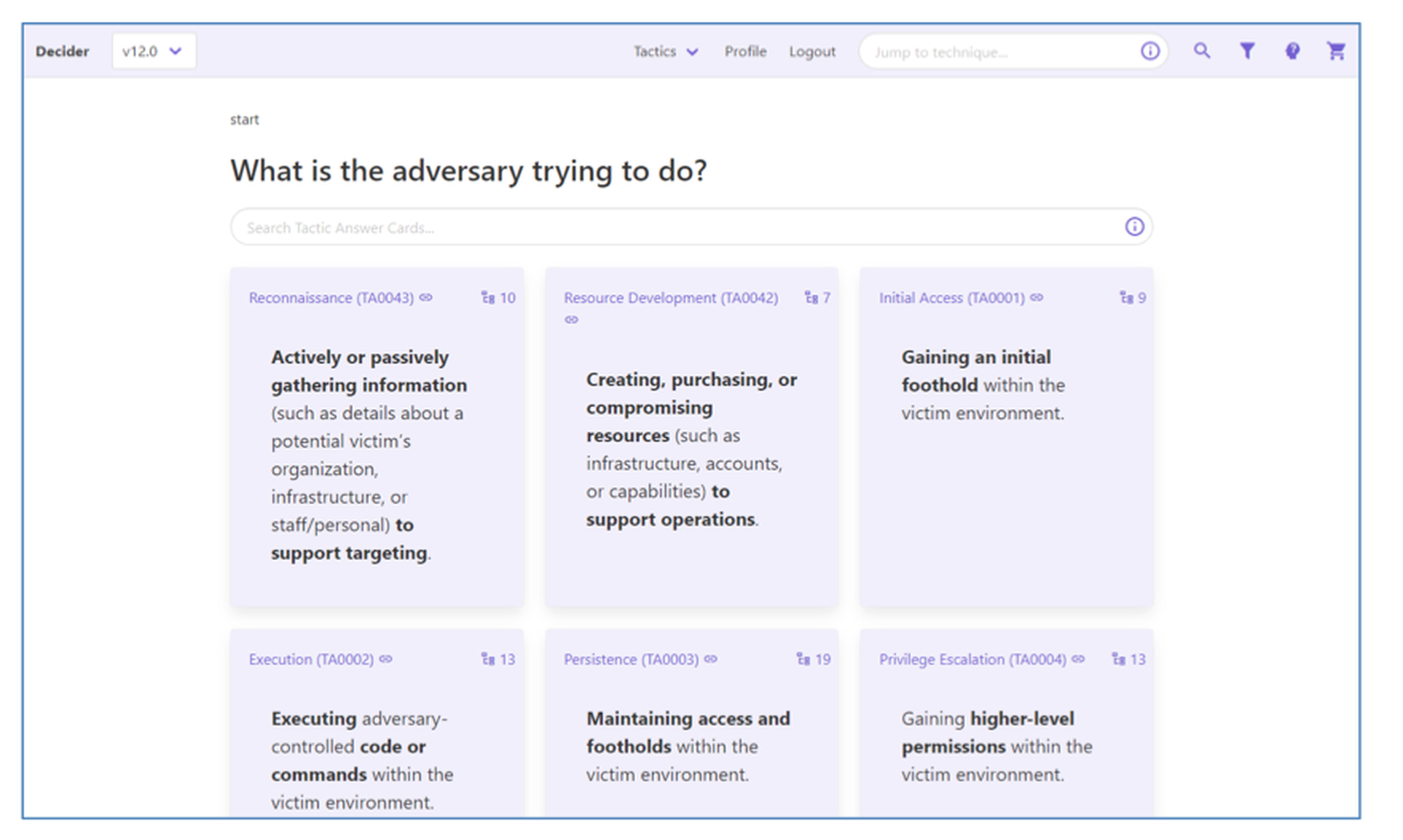
In the main workflow, Decider asks a series of guided questions in a decision tree format. Answering these questions will guide users into tactics, techniques, and subtechniques until a mapping is completed.
For example, the question might be, “What is the adversary attempting to achieve?” And a potential answer could be “gaining an initial foothold within the victim environment,” which aligns with the Initial Access tactic.
The Decider will proceed to pose additional relevant questions until users reach a subtechnique, if none is applicable, a technique.
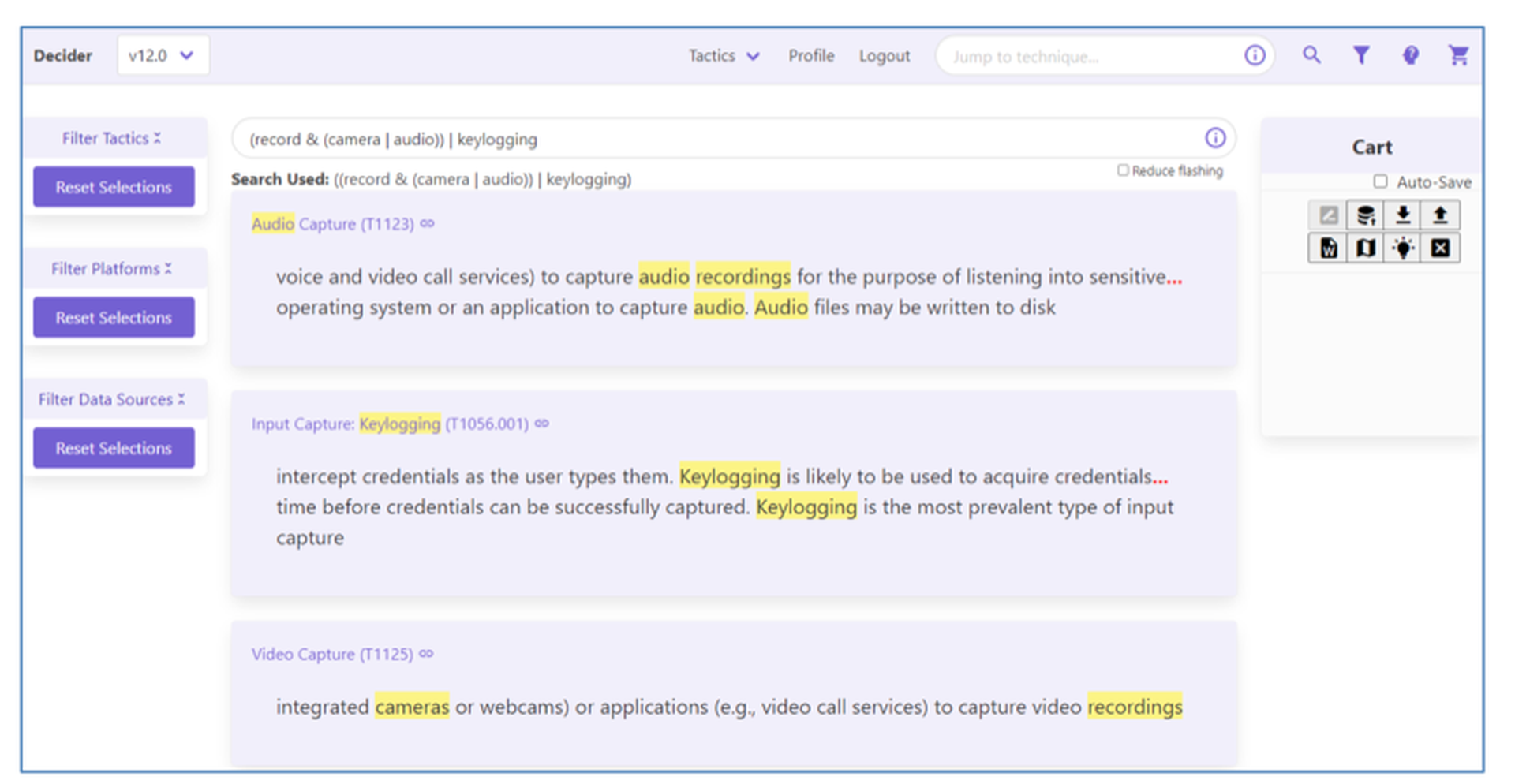
The tool’s search function also allows users to directly access a technique and subtechnique if the main workflow fails to present the correct technique or the user has already identified the technique used.
John Bambenek, principal threat hunter at Netenrich, said the open tooling like Decider gets the industry close to “the promised land of normalized attack information.”
“Everyone has slight differences in how they map the same behavior. With a standardized framework, everyone can describe the same attacks in the same way,” Bambenek said.
“The tool enables analysts to leverage a consistent, framework-backed triage, and response process,” added Justin Edgar, AVP of security strategy at Deepwatch.
Developed in partnership with the Homeland Security System Engineering and Development Institute and MITRE, the tool is now available for download on CISA’s GitHub repository.
It is a web application that must be hosted before using it and is currently compatible with Enterprise ATT&CK versions 11.0 and 12.0.