Vendor: Deceptive Bytes
Price: $40 per endpoint, per year
Contact: www.deceptivebytes.com
Quick Read
What it does: Deceptive Bytes Active Endpoint Detection uses existing IT infrastructures to respond to changing advanced threat landscapes and interfere with malicious attempts to carry out reconnaissance and takeover missions.
What we liked: We found this an effective, prevention-focused product that’s easy to operate, understand, and manage. Pinpoint decision-making and dynamic deception allows for the seamless operation and cohesion with other security tools, reduces operational costs, and improves employee productivity, all of which then increase the product’s overall value.
Security pros will find Deceptive Bytes Active Endpoint Deception an endpoint-centric platform that uses existing IT infrastructures so it can respond to changing advanced threat landscapes and interfere with malicious attempts to carry out reconnaissance and takeover missions. This product makes an environment look unattractive and hostile to adversaries, reducing hacker motivation and minimizing the chances of infection.
Malware threats are clever and evasive. Before it even begins to attack, it scans an environment to gain a baseline understanding of the layout and of any protective measures in place. It uses this information to craft an approach of defensive and evasive techniques, but in doing so, it also unwittingly alerts Deceptive Bytes to its presence and activates the very measures that Deceptive Bytes will then use against it. Deceptive Bytes can shape the decisions that an adversary makes and then beat it at its own game.
The product’s preemptive defense gives an environment the appearance of a hostile environment. Such an environment looks unattractive to malware. Thus, the Deceptive Bytes façade reduces attack motivation and therefore the chances of infection. Still, whenever an intrusion does occur, the proactive defense engages immediately and dynamically responds to evolving threats anywhere in the kill chain. Legitimate processes are automatically whitelisted, and Deceptive Bytes triggers different, real-time, and automated responses, based on the stage of detection, in the hopes of altering the outcome of attacks. Together, the preemptive and proactive capabilities of the platform close security gaps and stop unknown and sophisticated attacks that other security products often cannot detect, all with a very low false positive alert rate.
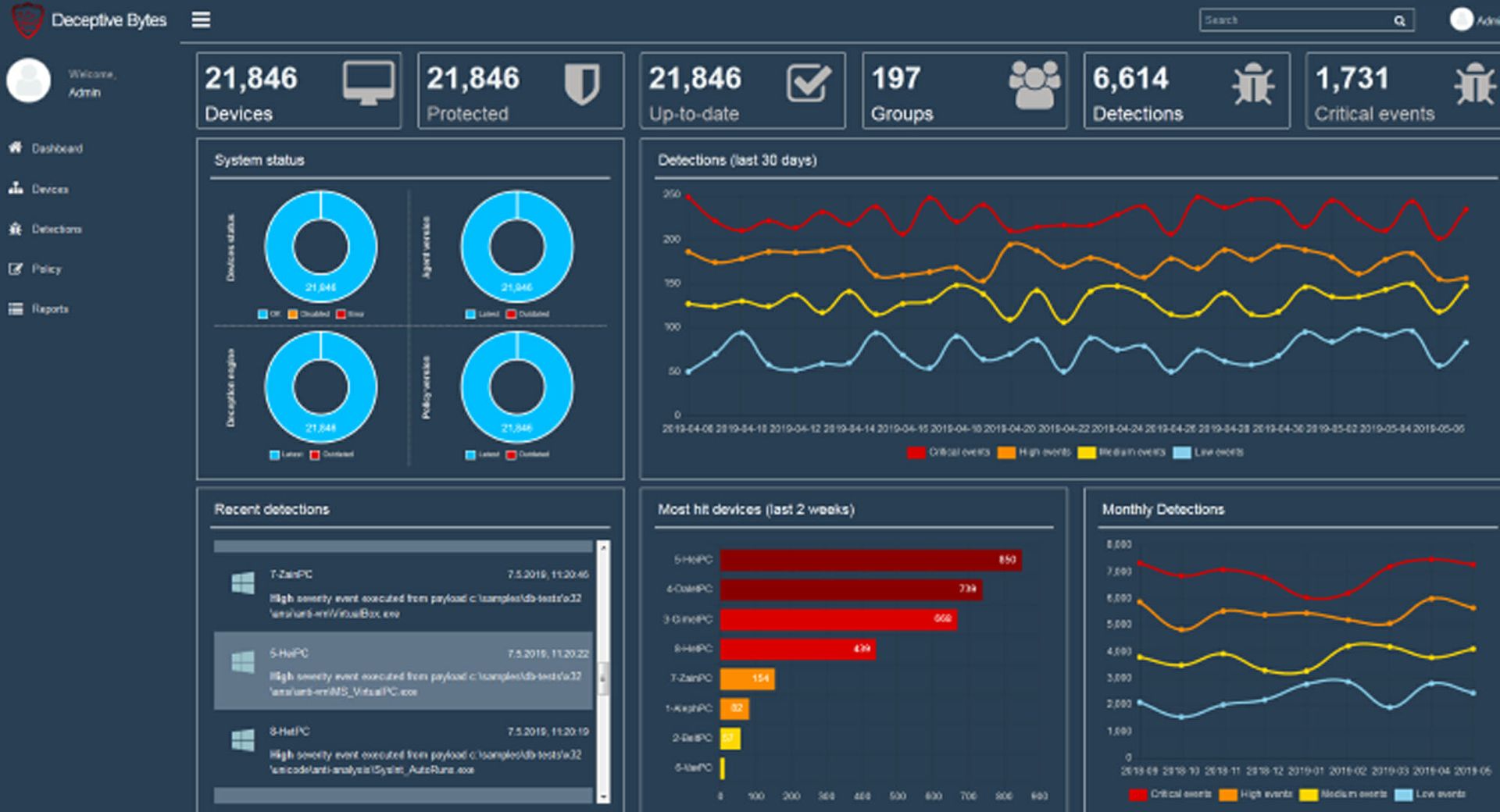
The main dashboard shows helpful, high-level information on an environment, such as system status and a list of all the detections the product has made in the last 30 days. Delving into the detections page shows even more details regarding these detections and other related information, including indicators of compromise, hashes, and execution specifics. These details highlight all the system objects the intrusions may have impacted. The detections are also searchable, making investigation easy and efficient.
The devices page lets administrators manage all endpoints from a centralized location and delivers visibility into, and remote control of, the agents. Deceptive Bytes also integrates with Active Directory, which lets administrators pull all device and personnel information from Active Directory directly into a management console. Security teams may even remotely view the endpoints with live forensics to see file systems, registry details and more on the endpoint.
Overall, security pros will find Deceptive Bytes Active Endpoint Deception an effective, prevention-focused solution that’s easy to operate, understand, and manage. Deceptive Bytes operates only from user-mode, keeping systems closed to potential vulnerabilities and preventing them from becoming points of failure. We found the coverage of the single agent multi-factorial, conducting everything from deception to event logging and operating only when necessary, resulting in a very low operational burden and highly dynamic deception. This pinpoint decision-making allows for seamless operation and cohesion with other security tools, reduces operational costs, and improves employee productivity, all of which then increase the product’s overall value.
Pricing runs at $40 per endpoint, per year and includes 24/7 support.